Russian Hackers Are Selling Access to Hundreds of Pulse Secure VPN Servers
- A large list of vulnerable Pulse Secure VPN servers was made available for purchase on a Russian cyber-crime forum.
- The list contains hundreds of IPs with various details like user login credentials in plaintext form.
- The hackers exploited a year-old flaw to exfiltrate this information, so seeing these systems patched now is unlikely.
A Russian hacker is selling access to hundreds of Pulse Secure VPN servers deployed at the enterprise. ZDNet, who got the list from KELA researchers, reports 913 IPs, but Bank Security raises that number to 1800 IPs.
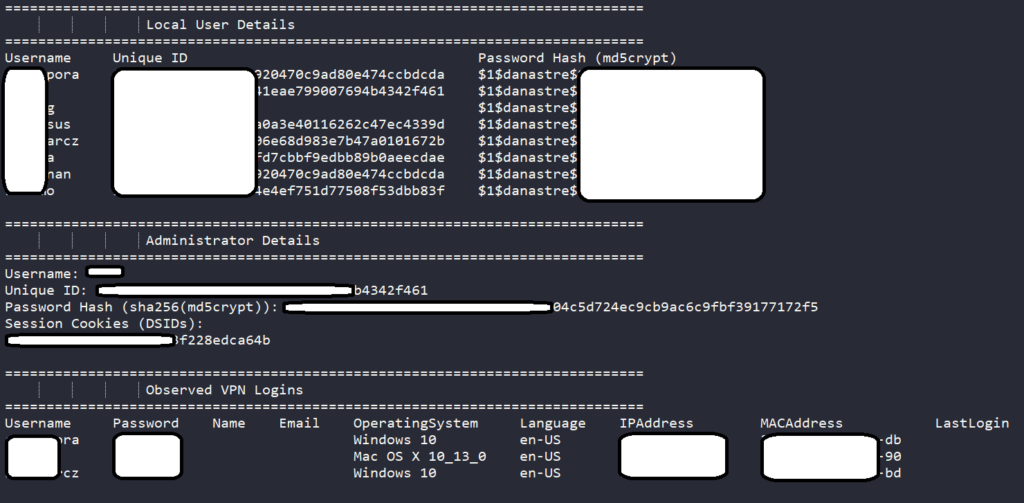
The list that’s for sale includes the IP addresses, SSH keys for each server, admin account details, the server firmware version, the VPN session cookies, and the VPN login data. That last entry is where usernames and passwords in plaintext form are to be found, which basically allows anyone to break and enter.
A well-known Russian-speaking Threat Actor shared details of over 1800 IPs vulnerable to the latest Pulse CVEs.
For each IP the actor shared many details including user & administrator clear-text credentials.
Big Banks and notable organizations are on the list.
🔥PATCH NOW!🔥 pic.twitter.com/QqyPBG17Mq— Bank Security (@Bank_Security) August 4, 2020
After analyzing the data, the researchers found that the firmware versions of the particular servers are all vulnerable to the CVE-2019-11510 flaw, which enables hackers to gain access to the target system and dump server data. This is precisely what seems to have happened here, and we’re talking about a vulnerability that has been known and widely publicized since August 2019.
Even in May 2020, a report co-signed by CISA and the FBI warned about the particular vulnerability, as it remained on the top of the most exploited flaws in 2020, denoting that a large number of admins hadn’t patched their enterprise VPN tools.
Source: Bank Security | Twitter
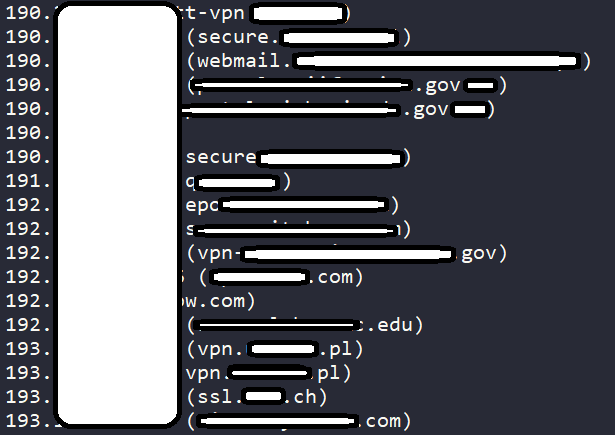
The threat actor returned to enrich the offering with more information only a few hours ago, adding a list of domains that are related to the IPs. In there, there are multiple .gov domains, large banks and financial institutes, and various well-known firms.
Since the credentials are out there, patching the Pulse Secure VPN servers now wouldn’t fix the problem. The exposed firms also need to patch and reset their credentials to keep hackers out of their corporate network.
Source: Bank Security | Twitter
As for how much time Pulse Secure VPN admins have to do all that, there’s none really. The forum where the exposure took place is a den for REvil, NetWalker, Lockbit, and other notorious actors who launch attacks immediately when an opportunity arises. That said, if there’s anything to give you time right now, that would be the large number of entries in the list.
Honestly, at this point, a full year has passed since these systems should have been patched, so we don’t believe there’s any hope to see them secured now. That said, a surge of ransomware-induced lockdowns that will take systems offline and have clients complaining is just around the corner.