Russia-Linked RomCom Hackers Exploit Firefox and Windows Zero-Day Vulnerabilities
- Russian-speaking group tracked as RomCom (UAT-5647) abused zero-day flaws in Mozilla Firefox and Windows.
- The campaign mainly targeted Europe and the U.S. via an attacker-controlled website that automatically deployed backdoor malware.
- Mozilla responded promptly with a patch for Firefox, and Microsoft addressed the vulnerability in Windows.
Cybersecurity researchers have uncovered a sophisticated hacking campaign led by the Russian-linked cybercrime group RomCom, exploiting previously unknown zero-day vulnerabilities in Mozilla Firefox and Microsoft Windows.
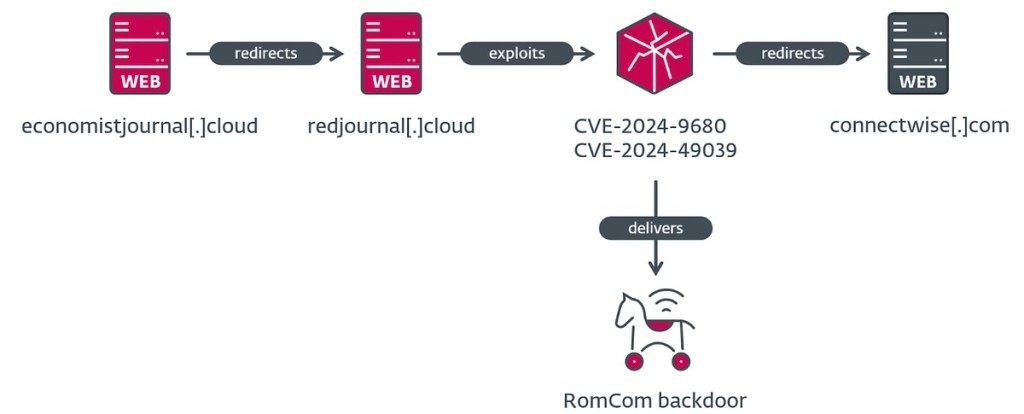
The campaign primarily targeted users across Europe and North America and involved two zero-day bugs, enabling a zero-click exploit. This advanced technique allows attackers to deploy malware on a system remotely without user interaction.
Victims merely needed to visit a malicious website controlled by RomCom, a Russian-speaking group known as UAT-5647, where the group’s backdoor malware would then be planted on their systems, granting hackers broad access to devices.
RomCom is associated with cyberattacks aligned with Russian government interests, previously linked to a ransomware attack on Casio and campaigns targeting Ukraine-allied organizations.
Their use of a zero-click exploit demonstrates heightened sophistication and intent to conduct stealthy, damaging cyber intrusions. Targets ranged from individual victims per country to as many as 250 victims across Europe and North America.
Mozilla responded promptly with a patch for Firefox on October 9, following an alert from ESET researchers. The Tor Project also patched its Tor Browser based on Firefox's codebase, though no evidence points to the Tor Browser being exploited.
Microsoft addressed the vulnerability in Windows on November 12, following its identification by Google’s Threat Analysis Group, which monitors state-sponsored threats.
This hacking campaign is a stark reminder of the continued threat posed by state-linked cyber actors leveraging advanced exploits. Organizations and individuals are urged to update their software and implement robust security measures to mitigate risks associated with zero-day vulnerabilities.
For further details, visit Mozilla and Microsoft’s official security advisories.