The Sea Turtle DNS Hijackers Enter Greek and US Waters
- The Greek domain name registrar got hit by the Sea Turtle actors, but the level of compromise remains unknown.
- The actors retained access to the systems for five days after the organization noticed the problem.
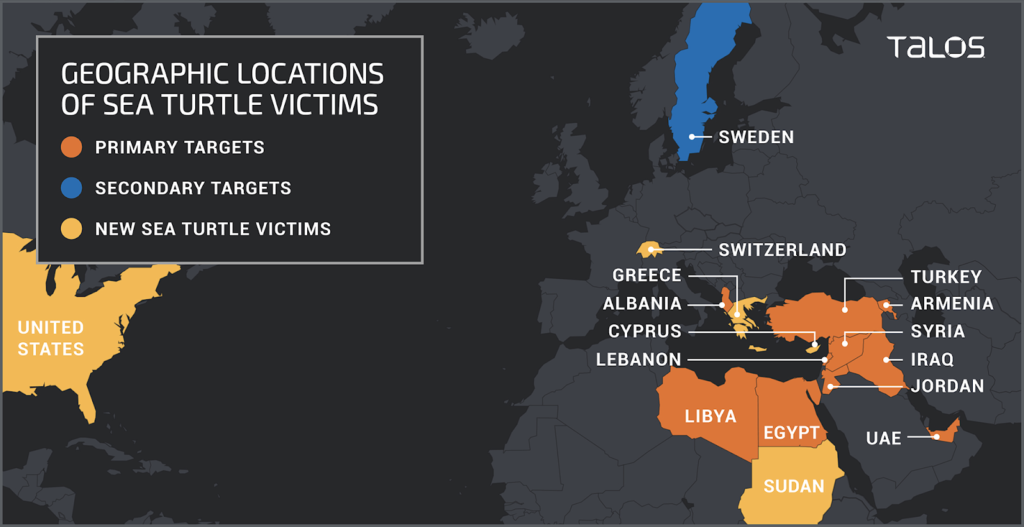
- Sea Turtle continues to roam and enter new waters in the USA, Sudan, and Switzerland as well.
Back in April, we discussed how state-sponsored DNS hijacking campaigns called “Sea Turtle” constituted a risk to the global DNS system, as trusting the backbone of the internet is key to keeping the economy going. The actors were targeting government organizations, energy companies, and transportation agencies in North Africa and the Middle East, but as Cisco Talos researchers warned, it would be only a matter of time before the attackers extended their operations to target more countries. As it seems, this time has now come, and Sea Turtle is now swimming the waters of the United States, Greece, Switzerland, and Sudan.
image source: blog.talosintelligence.com
As reported by the Greek news outlet techblog.gr, the National Institute of Computer Science of the Foundation for Research and Technology (ICS), which is the management entity for domain codes “.gr” and “.el”, has suffered a DNS hijacking attack. What this means is that part of the traffic was redirected from reaching the intended servers to the Sea Turtle clone servers. The purpose of this is to carry out man-in-the-middle attacks, steal sensitive information like login credentials, or spy on email communications. The fact that the attacks focused on governmental agencies indicates that the actors were after crucial data and not just money.
The Greek registrar proceeded to the resetting of the domain owners’ login credentials and promised to continue operating as per the ISO-27001:2013 standard requirements. In spite of these measures, Cisco reports that the Sea Turtle actors retained their access to the hijacked infrastructure for five days after ICS identified and disclosed the attack. The level of compromise cannot be determined at this point, as no further details regarding this incident were revealed. The same ambiguity shrouds the other operations of Sea Turtle, on Sudan, USA, and Switzerland.
Cisco is once again proposing several mitigation measures, as Sea Turtle should be stopped before the disruption becomes too big to overcome and the trust to DNS is irreversibly shaken. The proposals include multifactor authentication for the management of DNS, registry lock service for the domain names, DNSSEC signing and validation, IMAP access through VPN, frequent network-wide password resets, and constant passive DNS record monitoring. While the Cisco researchers won’t make any guesses as to who is behind Sea Turtle, other security experts believe it is the Iranian government which sponsors the attacks.
Have something to say on the above? Feel free to write us your comment in the section beneath, or join the discussion on our socials, on Facebook and Twitter.