Researchers Found Multiple Server-Side Flaws in Agricultural Equipment Giant ‘John Deere’
- Multiple server-side flaws could expose internal data and customer details of ‘John Deere’ and ‘CNH’.
- The vulnerabilities were plugged relatively quickly, but no bounties were ever distributed to the reporters.
- Large agricultural equipment manufacturers didn’t think that having a vulnerability disclosure program online was necessary.
A team of researchers led by ‘Sick Codes’ have “audited” some of the largest agricultural equipment vendors in the world and found several critical server-side vulnerabilities that had the potential to expose the critical assets of John Deere, the Illinois-based manufacturer of a wide range of heavy equipment products, and information on users/customers of Case New Holland (CNH), one of the largest agricultural equipment vendors in the world.
The discovery of the flaws, the subsequent reporting, and the eventual fixing took place months ago. However, the group of researchers has just published more details on the topic given the opportunity of the DEF CON 29 hacker convention. A summary of the discovered flaws is given below:
- Cross-site scripting (XSS) flaw in the reset password function of John Deere’s Account Portal, allowing a remote unauthenticated attacker to execute DOM-based XSS attacks via the ‘forgetUser?TARGET=’ argument.
- Cross-site scripting (XSS) vulnerability in the registration function of John Deere’s Account Portal, allowing a remote unauthenticated attacker to execute DOM-based XSS attacks via the ‘registration?SRC=’ argument.
- Cross-site scripting (XSS) vulnerability in the registration function of John Deere’s Account Portal, allowing a remote unauthenticated attacker to execute DOM-based XSS attacks via ‘com.deere.u90950.webregistration.view.servlets.StandardRegistrationAddServlet?EM_MandatoryPhone=’ argument.
- Cross-site scripting (XSS) vulnerability in the registration function of John Deere’s Account Portal, allowing a remote unauthenticated attacker to execute DOM-based XSS attacks via the ‘SignInServlet’ page.
- An HTTP request smuggling issue in John Deere’s qual.contest.deere.com, adds-eu.deere.com, admin.qual.contest.deere.com subdomains, potentially allowing a remote unauthenticated attacker to bypass front-end security controls.
- A misconfiguration of the ‘Pega Chat Access Group’ portal in the Pega platform deployed by John Deere, potentially leading to unintended data exposure and data exfiltration.
- SQL injection flaw in John Deere MachineBook administration panel, allowing a remote unauthenticated attacker to log into the database and access internal data such as employee details and machine information.
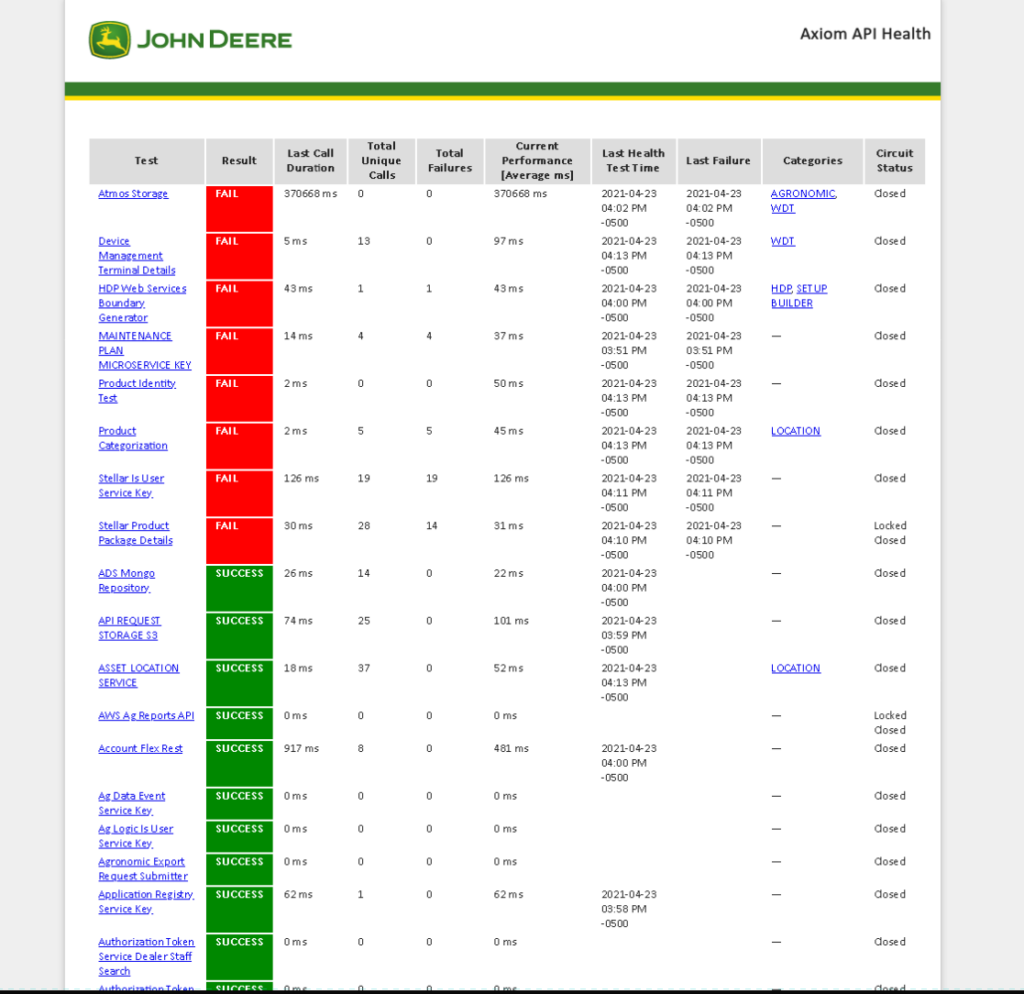
