Researchers Found Several Cryptographic Flaws in the Telegram App
- A team of university researchers has found four ways to attack Telegram’s cryptography.
- Some of the attacks are theoretically interesting, but not all are simple to execute.
- Telegram has fixed all issues through regular updates but hasn’t released any security advisories.
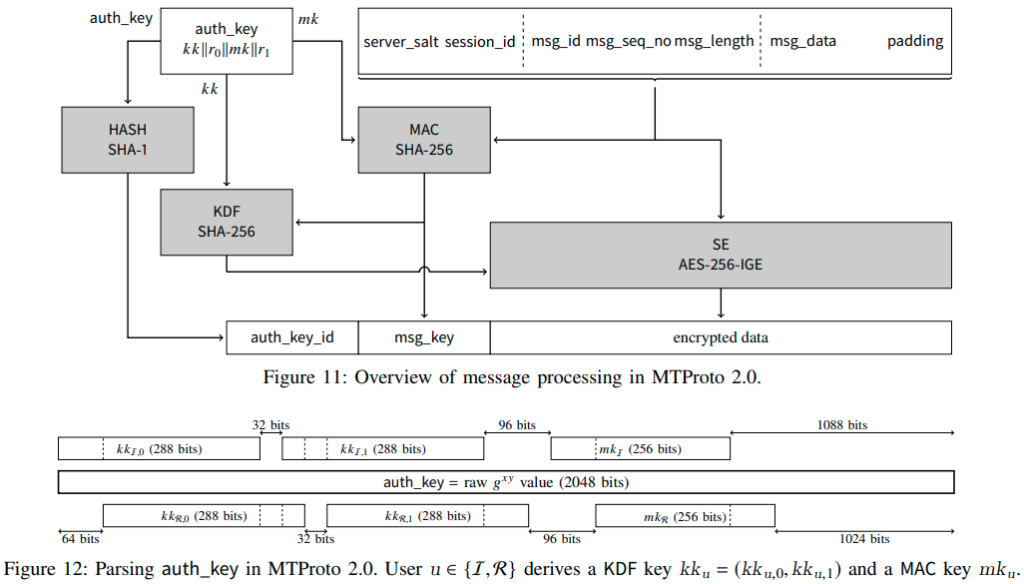
A team of researchers from the University of London and ETH Zurich published a paper describing their methods to four attacks against Telegram, relying on weaknesses in the cryptographic system (MTProto 2.0) of the popular instant messaging app. Since Telegram counts over 500 million monthly users who trust it for secure communications, any findings that threaten to break the encryption protocol are crucially important and have potentially wide and deep repercussions.
The four flaws discovered by the boffins are the following:
- An attacker can reorder the messages that fly from a client to the server of the platform. The attack is trivial to perform and could cause serious trouble to the user by altering the contents of their messages.
- An attacker can detect which messages were encrypted on the client-side and which were encrypted on the server-side. This is an attack that mostly has a theoretical interest rather than a practical significance.
- There’s a way to recover some plaintext from encrypted messages from all Telegram clients (Android, iOS, desktop), essentially devastating the confidentiality of the messages exchanged in the platform.
- A malicious individual can launch a “man-in-the-middle” attack by leveraging the initial key negotiation between the Telegram client app and the platform’s server. The end result would be to impersonate the server to the client, receiving all messages in a readable form.
Telegram has addressed all of the above as the researchers informed the project’s developers prior to the publication of their paper but have chosen not to issue security advisories at the time of patching. Attack scenarios 1, 2, and 4 have been addressed in version 7.8.1 for Android, 7.8.3 for iOS, and 2.8.8 for Telegram Desktop client apps, while attack number 3 was fixed last month.
Besides the fact that the problems have been fixed now, so you don’t need to worry about anything if you’re using the latest version of the app, we should note that the study proved the strength of MTProto on several occasions. What we would suggest is to use third-party (forks) Telegram clients where the implementation of the encryption protocol may not have been done appropriately. If you trust Telegram for your communications, the official app would be your best bet.