Researchers Warn About a New Sophisticated Malware Named ‘JhoneRAT’
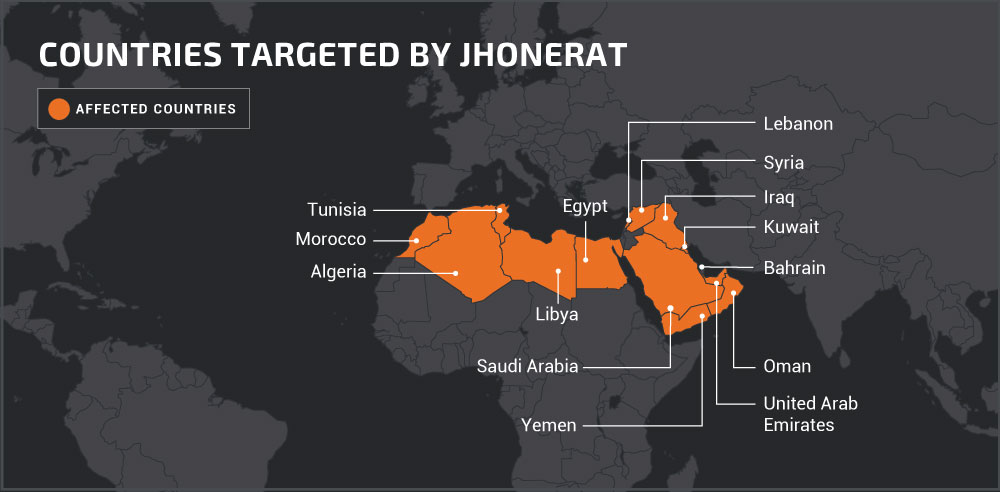
- A new malware called JhoneRAT is infecting Arab computers and steals crucial information.
- The campaign uses multiple payloads and Cloud services so as to evade detection.
- JhoneRAT is particularly hard to detect as it won’t run on VMs and will blend with the rest of the network traffic.
A new remote access trojan (RAT) has appeared in the Middle East, stealing information from its victims and downloading additional payloads as required. Dubbed “JhoneRAT”, it has been around since November 2019, and it is mainly targeting Arabic-speaking users (by checking the keyboard layout). To keep it safe from discovery, the actors have equipped JhoneRAT with features that make use of Twitter, Google Forms, and Google Drive. Moreover, the new malware was written from scratch, so it uses none of the known code that can be identified and flagged by most AV tools.
Source: Cisco Talos Blog
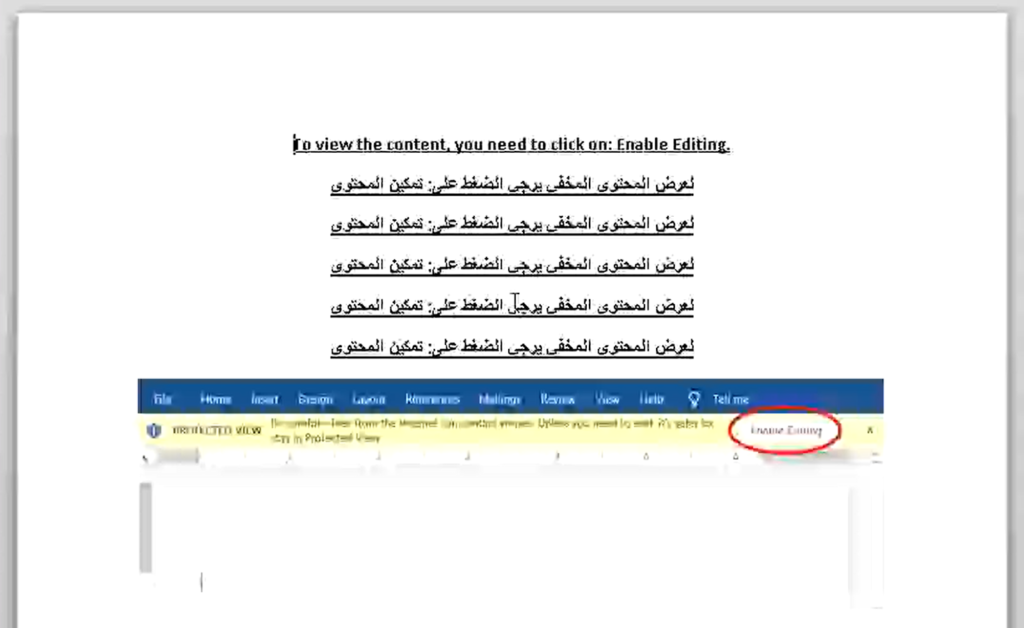
According to the Cisco Talos researchers who have been following the relevant campaign, the infection is carried out via a malicious document that is hosted on Google Drive. This is a great way to avoid URL blacklisting and create the first layer of legitimacy. The document contains a macro that will download additional payloads from Google Drive. As for the name of the risky file, one is “Urgent.docx” and another one is “fb.docx”. Possibly, there are and will be more, so checking the names alone won’t save you. Not enabling macros on your office suite though, and not opening random files will.
Source: Cisco Talos Blog
When the macro runs, it fetches a second payload which is an image file hosted on Google Drive. The image contains a base64-encoded binary, so there’s the trick of steganography involved in this campaign. Once opened, another binary (AutoIT) is downloaded from Google Drive again, and finally, a fourth payload which is the JhoneRAT is downloaded and executed from three different cloud services (depends on the C2 commands). The RAT can do three things. Firstly, it can take a screenshot and upload it to ImgBB. Secondly, it can download additional binaries and execute them. And thirdly, it can execute commands and send the output to Google Forms.
Source: Cisco Talos Blog
This is a relatively sophisticated campaign that is hard to detect and stop because of the use of the Cloud service providers, as well as the anti-analysis and anti-VM features that have been incorporated. If you’re using a VM or any sandbox to test the documents before opening, you should ensure that the virtual OS uses a keyboard layout that matches one of the countries given above. Moreover, you should also ensure that there’s a valid disk serial number assigned to the virtual drive. If these prerequisites aren’t met, the malware will remain dormant.