Ride-Hailing Firm ‘Bykea’ Leaked Out Sensitive Data of Drivers and Customers
- Bykea has exposed unencrypted driver and customer PII via an unprotected elastic server.
- The information in the 200GB of leaked data also includes trip details, contracts, and technical logs.
- Drivers suffered a more impactful compromise and now run the risk of having their info abused by fraudsters.
The Pakistani ride hailing and parcel delivery service ‘Bykea’ has exposed the sensitive details of its drivers and customers after it failed to properly secure an elastic server that contained 200GB and 400 million records. The discovery comes from researcher Anurag Sen, who found the database during a routine IP-address check on specific ports.
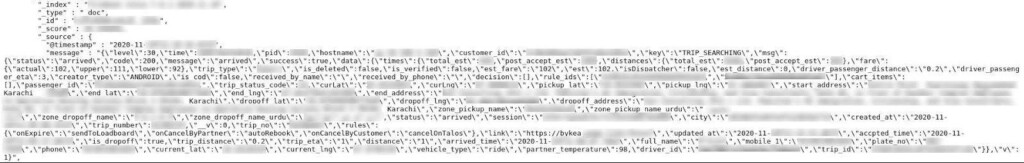
According to the relevant report, the contained data was not encrypted, so any unauthenticated user knowing the server’s IP address could have accessed and copied it.
As the researching team discovered upon looking deeper into the data, Bykea suffered another data breach in September 2020, when hackers found an exposed database again and wiped it. Back then, the firm decided to publicly claim that no customer data was compromised due to the attack and simply restored from a backup.
This time, the data that has leaked out includes the following:
Customers:
- Full names
- Phone numbers
- Email addresses
Drivers:
- Full names
- Phone numbers
- Address
- CNIC (Computerized National Identity Card)
- Driver license numbers, issuing city, expiry dates
- Body temperature readings
Other:
- Internal API logs
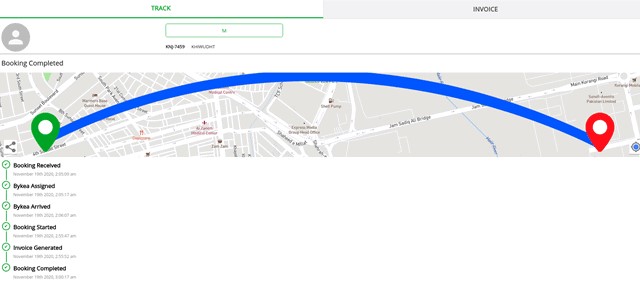
- Collection and delivery location information
- User token ID with cookie details and session logs
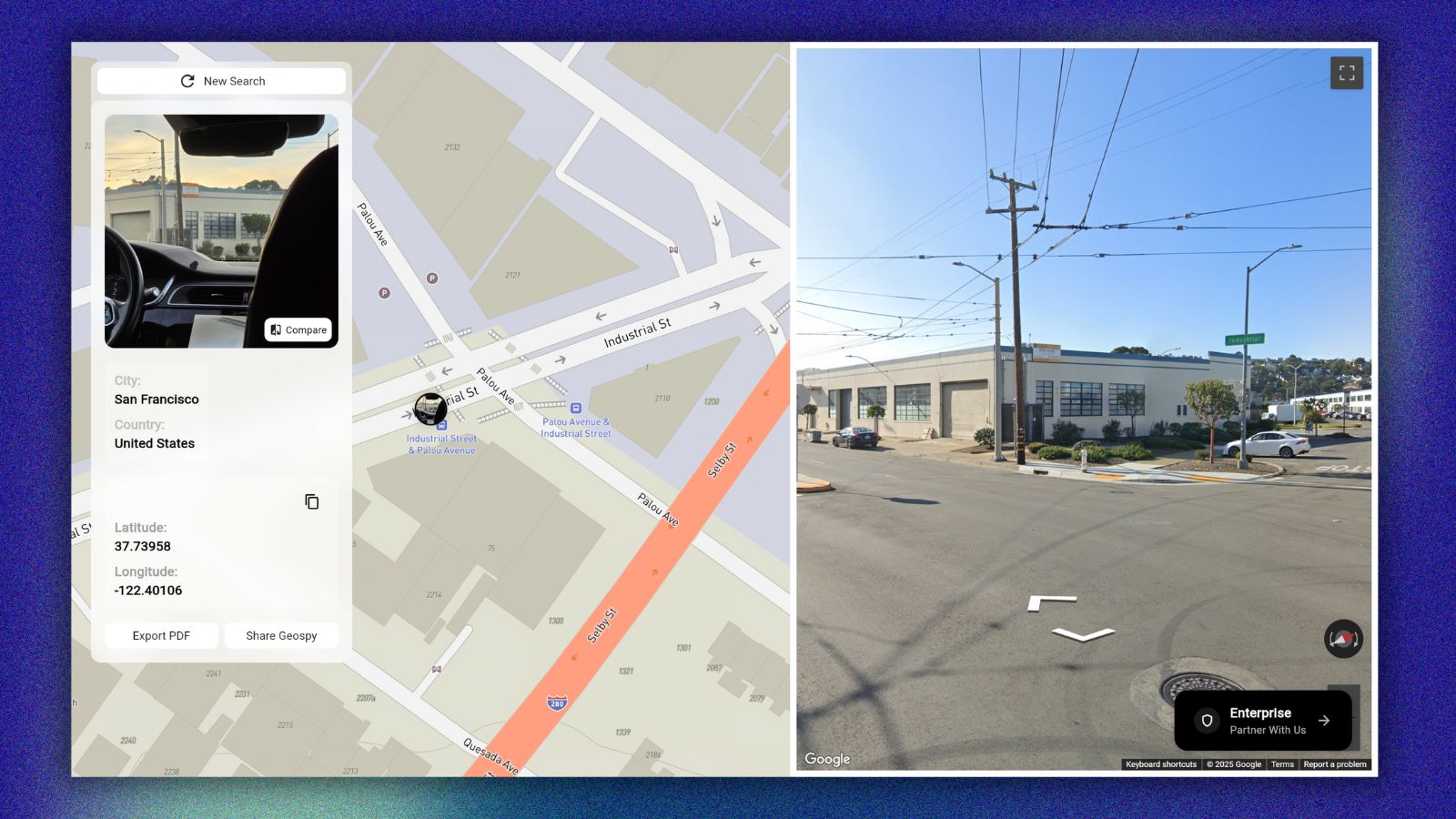
- Specific GPS coordinates
- Vehicle information, including model and number plate
- Driver license expiry information
- Miscellaneous user device information
- Encrypted IMEI numbers
The researchers also accessed invoicing documents that revealed full trip details, so someone could do a targeted investigation on a person’s whereabouts by knowing their name, or phone number, or email address. Other crucial info found in the server includes commercial relationship contracts and cleartext employee credentials.
The breach's impact is different for the drivers and the customers, but it is severe for both and should guarantee the distribution of notifications by Bykea. Judging from the firm’s stance in the past, we wouldn’t expect to see that happening, though.
Drivers should be aware of the possibility of insurance fraud and impersonation, which would create a dire situation for them. Customers will most likely have to deal with scamming and phishing attempts, but blackmail would also be a rare possibility thanks to the trip detail leaks.
As for the firm itself, restoring from backups isn’t fixing the exposure of employee credentials, backend data, corporate network, the leak of technical logs, and the fact that they offered crooks an easy way to plant spyware or ransomware. Also, now that this is public, the reputation damage cannot be mitigated with statements of assurance that nobody other than the researchers accessed this data.