Scammers Create Spoofed PayPal Credentials with Extreme Likeness
- Researchers recently found a new way scammers are crafting PayPal emails.
- The phishing email is crafted with the URL and email address that look legitimate.
- The PayPal money laundering scheme could evade detection on the portal.
Cybercriminals are now sending malicious communications by creating nearly perfect-looking email addresses using resources that are open to all. In a recent incident, it was observed that a malicious email asking for payment through PayPal reflected a sender ID that appeared just like the official credential.
Carl Windsor, who has been working with Fortinet for over 17 years, was stumped to see a malicious email crafted to perfection. As a CISO, he found all the cyber hygiene checklists maintained in the email.
This included:
- The sender's address was to the point [service] and ended with the company name only without any extra letter, number, or character.
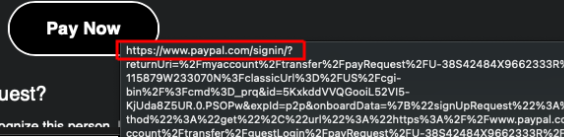
- The link in the email took the user to a genuine-looking login page of PayPal.
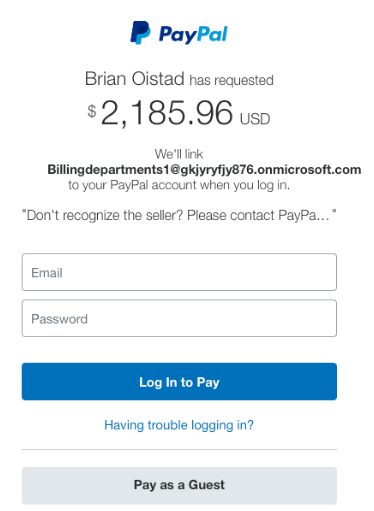
However, Carl found that the Pay Now page was programmed to link the PayPal account of the victim with another account.
Not only this, the linking of accounts was such that PayPal would readily allow transactions without detecting any malicious activity.
This tactic was possible for the threat actor using a service that is available to all for free!
This is how they did it:
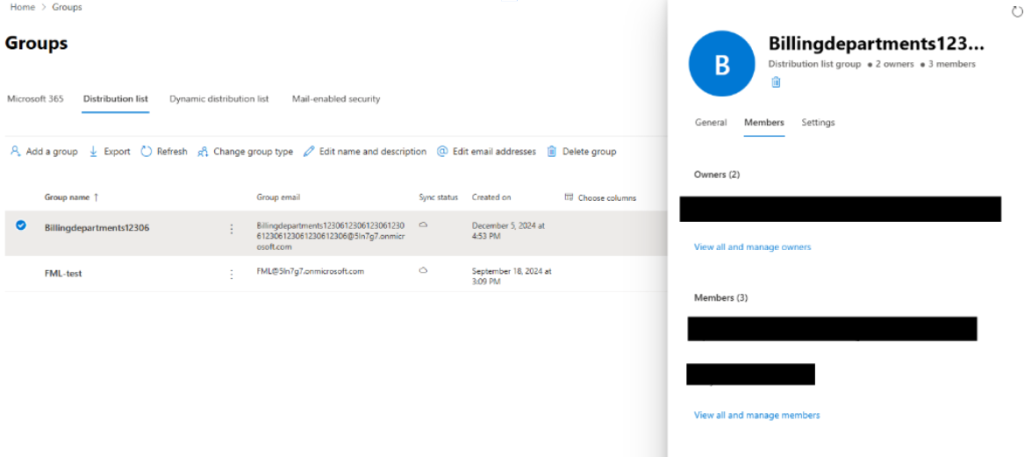
First, they registered an MS365 test domain which offers a free plan for three months. Then, they created a distribution list of targeted email addresses.
