Scammers Trying to Gain Account Data Through Semrush Brand Impersonation
- Semrush has been targeted by scammers in malvertising campaigns posing a risk to account holders’ personal data
- Researchers found duplicate Semrush web pages reflecting on Google search results
- Several domains impersonating the marketing tool have been created to trick users
The Software-as-a-Service platform Semrush which offers digital marketing services has been leveraged in a malicious campaign. This scam is linked to previous malvertising attempts via Google ads that reflect impersonating web pages of legitimate sites.
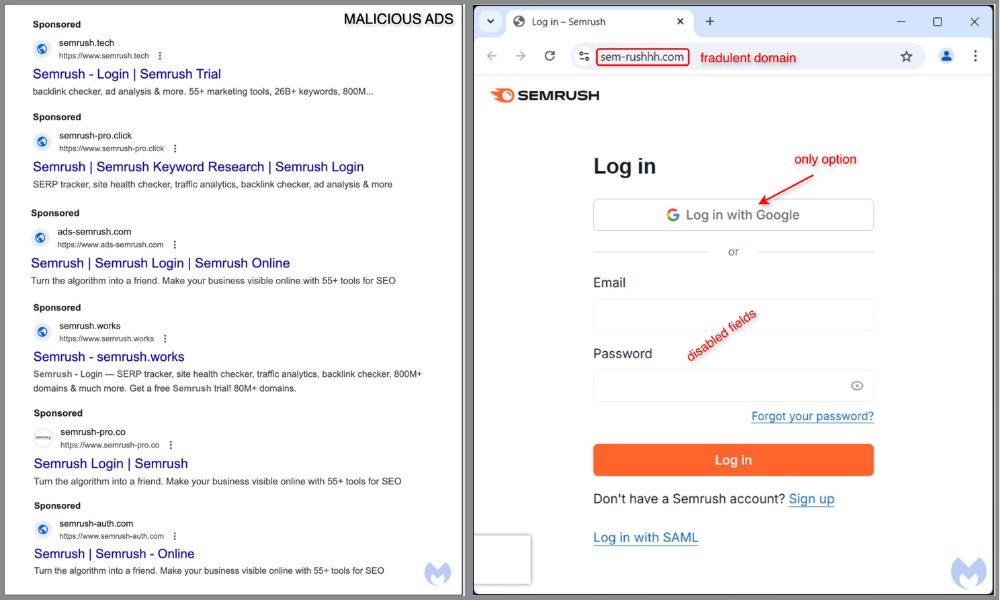
Several fraudulent websites impersonating Semrush were found on Google search results as shown in the image above. They take users to fake Semrush and Google login pages. Such websites are designed to steal the username and password of unsuspecting users.
The fraudulent domain to the right was spelled with a triple h, 'sem-rushhh.com'. It is common for scammers to create URLs with a few extra letters added to known brand names to trick users.
While the phishing site mentioned different methods of logging in, only ‘Log in with Google’ was enabled exposing the scammers' motive to steal Google account credentials.
Researchers found the following fraudulent domains impersonating Semrush:
- adsense-word[.]com
- auth[.]semrush[.]help
- sem-russhh[.]com
- sem-rushhh[.]com
- sem-rushh[.]com
- semrush[.]click
- semrussh[.]sbs
- semrush[.]tech
- seemruush[.]com
- semrush-auth[.]com
- auth.seem-rush[.]com
- ads-semrush[.]com
- semrush-pro[.]co
- semrush-pro[.]click
- auth.sem-ruush[.]com
- semrush[.]works
Successful attempts could result in scammers getting their hands on business data including revenue, user behavior, paid ads, and other strategic information for the past several months.
They may not have to breach Semrush to gain sensitive data but only need the marketing tool users to reach the platform via Google for both accounts. SaaS platforms request Google accounts to allow Semrush to access critical analytics and search-related information.
Elucidating further, Malwarebytes noted, “As mentioned earlier, Google Analytics and Google Search Console data is often integrated with tools like Semrush for enhanced analysis.” Once in, cybercriminals can misuse the personal data of Semrush account holders including their name, phone number, address, and the last four digits of a Visa card.
They may impersonate an employee to deceive vendors and clients to make payments or expose their infrastructure in the name of business promotions. Moreover, they may even make vishing or smishing attempts to call/ send SMS urging them to update payment data, complete KYC, or other frauds.
It is important not to access random webpages on Google search results that do not hold the correct URL of the destined website. Moreover, professionals must be watchful of brand impersonation using similar tactics for other tools or services they may use.
It is also necessary to report the same to the IT department of one’s company to alert all other users of the tool.