Scammers Tricking Rapacious Crypto-Investors With the Help of Lightshot
- A smooth scamming technique is laying bait for greedy crypto-investors who scour Lightshot.
- The trick is to upload screenshots that supposedly reveal credentials and a URL on an exchange.
- The victim goes to steal the money, but they end up losing between $50 and $100 from their own assets.
Lightshot is a widely used screenshot tool for Windows, macOS, and Linux, allowing people to capture their screen or parts of it and upload it on the tool’s cloud portal for easy sharing with others. As a report from Kaspersky details, scammers have found a way to exploit the tool to scam cryptocurrency investors, and it seems to be working very well for them.
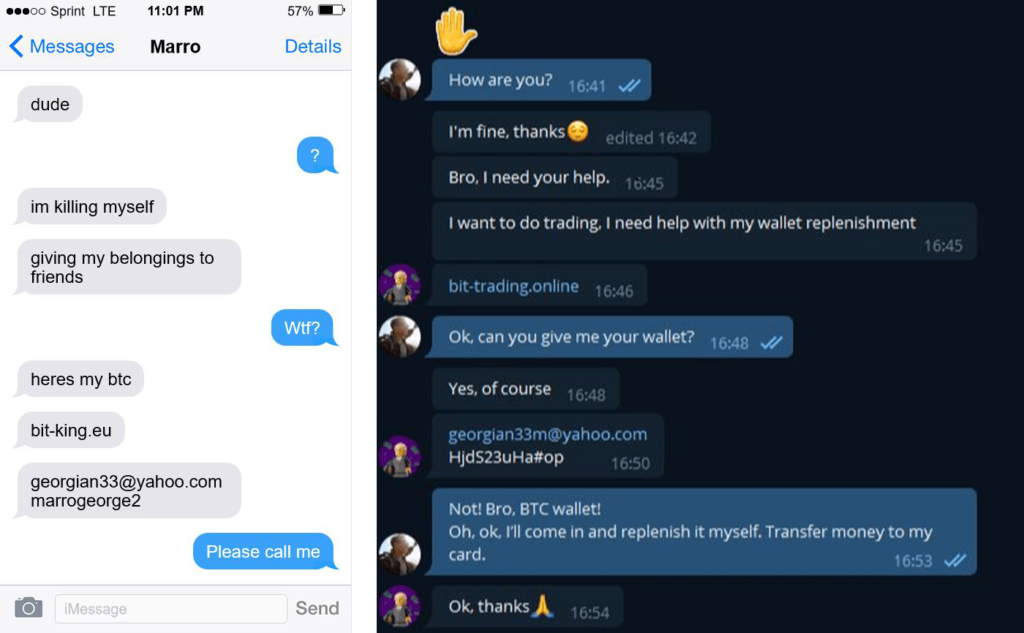
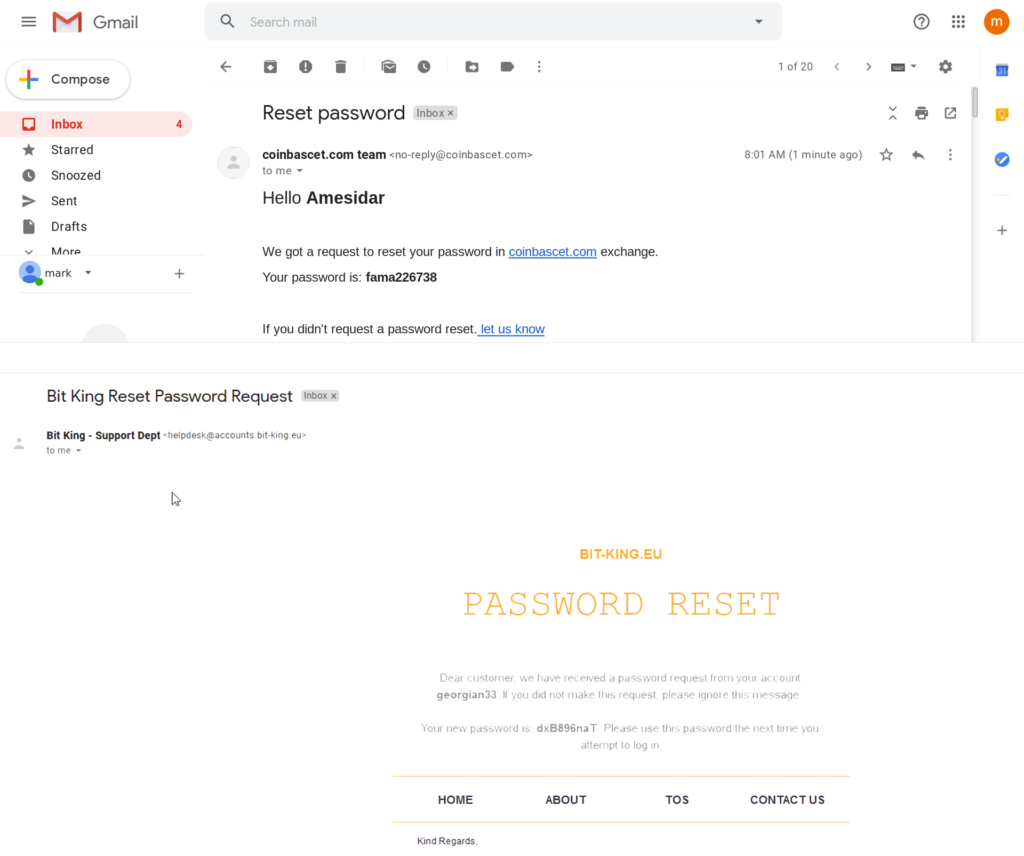
The trick is to upload “entrapping” screenshots on Lightshot’s cloud portal that appear to have been mistakenly taken and posted there. The actors typically upload password reset screenshots or IM conversations where their account credentials are supposedly given away. Other users on the Lightshot platform are seeing the images with the ostensibly sensitive info, and if they take the bait, they will follow the URL shown to grab the unfortunate user’s assets.
The URL given in these images points to a website that's made to look like a legit cryptocurrency exchange that offers a login page. If the victim enters the “stolen” credentials there, they are met with a wallet that supposedly contains 0.8 BTC (about $50,000).
The next logical step to follow would be to transfer this amount to their personal wallets, and those who attempt to do that are asked to pay a small commission in BTC, somewhere between $50 and $100. Thinking they’re about to get $50,000, the victims pay that commission, only to get nothing in return. Trying to transfer the amount again repeats the same losses, and so on.
It is an admittedly elegant scamming technique that has made the crooks about 0.1 BTC so far. Also, it has an implied sense of urgency that pushes victims to act quickly and omit all signs of fraud, as the uploader of the Lightshot image that exposed their sensitive details could realize their mistake at any moment and reset their credentials on the crypto exchange. This is automatically created by the scam's context, so the actors don’t have to do much for that part.
Taking the scammers' bait is certainly a matter of being greedy, as these users are victimized while trying to victimize someone else. As such, they had it coming, and it served them right, but it’s still a good lesson for the rest. Don’t upload stuff your capture on your computer onto cloud services, as there are hawks there scanning everything carefully. You’d better use more secure and private means to share captured screenshots directly with the person you want.