Security Advisory From F5 Calls for Urgent Patching for BIG-IP Admins
- F5 has released patches for two of its products, addressing a total of seven vulnerabilities.
- The flaws are in their majority critical, and two of them have published proof of concept code.
- There are no mitigations available yet, so patching is the only way to safety.
F5 has discovered four critical and two high and one medium-severity flaw affecting its BIG-IP and BIG-IQ products. Because of the wide scope of the problems and also the extensive affection, the company has released a detailed security advisory so important that even CISA has caught it and published its own notice to point admins there.
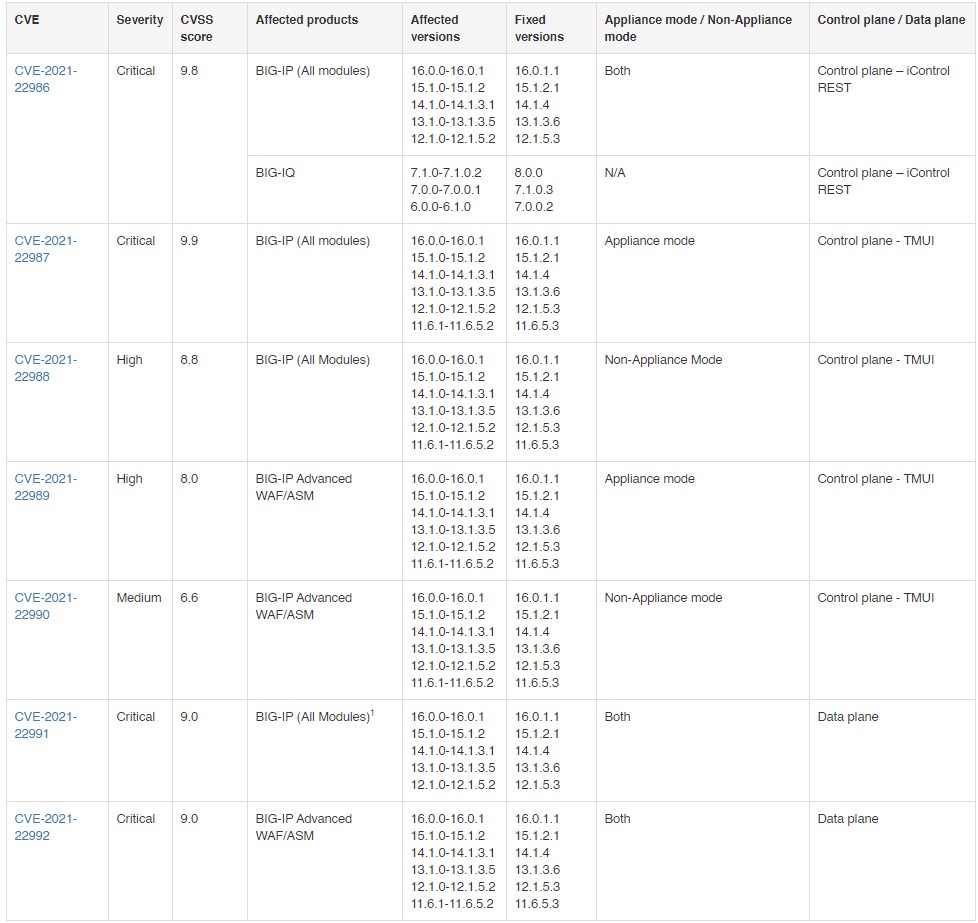
The seven vulnerabilities found and patched are the following:
- CVE-2021-22986: Unauthenticated remote command execution vulnerability in the iControl REST interface, CVSS score 9.8
- CVE-2021-22987: Authenticated remote command execution vulnerability in undisclosed pages of the Traffic Management User Interface (TMUI), CVSS score 9.9
- CVE-2021-22988: Authenticated remote command execution vulnerability in undisclosed pages of the Traffic Management User Interface (TMUI), CVSS score 8.8
- CVE-2021-22989: Authenticated remote command execution vulnerability in undisclosed pages of the Traffic Management User Interface (TMUI) when running in Appliance mode with Advanced WAF or BIG-IP ASM provisioned, CVSS score 8.0
- CVE-2021-22990: Authenticated remote command execution vulnerability in undisclosed pages of the Traffic Management User Interface (TMUI) when running in Appliance mode with Advanced WAF or BIG-IP ASM provisioned, CVSS score 6.6
- CVE-2021-22991: RCE or URL-based access control flaw or DoS-inducing buffer overflow vulnerability in the Traffic Management Microkernel (TMM), CVSS score 9.0
- CVE-2021-22992: RCE or buffer overflow resulting in DoS, triggered through a malicious HTTP response to an Advanced WAF/BIG-IP ASM virtual server, CVSS score 9.0
The above flaws are addressed in BIG-IP versions 16.0.1.1, 15.1.2.1, 14.1.4, 13.1.3.6, 12.1.5.3, and 11.6.5.3, while for BIG-IQ, which is only affected by CVE-2021-22986, the fixes come through 8.0.0, 7.1.0.3, and 7.0.0.2.
Everyone is advised to apply the patches immediately, as they all have serious potential for malicious exploitation. Unfortunately, there are no mitigations to use by those who can’t patch for the time being.
Google project zero researchers have a PoC for CVE-2021-22991 and also for CVE-2021-22992, which were now published as the vendor has fixed them. This obviously makes the patching even more imminent for system administrators, so go ahead and do it right now.