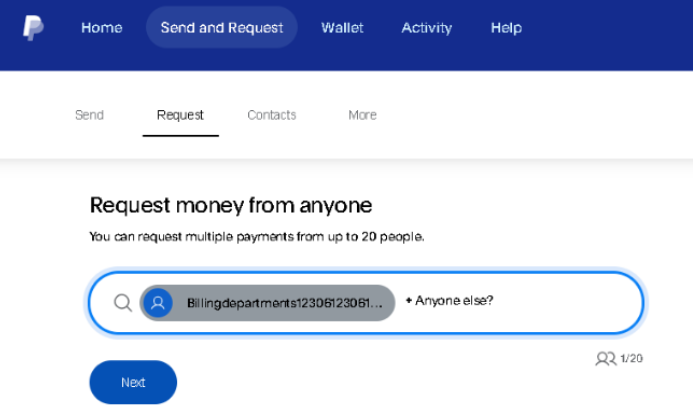
An example of this is seen in the above screenshot, “Billingdepartments1[@]gkjyryfjy876.onmicrosoft.com.”
Upon getting access to PayPal, they would simply request money and enter the receiver's email address from the distribution list.
At this stage, the victim of fraud may receive notifications of transactions. The sooner they alert the financial service, have the intruders blocked, and change their passwords, the swifter would be the procedure to curtail the cybercrime.
Looking into the details of the money laundering mechanism employed by the developers the following observations were made:
- When the request to send money was made to a legitimate PayPal user, the sender credentials were rewritten from Microsoft365 SRS (Sender Rewrite Scheme) to the one desired by the threat actor.
- An example of the same can be explained thus: bounces+SRS=onDJv=S6[@]5ln7g7.onmicrosoft.com, which passes the SPF/DKIM/DMARC check.
- This technique would also allow the scammer to gain full access and control of the target’s PayPal account.
- The scheme is developed to bypass PayPal phishing checks.
When detection tools get better at spotting and stopping malicious activities, threat actors try to work around and find access. Addressing the technique used by the scammer in this incident, Elad Luz, Head of Research at Oasis Security, a New York City-based provider of Non-Human Identity Management (NIM) solutions shared their observations.
Older phishing methods of crafting and sending emails are easy for mailbox providers to detect, Elad stated. However, in the PayPal scam, the email presented all the information that looked legitimate, and it became clear that it was designed by exploiting a vendor feature.
This points toward an upgrade needed to detect such communications. There are certain steps users must take to detect this PayPal fraud and others.
They are:
- Looking for impersonal and non-specific greetings in the communication like, ‘Dear Sir/ Madam,’ without addressing the person by their name.
- Hover over any clickable links and web pages in the email to see the preview. In most devices, the preview shows on the lower left corner of the screen. If the email claims it is from PayPal while the link reflects something otherwise, it is a red signal for being suspicious.
- If the email contains attachments that you do not usually ask or receive including bills, invoices, or others, steer clear of clicking or downloading them. In case it is too late, go ahead and check your notifications for any transactions.
- Change the password.
- Connect with the service provider and share the details about the same.
- If the communication makes you nervous or fearsome of losing something or a penalty, check with the service provider through regular contact details to make sure the alert is true. Every service provider offers a decent deadline and never stresses paying in an hour or so.
Stephen Kowski, Field CTO at Pleasanton, California-based SlashNext Email Security+ shared how neural networks can be used to create social graph patterns. This data can help better technology based on user behavior and reactions in selecting their course of action.
In the age of increased online threats, relying solely on detection and prevention tools is not enough. As Carl calls it, the human firewall should always be at play. One must base their online actions on observation, cross-checking, and alertness required at the moment.
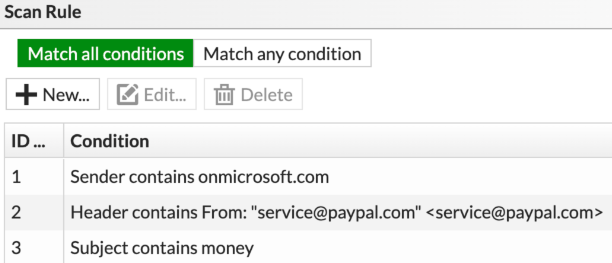
Users can create their own Data Loss Prevention (DLP) rules or a checklist to spot cases that point toward a communication coming from a distribution list.