- Unprotected Primary Channel flaw in the John Deere website allowing a remote unauthenticated attacker to view mission critical health tests related to all *.deere.com assets.
- A DOM-based XSS flaw in the John Deere Supplier Invoice Login Servlet & John Deere Supplier Invoice Purchase Order Servlet pagesm allowing a remote unauthenticated attacker to launch assaults via the Supplier Invoice portal.
- SQL Injection flaw in the in the John Deere Supplier Invoice Purchase Order Servlet pages allow a remote unauthenticated attacker to perform SQLi injection on the (Purchase Order) form field which returns a response containing the executed IBM DB2 SQL query.
- A Remote Code Execution (RCE) Vulnerability in the John Deere Supplier supportportaldevr14.deere.com/axis as it was afflicted by AXIS RCE CVE-2019-0227
- An exposed JavaMelody monitoring server of the Case New Holland (CNH) painel360.cnhindustrial.com, allowing an unauthenticated remote attacker to view session data of all current website users including cookies for authentication, full name, HTML page contents of current viewing page, IP address, location, user ID number and session count. An attacker can login as any user that is using the website.
- A username enumeration vulnerability in the Case New Holland (CNH) Azure username API https://euapidevportpwbapp02.azurewebsites.net/api/auth?email= allows an unauthenticated remote attacker to see the user id number, permission level, user roles, username, first name, and last name, exposing critical PII (personally identifiable information) of any known user of the CNH portal.
- An exposed Sidekiq server containing Case New Holland (CNH) running Sidekiq version 3.2.12 storing data synchronization queues for cnhi-nz-rails-server & cnhi-nz-rails-server-uat allows an unauthenticated remote attacker to manipulate internal data queues.
The researchers provided a PoC (proof of concept) for each of these flaws, and the fixes came pretty quickly (in about a week). However, John Deere had no vulnerability disclosure program in place, and decided not to publish any details about the findings, how they may have affected the users of their websites and online services, and also for how long users remained at risk of having mission-critical or personal details leaked.
For a company that sells six-figure autonomous farm vehicles, lacking a solid cybersecurity and bug disclosure program is irresponsible, to say the least.
As ‘Sick Codes’ told us during a private discussion following the disclosure of the above:
John Deere has since launched a vulnerability disclosure program on HackerOne and has already received 62 reports from 19 hackers. This means the future cybersecurity perspective for the firm and its clients is now much better, courtesy of ‘Sick Codes’ and his team, even if they never got a bounty for their reports.