Researchers Unveil Technical Details About FIN7’s JSSLoader
- Researchers dive deeper into how FIN7’s JSSLoader actually works as the RAT continually evolves.
- While malware toolsets are a moving target, methods, tactics, and oftentimes infrastructure remain unchanged.
- Closely monitoring the activities of hacking groups is still crucially important for security.
Actual details about the JSSLoader component used by the “FIN7” threat group, also referred to as “Carbanak,” have remained elusive even though the white-hat research community knows about its existence for a while now. Morphisec has finally analyzed the minimized .NET RAT (remote access tool), leveraging an opportunity that arose from a failed attack last month, and they are now in a position to share more about how it exfiltrates data, how it establishes persistence, what commands it supports, how it does auto-updating, and more.
The compromise begins with a phishing message leading to the downloading of a VBScript. This is what fetches the JSSLoader and executes it through a scheduled task to add the element of the time delay. The Morphisec researchers report that this VBScript is very similar to what is used by ongoing QBOT campaigns.
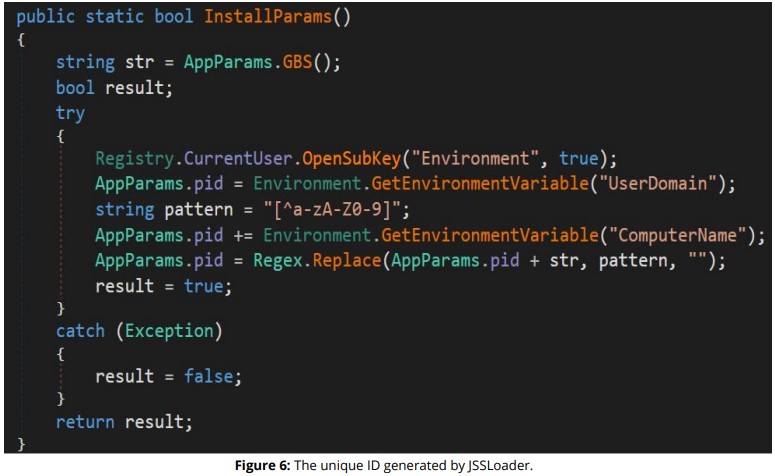
According to the analysis of the latest JSSLoader samples, the tool is tracking the target by first generating a unique ID of the victim, which is a combination of the computer’s serial number, computer name, and domain name. The anti-debugging is pretty minimalistic, using TickCount timing checks.
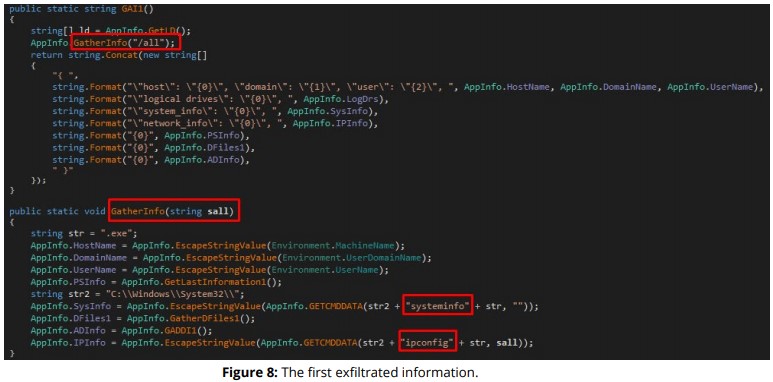
Passing to the exfiltration of information, the RAT collects the following data and encodes them with base64 before they are sent to a preconfigured URL:
- Host name
- Domain name
- User name
- Running processes
- System information (patches)
- Desktop files
- AD information
- Logical drives
- Network information
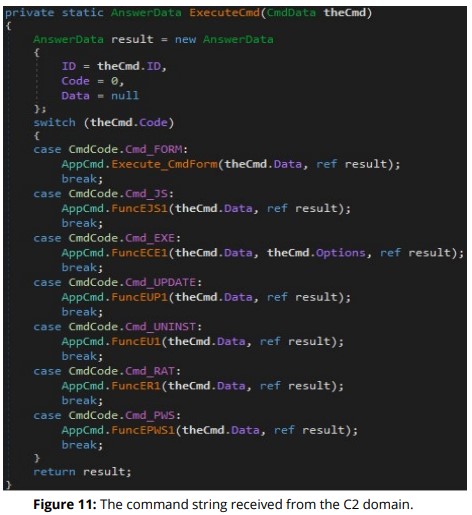
Being a RAT, it supports remote command execution too, which can be delivered to it via a ‘Get’ command right from the C2 domain. There are multiple execution options, like commands to execute a file, pop a form, execute PowerShell in memory, write a DLL, exfiltrate data, activate the auto-update functionality, or even uninstall the JSSLoader, delete its persistence mechanisms, and terminate all processes.
FIN7 is making a real effort to keep the JSSLoader component up to date and ever-evolving, and what is described above is the result of a long-term endeavor to develop the tool.
That said, while malware is indeed a moving target, adversaries like FIN7 are still following a set of tactics that don’t change much. So threats that derive from that group - and any group, for that matter - can always be fingerprinted and closely tracked.