Sandworm APT Targets Ukraine with Trojanized Microsoft Activators and Fake Updates
- The Russian Sandworm APT targets Ukraine in its latest cyber espionage campaigns.
- They distribute trojanized Microsoft KMS activation tools that disseminate DarkCrystal RAT (DcRAT).
- DcRAT can exfiltrate keystrokes, browser cookies, saved credentials, FTP credentials, screenshots, and more.
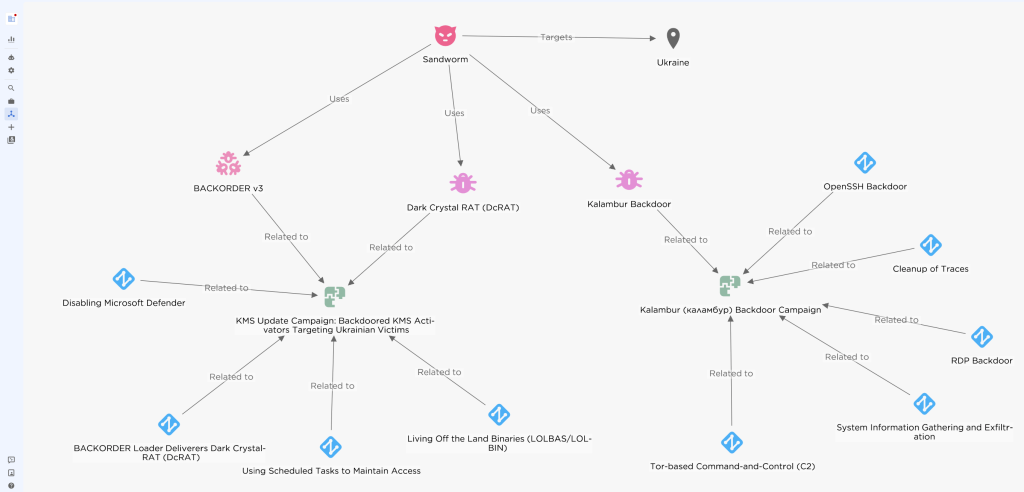
The Russian military cyber-espionage group Sandworm, also referred to as UAC-0113, APT44, Telebots, Voodoo Bear, IRIDIUM, Seashell Blizzard, and Iron Viking, has been linked to a series of malware campaigns targeting Windows users in Ukraine.
The group's latest activities rely on trojanized Microsoft Key Management Service (KMS) activators and counterfeit Windows updates to infiltrate systems, steal data, and compromise critical infrastructure, according to analysts at EclecticIQ.
EclecticIQ's analysis connects seven malware distribution campaigns to Sandworm hackers, demonstrating consistent Tactics, Techniques, and Procedures (TTPs).
The campaigns, which began in late 2023, utilize overlapping infrastructure, ProtonMail accounts for domain registration, and debug symbols tied to Russian-language build environments. The alignment of these elements strongly indicates the involvement of Russian military hackers.
Once deployed, the fake KMS activators present a counterfeit interface, disable Windows Defender, and install a BACKORDER loader that subsequently drops the DarkCrystal RAT (DcRAT) onto victims' devices.
DcRAT, a tool associated with prior Sandworm operations, is used to exfiltrate sensitive data, including keystrokes, system details, browser cookies, saved credentials, FTP credentials, browser history, and screenshots.
The most recent observed campaign, on January 12, 2025, involved a typo-squatted domain to distribute the RAT malware.
Sandworm has seemingly leveraged the widespread use of pirated software in Ukraine as a primary attack vector. "Many users, including businesses and critical entities, have turned to pirated software from untrusted sources, giving adversaries like Sandworm (APT44) a prime opportunity to embed malware in widely used programs," EclecticIQ stated.
This approach enables Sandworm to launch large-scale espionage and data-theft campaigns, jeopardizing Ukraine's national security and resilience across critical infrastructure and private sectors.
Active since at least 2009, Sandworm operates under Russia's Military Unit 74455 of the Main Intelligence Directorate (GRU), focusing on destructive and disruptive cyberattacks.
Predominantly targeting Ukraine, the group has previously executed operations involving malware like BlackEnergy, KillDisk, and Industroyer—tools designed to inflict significant damage on energy grids, transport networks, and other critical systems.