Russian Hackers Steal $3 Million From a Private Bangladeshi Bank
- A Russian-speaking hacker group has successfully stolen $3 million from the Dutch Bangla Bank.
- Two more private banks were targeted as well, but the attacks were deflected this time.
- The evidence that points to the Silence hacker group includes C2 server communication and ATM jackpotting techniques.
As reported by “The Daily Star”, a group of hackers has targeted three Bangladeshi private banks, namely the Dutch Bangla Bank Limited (DBBL), the NCC Bank, and the Prime Bank, with the former losing $3 million and the other two successfully defending the attacks. According to sources from within the banking sector, the hackers planted malware inside the bank’s card management system about three months ago and created a perfect replica of the switch. Last month, Ukrainian accomplices of the hackers used cloned cards to draw a total of $3 million from ATMs in Cyprus, always with the help of the “shadow switch” and without the bank realizing it at the time.
The withdrawals occurred between May 1 and May 3, but it wasn’t until Visa reached out to DBBL asking them to settle payments for transactions the bank’s clients made in Cyprus that the bank got to learn about the hack. DBBL couldn’t see the claimed transactions in their system, but Visa provided solid evidence, so the bank was convinced and paid the amount. The NCC Bank and the Prime Bank also had their security systems compromised at a later date but suffered only negligible financial losses as a result. The money mules who tried their luck again were caught this time, while the relevant video shows the person talking on the phone, possibly to coordinate the remote triggering of the ATM jackpotting.
The problem with banks in Bangladesh and the reason why hackers target them is their characteristic lack of adequate security measures. The DBBL, which lost $3 million this time, does not have the PCI DSS certification (Payment Card Industry Data Security Standard), has not invested much in their IT security and human resources, and according to local analysts, possibly even uses pirated software tools that are incredibly vulnerable to attacks. In the same time, DBBL maintains the largest network of cash machines and has the highest number of debit cards in circulation in Bangladesh, so this was really a time bomb for them.
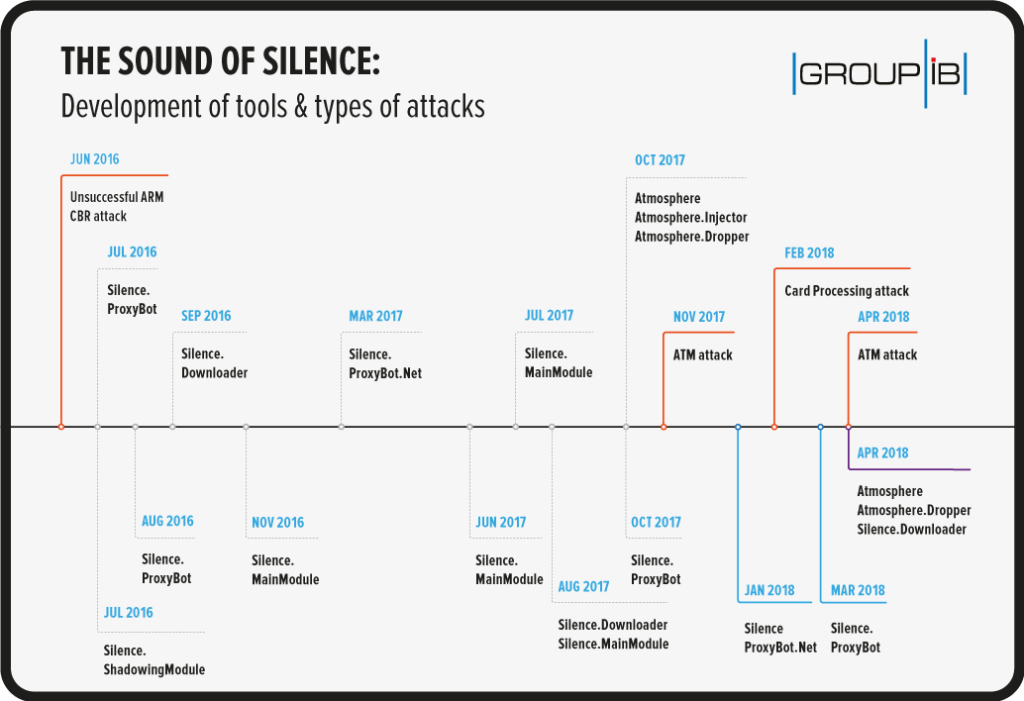
Banking security expert Group-IB believes that this is the work of the Russian-speaking hacker group known as “Silence”, as the tool that was used for the ATM jackpotting points to them. Moreover, the evidence also shows that DBBL’s hosts were communicating with Silence’s C2 server, so there’s little doubt about who’s behind the heist. The particular group has targeted Russian and Ukrainian banks in the recent past, while phishing emails from them have also reached bank employees in Europe, Africa, and Asia.
image source: group-ib.com
Have something to say about the above? Feel free to leave your comments down below, or join the discussion on our socials, on Facebook and Twitter.