Russian Threat Actors Target Microsoft 365 Accounts Via Device Code Authentication Phishing
- Russian hackers impersonating various official entities engage in social engineering and phishing.
- The attackers’ emails invited users to an MS Teams meeting/video conference or to join a chatroom on a secure chat app.
- They aim to compromise Microsoft 365 accounts via Device Code Authentication phishing.
Russian threat actors targeting Microsoft 365 (M365) accounts increasingly deploy sophisticated phishing campaigns. These attacks use Device Code Authentication phishing, a tactic that deceives users with an unfamiliar authentication process.
Security researchers at Volexity warn that this unusual method is effective because many users fail to recognize it as phishing. Launched in mid-January 2025, the campaigns were highly targeted and politically themed, focusing on the new U.S. administration and its global impact.
Volexity tracks the actors behind these attacks as UTA0304, UTA0307, and possibly CozyLarch (similar to APT29, Midnight Blizzard, DarkHalo, and CozyDuke).
The cybercriminals impersonated individuals from political and research institutions, as well as government organizations like the U.S. Department of State, Ukrainian Ministry of Defence, and European Union Parliament.
Attackers used social engineering, spear-phishing emails, and real-time communication to gain account access. Some victims were contacted through platforms like Signal, where attackers posed as high-ranking officials.
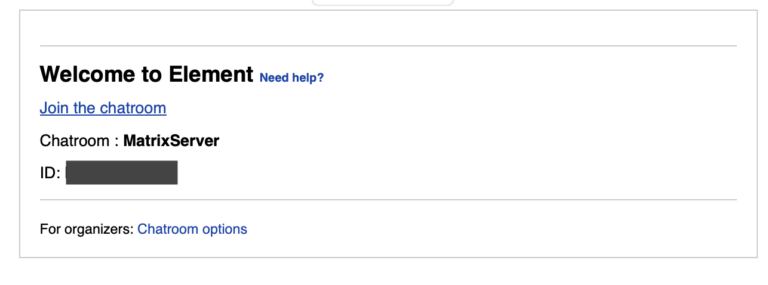
They then directed targets to attacker-controlled platforms like Element to execute Device Code Authentication phishing efficiently.
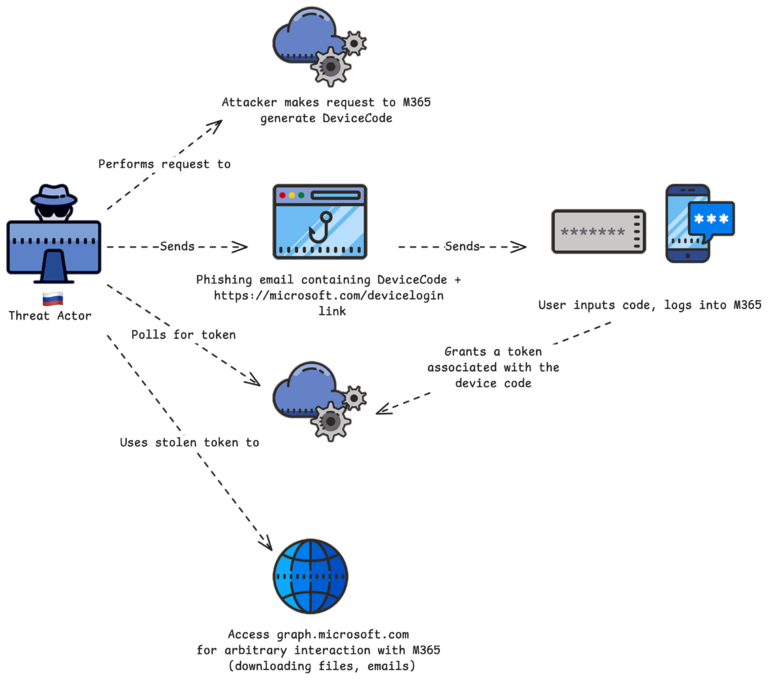
Device Code Authentication phishing exploits Microsoft’s authentication process designed for devices like smart TVs or IoT gadgets. Attackers trick targets into entering a code from a phishing link into a legitimate Microsoft login page and gain long-term account access once the victim enters their credentials and approves the request.
This method bypasses multi-factor authentication (MFA) by exploiting trust and urgency. Volexity notes it is more effective than traditional spear-phishing approaches.
The report revealed that UTA0304 operated its own Element server for real-time victim coordination and posed as officials from reputed organizations to build trust. Victims received emails with meeting or chatroom invites, linking to phishing pages mimicking Microsoft’s Device Code Authentication.
Among the highlighted key tactics are accessing emails and cloud storage (e.g., OneDrive), activity originating from VPS and Tor IPs, and tools like "python-requests/2.25.1" used for automated data theft.
The campaign came to light after a January 2025 breach. An M365 account at a Volexity client was compromised when the victim received a forged email from an impersonated Ukrainian Ministry of Defence official.
The report concludes with high confidence that these campaigns originate from Russia-based state-sponsored actors. While the campaigns share techniques and targets, Volexity tracks them separately due to operational differences.