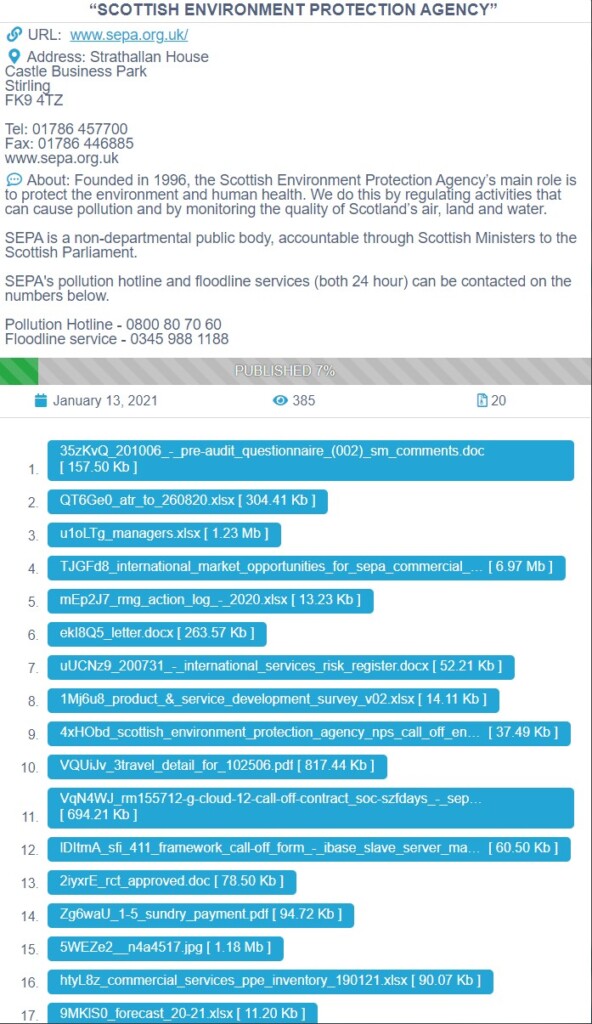
The Scottish Environment Protection Agency Was Hit by Ransomware
- The Scottish Environment Protection Agency (SEPA) was compromised by the Conti group almost a month ago.
- The ransomware gang is now leaking part of the stolen data, which appears to concern non-critical stuff.
- The agency’s most critical systems are operational, but full recovery will take a while.
The Scottish Environment Protection Agency (SEPA) has been hit by ransomware actors, and more specifically, the Conti group. The cyber-attack took place on Christmas Eve, but the organization hasn’t recovered yet.
Moreover, the actors have stolen 1.2 GB of data, as confirmed by SEPA and as seen on Conti’s data leak portal, where the actors published 7% of the data on Thursday. The stolen data mostly concerns information about SEPA’s stuff, letters, contracts, service logs, and forecast details, enforcement notices, so there’s nothing extremely critical in the set of 4,000 files stolen by the hackers.
SEPA’s employees are having big operational problems as a result, though, and have lost access to basic systems like their email platform. Thankfully, critical and important services such as the flood-warning system remain unaffected, so people in Scotland will still get warnings if needed.
Pollution reporting, which is another aspect of SEPA’s mission, is partially operational, though, as this relied upon online submissions of incidents and is now taken over to phone lines. All in all, the non-departmental public body has a lot of work to do until its systems are fully recovered, as Chief Executive Terry A’Hearn also confirmed.
SEPA will adjust to the new conditions and will continue to fulfill its environmental-protection role. In the meantime, investigations from contracted cyber-security experts, the Police Scotland, and the National Cyber Security Centre will attempt to evaluate the stolen data and the legal implications of the data leak.
From a regulatory and operational perspective, the situation is somewhat complex, but we do not expect to see Conti receiving any money this time. It took SEPA a while to admit this attack, but now that it’s public, they won’t be able to negotiate ransom payments.
Regulated SEPA businesses and supply chain partners will soon have access to a dedicated data loss support website. However, there’s still a question mark above who were affected by the incident. SEPA stated that it would be inappropriate to provide more specific detail of the investigations and their findings thus far, but they did promise to publish updates in the next couple of weeks.