‘Sarbloh’ Ransomware Targets Specific Political Entities in India
- There’s a highly-targeted yet unsophisticated ransomware campaign taking place in India right now.
- The actors are encrypting files down not for money but for the retraction of a law that passed a couple of months back.
- The distribution takes place via email, and the payload itself is fetched from AWS thanks to macro code.
There’s a new ransomware strain on the Indian cyber-space, targeting entities linked to a very specific political agenda. Called Sarbloh, this new piece of malware appears to be targeting entities connected with the farmer protests in India, which are still ongoing for 100 days now.
The non-financial motives of the particular strain are becoming more obvious from the fact that the distributors are not even asking for the payment of a ransom. Instead, the goal seems to be the targeted systems' lock-down, keeping them offline and threatening them on the political level.
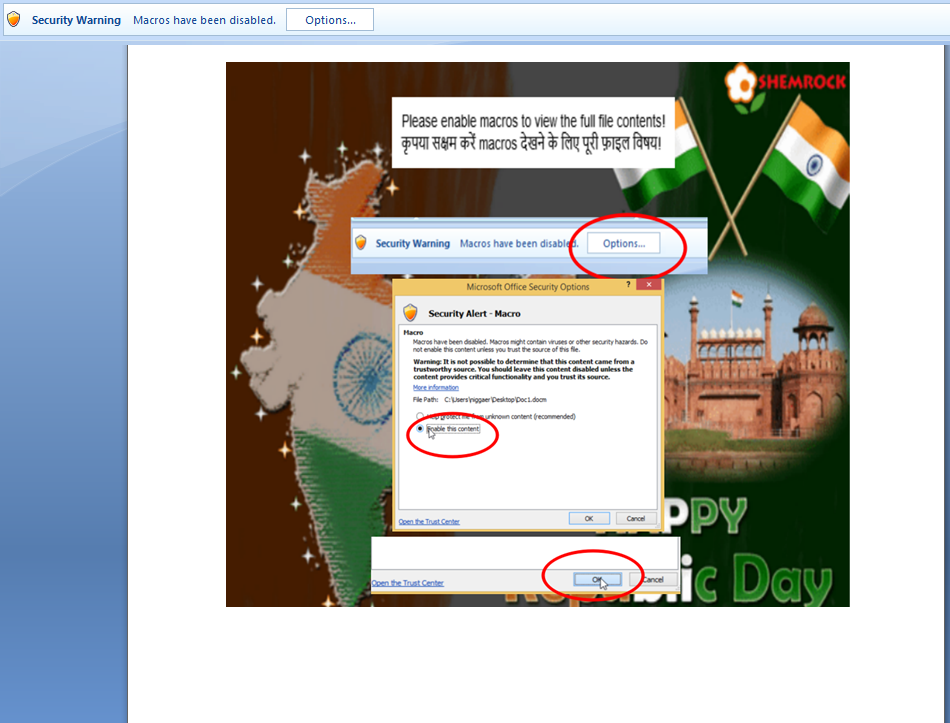
Sarbloh encrypts audio, documents, image, video, databases, and various other “key” filetypes, appending them the “.sarbloh” extension. The payload arrives via a macro-ridden document which in turn arrives via email.
The trick used by the distributors is to make the message and attachment appear as something of nationalistic interest to the recipient, urging them to “enable content” to view the file. If the recipient does that, the macro decodes the download URL runtime and fetches Sarbloh in the form of an executable named “putty.exe.”
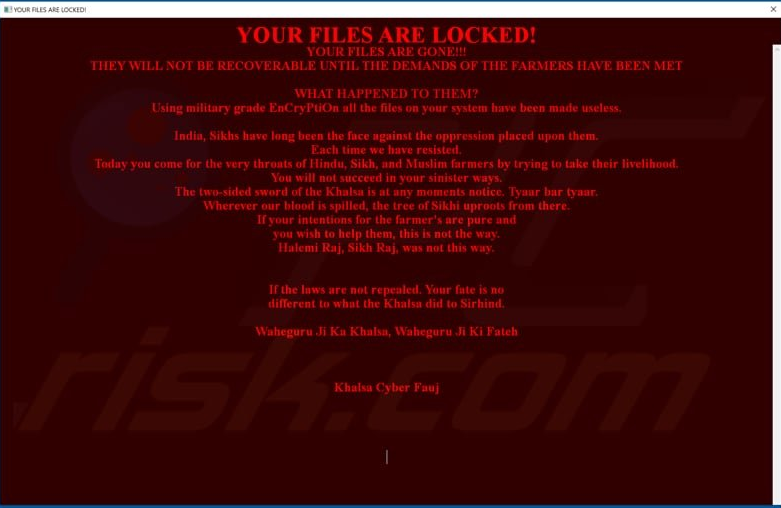
Interestingly, the payload is hosted on Amazon AWS and is downloaded through BITS (Background Intelligent Transfer Service), which has been recently abused by banking trojan campaigners as well. The ransomware executable is compiled on Borland Delphi, enumerates the file system to locate a large number of file types, encrypts them using strong encryption, and finally delivers the following note to the victim.
Based on what is mentioned on the note, the actors appear to support the farmers’ side, so they are presenting the infection and subsequent encryption of the files as retribution for all that the Sikhs, Hindu, and Muslim farmers have been through. Where there should be a ransom payment demand, the actors demanded repealing the already-passed legislation that is purported to hurt the farmers' rights to control the selling prices of their goods.
All in all, this appears to be the work of an opportunistic and unsophisticated actor, but the consequences of the infection remain dire. Make sure to never enable macros on your Office suite unless you absolutely need them, don’t download documents or any attachments that arrive with unsolicited emails, and before opening anything you have downloaded from the net, make sure to scan it with an up-to-date AV tool first.