Russian Espionage Group Using Novel RDP-Based Phishing Targets European Govt and Military Organizations
- European government and military organizations are targeted by a Russian-nexus cyberespionage actor via RDP connections.
- UNC5837's campaign utilizes .rdp configuration files to automate RDP connectivity from the victim’s devices to attacker-controlled domains.
- They used deceptive, attacker-controlled applications disguised as legitimate software to infiltrate.
A novel phishing campaign that targets European government and military organizations employs innovative techniques overlooked by conventional cybersecurity measures. It was attributed to a Russian nexus espionage group codenamed UNC5837.
The campaign was first observed in October 2024 by the Google Threat Intelligence Group (GTIG) and used signed .rdp configuration files as phishing email attachments for Remote Desktop Protocol (RDP) connections on victims' machines.
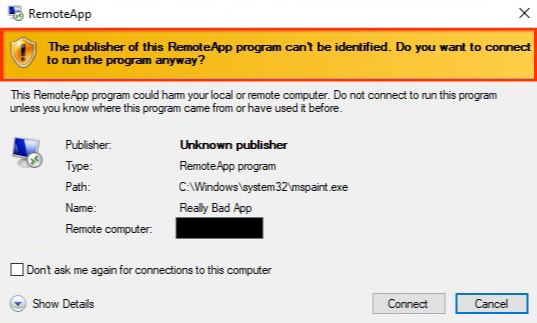
Unlike traditional RDP attacks relying on interactive sessions to control victim machines, UNC5837 creatively exploited lesser-known functionalities of RDP. This approach bypassed user security warnings by leveraging SSL certificates issued by Let's Encrypt that matched the attacker-controlled domains.
Once activated, these .rdp files established RDP connections between the victim's devices and the attacker’s command-and-control (C2) servers, redirecting victim resources and introducing attacker-controlled RemoteApps.
Using features such as resource redirection and RemoteApps, the group accessed sensitive resources and offered deceptive, attacker-controlled applications disguised as legitimate software.
This approach allowed them to perform activities like file exfiltration, clipboard content capture—including passwords—and reconnaissance of victim environment variables, all without direct command execution on victim devices.
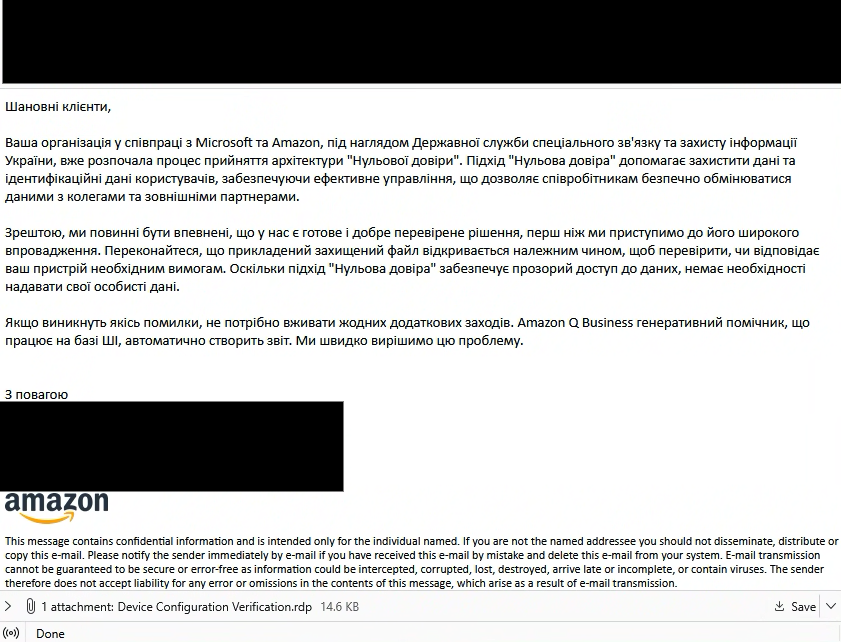
The campaign's phishing emails claimed to originate from a collaborative project involving tech leaders like Amazon, Microsoft, and Ukrainian government agencies. The email attachments purported to be project-related files, titled to appear legitimate. Recipients were instructed to run the attachments despite errors, under the pretext that error reporting was automated.
When victims executed these .rdp attachments, RDP connections redirected local drives and other devices to attacker servers. A deceptive RemoteApp, labeled "AWS Secure Storage Connection Stability Test," appeared on the victim’s machine, hiding its malicious functionality.
While full details of the application's intent are unknown, it likely served purposes such as phishing or facilitating further intrusion.
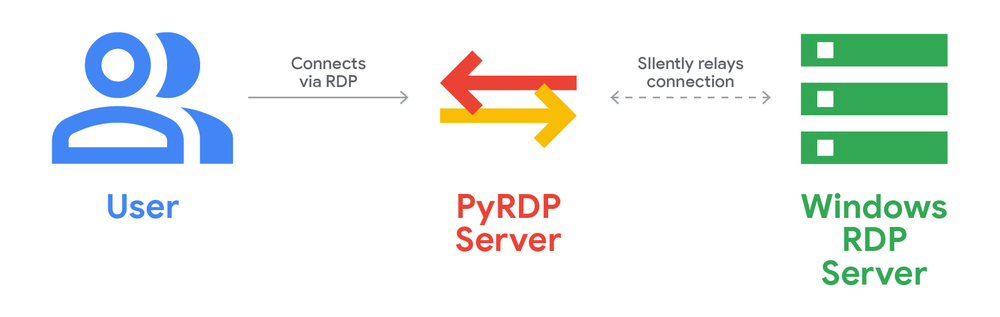
Evidence suggests the attackers may have used an RDP proxy tool like PyRDP to automate malicious activities. PyRDP, an open-source tool, allows attackers to streamline RDP-based operations, making campaigns like this more scalable and complex.
The malicious .rdp files redirected victim resources, granting full read/write access to local drives and capturing clipboard content, including sensitive data like passwords.
To enhance deception, attackers deployed RemoteApps presented as AWS diagnostic tools. However, these applications were hosted on attacker servers, weaponizing trusted interfaces to facilitate phishing and intrusion activities.
Evidence points to the potential use of PyRDP, an open-source RDP proxy, to automate tasks such as data exfiltration and user monitoring. While this tool simplifies attacker operations, it operates within the permissions granted by the RDP session.
Though no exploits in the RDP protocol itself were detected, the use of such tools demonstrates how standard features can be misused with devastating impact. While direct command execution was not observed, the attackers gained significant access to victim environments.