The Role of Initial Access Brokers in the Ransomware Scene
- Hackers who compromise firms sell their services to RaaS groups, as the demand is rising.
- These actors support and practically enable the augmentation of ransomware infections.
- Initial access agents have to advertise their offerings carefully - otherwise, they may lose them.
Ransomware groups are working like fine-tuned machines, assigning distinctive roles to specific teams and raising their money-making effectiveness to the maximum level. But for anything “nasty” to happen, one needs to establish initial access to the target’s systems, and this is maybe the most time-consuming and complicated process.
One has to scan the target for vulnerabilities, identify potential opportunities, and then break in without getting detected. A report from Digital Shadows touches this subject, focusing on the “initial access” actors and their role in the rise of the RaaS problem.
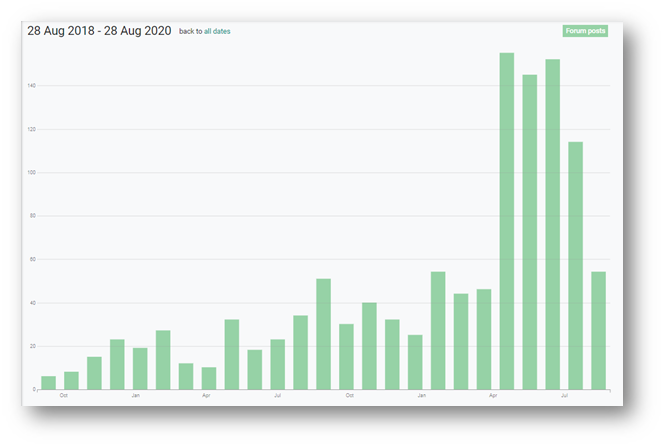
Hackers who are able to access company systems remotely are promoting their services to ransomware groups on dark web forums, and these listings have risen to unprecedented levels this year. From network access to full RDP domain admin access, the listings come with price tags between $500 and $10,000.
The hackers don’t care about who’s buying their services and what they’re planning to do with the access, they just want to make money - and they are.
Source: Digital Shadows
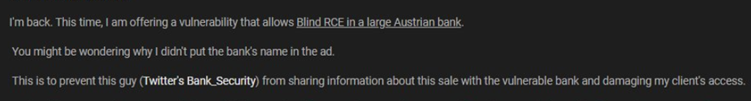
Digital Shadows have noticed an interesting dynamic that comes into play for this category of actors. Once they gain access to a firm’s systems, they have to decide how open and vocal they’ll be about it. Advertising the hack with many details will increase interest and will raise the auction value as a result.
At the same time, though, the risk of white-hat researchers learning about who has been compromised and helping the affected organization secure its systems also rises. That’s why the hackers are trying to give away enough details to draw attention, but no giveaway clues.
Source: Digital Shadows
This is precisely where business intelligence platforms come into play, and services dedicated to finding out who has been hacked by looking at secondary elements like company size, location, revenue, etc.
So, essentially, this is a peculiar cat and mouse game, where the mouse needs to go for the cheese even though it knows the cat is out there, watchful and ready. The greater the risk, the larger the cheese, but generally, those who have managed to break in a large organization’s systems are starting from a good point.
The re-ignition of RaaS (ransomware as a service) groups and the addition of file-stealing extortion platforms have sucked more crooks in the particular field, and there’s an entire money-making industry of inter-supporting groups of actors at the moment. System admins can take note of how all things trouble begin, so patching the systems they manage by applying the latest available update should be a solid first step.