Researchers Find a Way to Track iOS and Windows Devices via Bluetooth
- Three scientists have developed a Bluetooth tracking algorithm that works on Mac, iOS, and Windows.
- Android devices are invulnerable to this algorithm thanks to the way the associated SDK works.
- One solution would be to turn off your Bluetooth regularly, and then activate it when required.
Researchers from Boston University have disclosed a vulnerability on devices running iOS, macOS, and Windows 10, which enables an attacker to track them with persistency. The scientists have shared their findings with Microsoft and Apple since November 2018, but it looks like not much fixing action has taken place since then. The tracking happens through the advertising channels that are used by BLE (Bluetooth Low Energy) devices to announce their presence to other nearby devices for the purpose of communication. As these channels are public for practical reasons, they are changed through randomization periodically so as to avoid tracking.
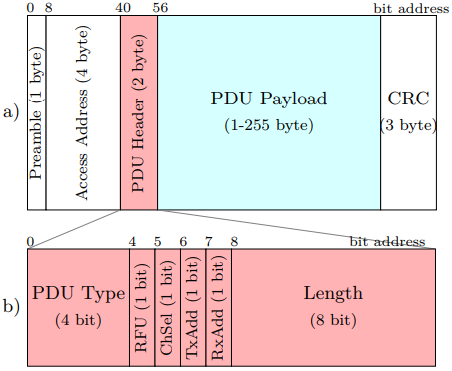
However, the researchers have developed an online algorithm called “address-carryover”, which monitors the identifying tokens and the random addresses, following the device persistently. There’s no need for decryption, as the advertising traffic is unencrypted anyway, and with the Bluetooth 5 specification, there’s no need for the sniffer to be near the target either. The trick for the algorithm is that it can identify specific devices and create a pseudo-identity based on the custom data structures that are contained in their transmission advertising events. These identifying data structures can be found either at the raw PDU Payload and its isolated byte sequence or by breaking it down and analyzing its metadata elements.
image source: petsymposium.org
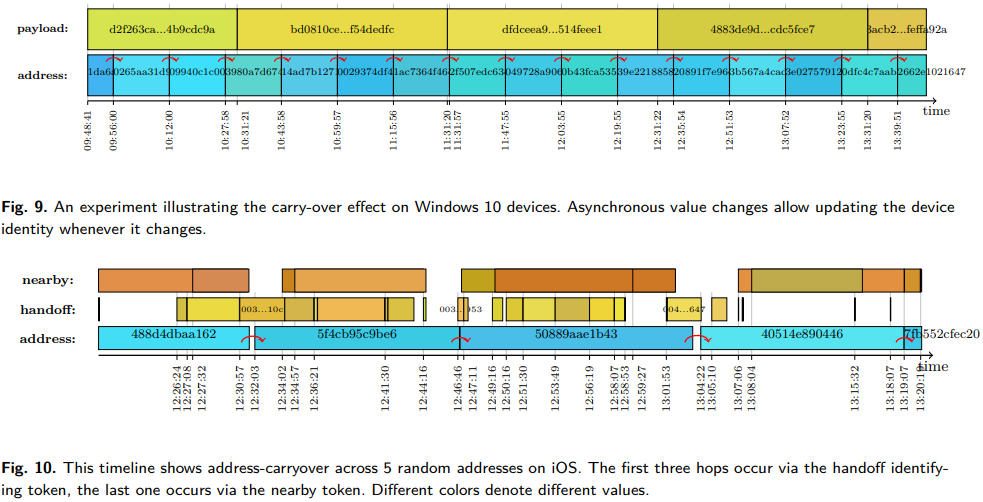
A key factor for this to work is that the changing of the identifying tokens and the randomization procedure does not happen simultaneously, so the algorithm hops from one known platform of identification data to the next, ignoring what can’t be recognized and correlated to the tracked device. The reason why Android devices are immune to this passive sniffing technique is that they do not send advertising messages all the time, and neither do they use exploitable identification tokens.
image source: petsymposium.org
The recommendations of the scientists to the affected manufacturers include the implementation of address randomization for BLE smartwatch devices and the synchronization of the payload changes with the address randomization. This way, no hopping will be possible as the identifiers will all change suddenly and as a unified set. Another resolution could be to implement reconnection addresses based on the use of IRK (Identity Resolving Keys). Until something gets fixed by Microsoft and Apple, users can simply disable their Bluetooth module. If you need to use it, switch it off and turn it back on again at regular intervals so that it gets new tokens and new address simultaneously, resulting in the sniffers losing it.
Share your comments with us in the dedicated section down below, and help us reach to more people by sharing this post through our socials, on Facebook and Twitter.