Sensor Tower VPN Apps Collect all Traffic Data on People’s Phones
- VPN tools developed by “Sensor Tower” plant root certificates that enable the monitoring of all traffic.
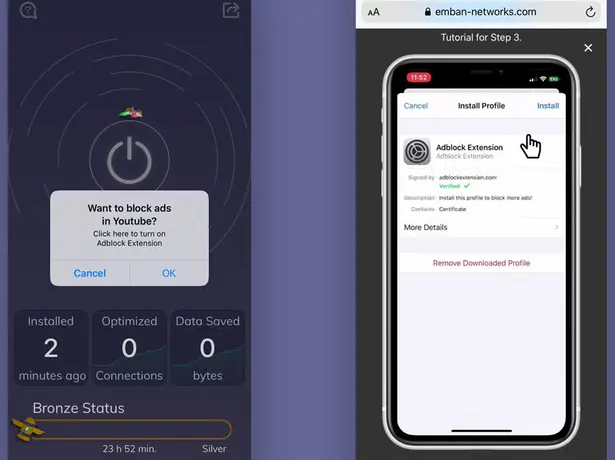
- Users are tricked into approving the installation of the certificates by getting redirected on an external webpage.
- Sensor Tower says they’re doing nothing wrong and only collect anonymized user data for analytics.
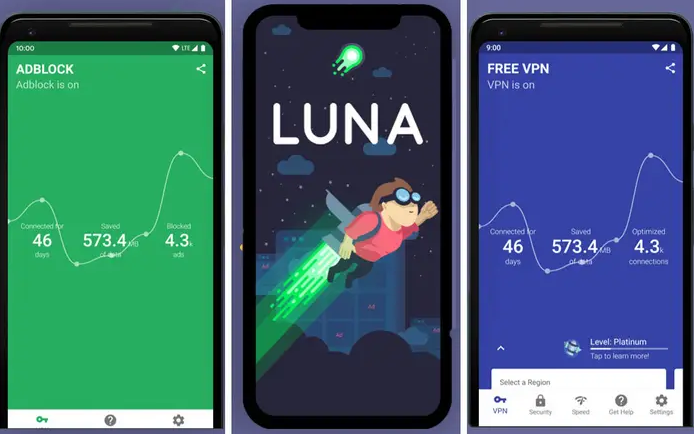
According to a report based on a BuzzFeed News investigation, popular mobile apps made by "Sensor Tower" are collecting all traffic data that passes through the user’s phone. This includes “Luna VPN”, “Free and Unlimited VPN”, “Mobile Data”, and “Adblock Focus”. Apple and Google have already removed some of the 20 apps that belong to Sensor Tower, and it’s possible that more apps will be ousted as their internal investigation continues. As for the developer, Sensor Tower responded by admitting that their apps collect some user data, but stated that it’s entirely anonymized and used solely for analytics.
Source: BuzzFeed News
Sensor Tower is specialized in mobile app store marketing intelligence, so collecting and analyzing data is basically what they’re in business for. Their insights have previously helped identify other risky apps on the App Store. Their twenty apps have more than 35 million downloads, and many of them are following the suspicious practice of asking the user to install a root certificate on the device. Usually, these small encryption keys are meant to help verify users when they attempt to access secure data or networks. Oftentimes though, they enable the signing/trusty authority to gain full access on the device, which is a pretty risky thing to accept.
The users of the above apps would typically assume that blocking ads or connecting to VPN networks would require the use of CA certificates, but this shouldn’t be necessarily the case. Both Apple and Google are strict with how they handle root certificate privileges, as this constitutes a significant security risk to the users. This is why the "Sensor Tower" apps prompt the users to install the required certificate by redirecting them on an external webpage right after they install one of their apps. If you want to check what root certificates run on your device and disable the ones that seem suspicious, go to “Settings” / “Security” / “Advanced” / “Encryption & Credentials” / “Trusted Credentials”.
Source: BuzzFeed News
We can’t accuse Sensor Tower of misusing the collected data or rule out the possibility of anonymizing it. However, the way they go around Android’s and iOS’ protections to have their CA certificates planted on the user device isn’t nice, and it’s done on the verge of deception. Still, the analytics company insists that they do not track, request, or store any sensitive user data such as usernames or passwords and that the people’s web browsing data remains completely private and untouched.