Russian Threat Actor EncryptHub Exploits a Microsoft Management Console Zero-Day Flaw
- Russia-aligned EncryptHub (Water Gamayun) hacking group was seen deploying infostealers and backdoors in a new campaign.
- CVE-2025-26633 is exploited in the process, a recently patched zero-day in Microsoft Management Console.
- The actively developed operation employs multiple delivery methods and custom payloads for persistence and data theft.
EncryptHub, a known threat actor also tracked as Water Gamayun, leverages a recently patched Windows zero-day vulnerability, CVE-2025-26633, to distribute malicious software. The attack involves deploying backdoors and infostealers to exfiltrate sensitive data from targeted systems.
Classified as an improper neutralization vulnerability within Microsoft Management Console (MMC), CVE-2025-26633 holds a CVSS score of 7.0. The issue, rectified by Microsoft during this month’s Patch Tuesday update, enables attackers to bypass a crucial security feature locally.
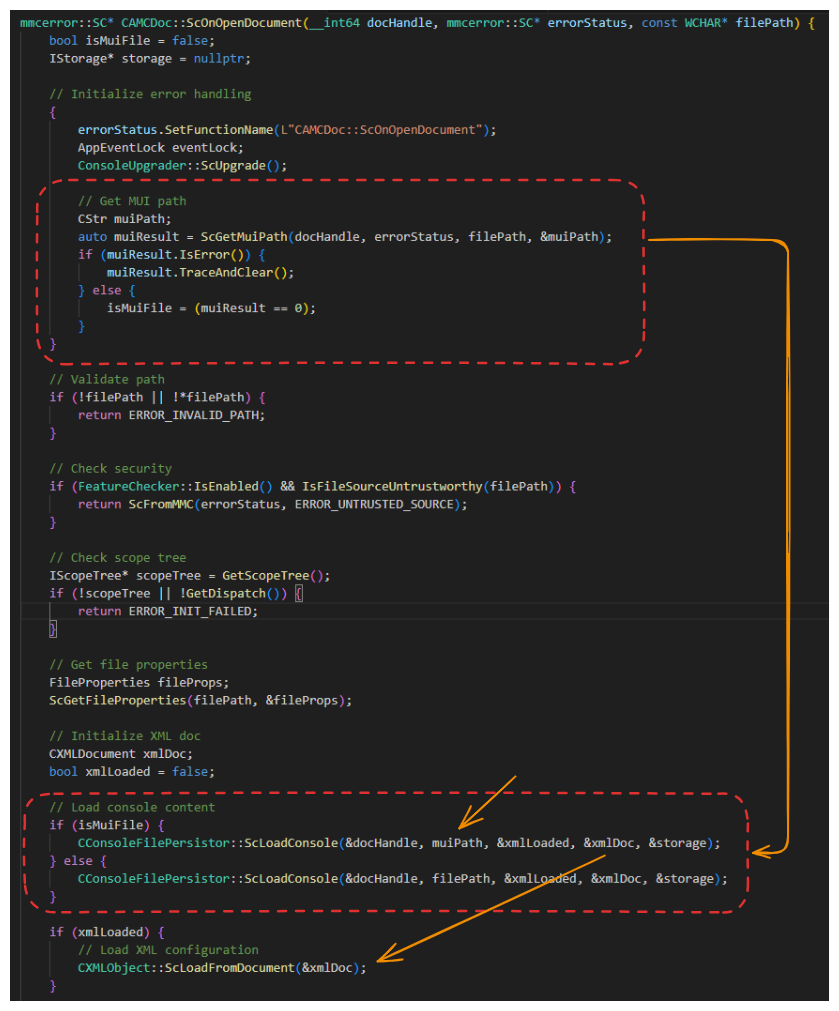
Trend Micro has dubbed the exploit "MSC EvilTwin," highlighting its mechanism of using duplicate Microsoft Console (.msc) files and MMC’s Multilingual User Interface Path (MUIPath). Attackers manipulate .msc files to execute malicious payloads instead of legitimate ones.
The attack utilizes PowerShell-based loader MSC EvilTwin to create two identically named .msc files in separate directories. When the original .msc file is executed, the MMC unintentionally selects the malicious version stored in the directory "en-US," bypassing detection.
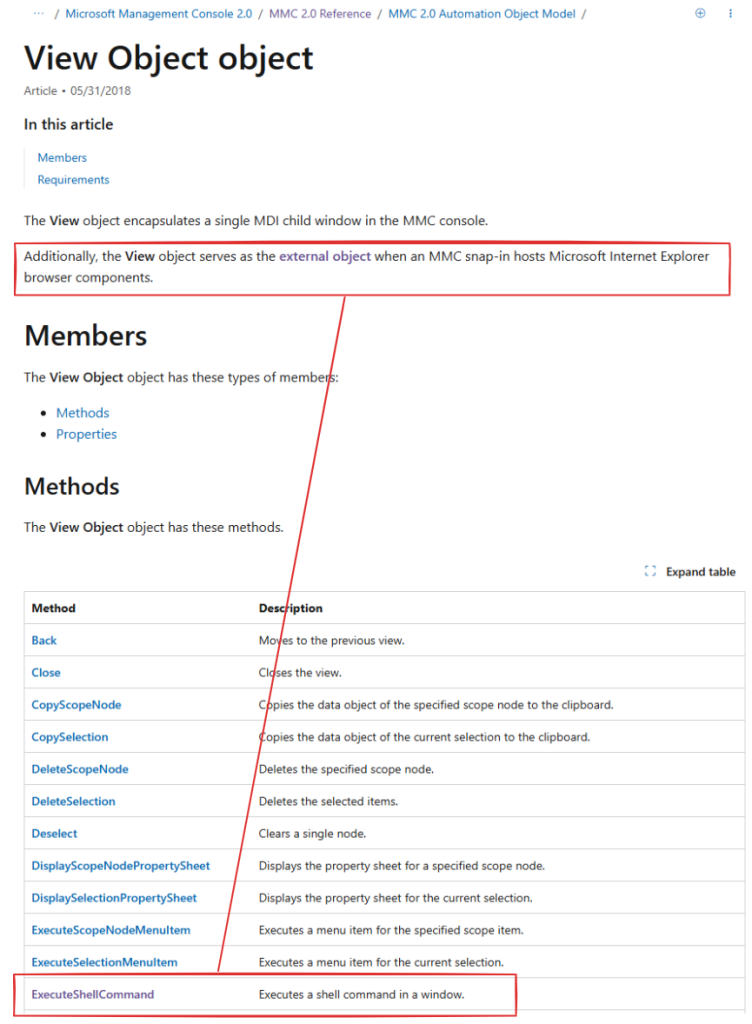
Trend Micro’s analysis also reveals EncryptHub employing additional methods, including ExecuteShellCommand exploits via MMC’s function to download next-stage payloads and deploying malicious .msc files in altered folders like "C:\Windows \System32" (with trailing spaces) to bypass User Account Control (UAC).
The threat actor has developed an array of malware tools under its umbrella, including the EncryptHub Stealer and backdoors known as DarkWisp and SilentPrism, collectively referred to as EncryptRAT by Outpost24. Infostealers such as Rhadamanthys and StealC are also in the group’s arsenal.
The attack begins with victims downloading seemingly legitimate installation files, such as digitally signed MSIs impersonating popular Chinese software like DingTalk or QQTalk. These files serve as a pretext for remotely fetching and running MSC EvilTwin loaders.