RomCom Malware Variants Target Entities in Ukraine and Poland
- The UAT-5647 cybercriminal gang, also known as RomCom, was seen deploying advanced malware variants in a new wave of malicious operations.
- One of the downloaders is designed for people who speak Polish, Ukrainian, and Russian.
- Brute force and password spraying are employed to gain initial access in these new apparently cyberespionage campaigns.
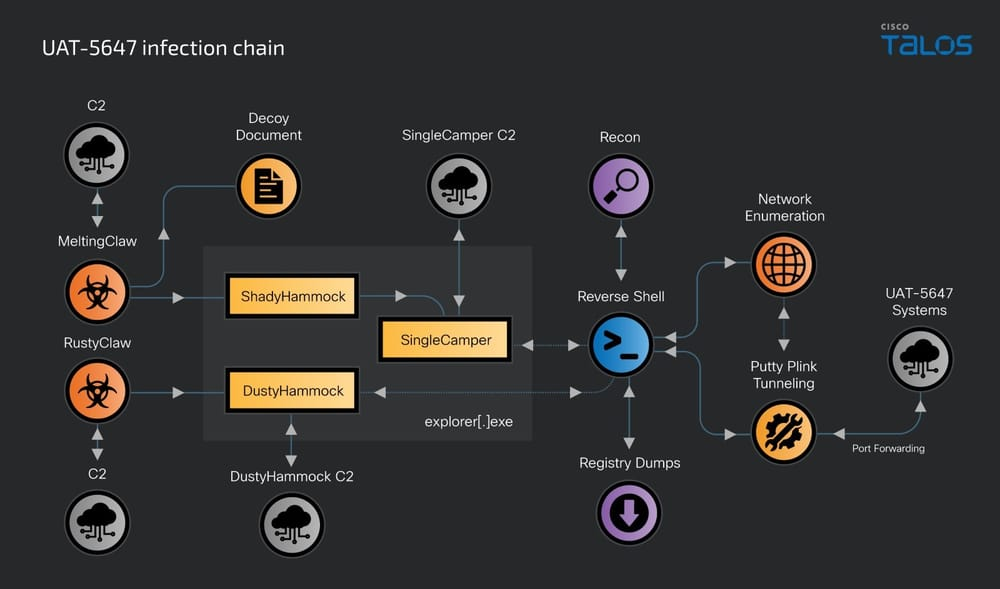
A new wave of sophisticated cyberattacks attributed to a Russian-speaking group known as UAT-5647 targeted Ukrainian governmental institutions and unidentified entities in Poland. This threat actor, also referred to as RomCom, is deploying advanced malware variants in these operations, namely the updated SingleCamper malware.
Cisco Talos security researchers said in a new cybersecurity report that the latest campaign has evolved with UAT-5647 employing four distinct malware families.
A notable tactic in these attacks is the targeting of edge devices within compromised networks. UAT-5647 attempts to tunnel internal interfaces to external hosts, effectively bypassing detection mechanisms. Techniques such as brute force or password spraying are employed to gain initial access, followed by data exfiltration and network reconnaissance.
The RustClaw and MeltingClaw downloaders are two variants that initiate the infection chain via spear-phishing emails. The first is a RUST-based malware designed for Polish, Ukrainian, or Russian-speaking users, leveraging keyboard layout checks to ensure regional targeting, while the latter operates similarly, using C++ to infiltrate systems.
The infection chain commences with a phishing email embedding the downloader, which installs a decoy PDF and subsequently downloads the next-stage implant, DustyHammock.
After deploying the anti-analysis feature to prevent malware from running in sandboxes with randomized names, the downloader optionally downloads the decoy PDF to display to the infected user.
Then, it downloads the next-stage implant, DustyHammock, to locations on disk, which acts as the primary backdoor, handling communication with command and control (C2) servers and executing malicious actions.
Another backdoor, ShadyHammock, facilitates the deployment of the RomCom backdoor variant SingleCamper and may intercept additional commands from other malicious components. These implants prepare the environment for further malfeasance by establishing discrete channels for espionage activities.