The REvil Ransomware Gang Threatens to Publish Celebrity Surgery Photos
- The REvil ransomware group, which has threatened to publish celebrity photos, has let two-thirds of the stolen data out.
- The remaining data part is possibly kept for the last step of the extortion to “The Hospital Group.”
- The REvil has passed from a season of bulk targeting to a period of highly focused attacks.
For ransomware actors today, getting into systems and networks is the easy part. The difficult thing is convincing the victim to pay the demanded ransom. On that front, there’s quite a lot of “innovation” going on, and threat actors are constantly considering new platforms of extortion, compelling arguments, and powerful levers of pressure.
The latest new trend comes from the REvil group, which is looking to exploit healthcare targets - and according to recent reports, they are threatening to publish plastic surgery photos of celebrities.
The REvil group has recently compromised “The Hospital Group” in the UK, allegedly stealing 900 GB of data in the process. This data concerns patient photographs from plastic surgery procedures, and some of them exposed well-known individuals.
The procedures concern bariatric weight loss surgeries, breast augmentations, nose jobs, etc. Many of the people who went through these procedures chose to keep it a private matter, so the threat delivered here affects many people and on multiple levels.
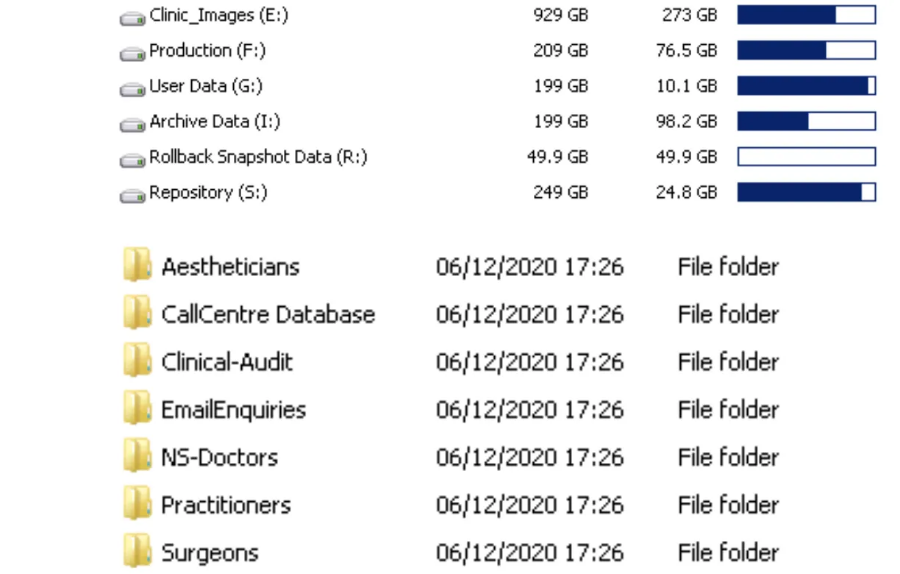
From what was published on the dark web, which we accessed with the help of KELA, there are also details about the doctors, practitioners, surgeons, aestheticians, and even clinical audit details and the call center database. However, extorting The Hospital Group with this data is not likely to yield the desired results. Instead, the ultimatum focuses on releasing images that expose the healthcare organization’s celebrity clientele.
After ten days of not hearing back from the compromised entity, the actors decided to leak 600 GB of the most important documents, personal data of customers, and several intimate photos of clients that, as they warn, are not a pleasant sight. We don’t know if the remaining 300 GB they’re holding back for now are those that expose the celebrities or not, but this partial publishing move points to this scenario.
REvil has been more selective in its targeting during the past few months, and while their activity has toned down a bit, the group is still out there and hunting. The particular group culminated last summer when they hit large power companies, breweries, railway management firms, and a prominent law firm in the United States. After all that, they sought to recruit new promoters and testers and then went from bulk targeting to highly-focused stinging.