Researchers Find Malware Loaders Inside WAV Audio Files
- Malware hiding in WAV audio files is the latest trend, targeting audiophiles and music enthusiasts.
- The actors are sending the malicious files via email spamming, or upload them on pirate platforms.
- The same method of obfuscation and embedding can be used in other file types as well.
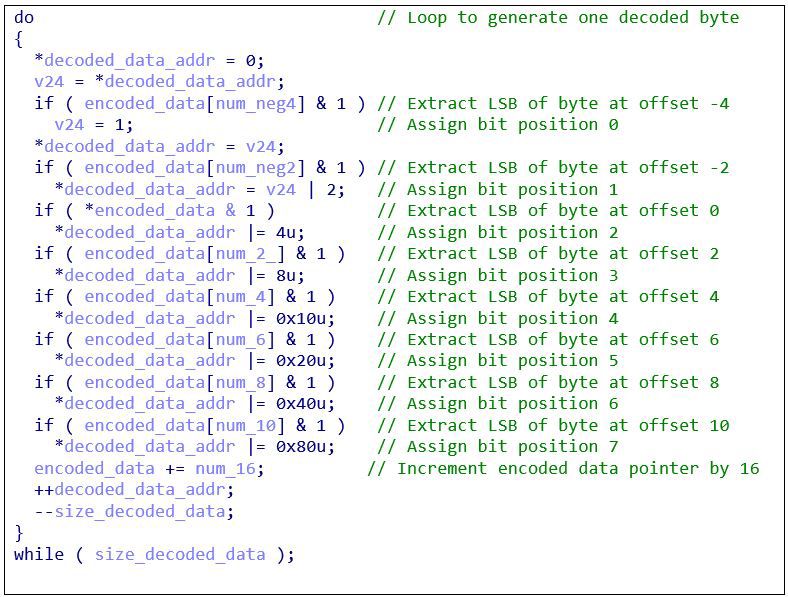
Researchers from BlackBerry Cylance have found malware loader, decoding, and execution components embedded inside WAV audio file data. The malicious code is hiding very nicely inside the structure of the file, as its embedding and obfuscation aren’t leaving much margin for detection. Once a victim tries to playback the file, they may get a static white noise, or they may listen to the expected audio without any glitches whatsoever. It depends on whether the actors even bothered to add the music/audio or not. Other than that, there’s no indication that something is off with these nasty audio files.
During their investigation, the researchers have noted two payloads that are delivered this way. One of those is a Metasploit code that helps them establish a reverse shell, while the other one is a “classic” XMRig/Monero crypto-jacker. As WAV files can concern a wide range of things, malicious actors are delivering them in various ways. Email spamming is a standard method. Others prefer to upload them onto music piracy platforms that don’t review user uploads or don’t have a way to figure out what code is hiding inside the audio files.
Source: Cylance Blog
The way the actors add the malware code is not corrupting the structure of the WAV container, so the same method could be used for other filetypes as well. The reason why they might have picked WAV could be because this type usually results in larger files, and so the addition of “extra code” goes unnoticed more often than not. Remember, WAV is a format that is used for raw, uncompressed audio, which is preferred by those who are going for maximum sound quality over convenience. However, this results in particularly large audio files, up to ten times that of the corresponding MP3 file.
This case goes to show that threat actors are able to put sophisticated ideas into practice, and they are increasingly relying on highly obfuscated code. The WAV malware is obfuscated using a combination of steganography and encoding techniques, and it maintains a separate execution context that doesn’t affect the host file while staying perfectly concealed. Since we have started seeing such advanced creations, we are doomed to having to deal with even more sophisticated threats in the near future. Malicious actors will continue to perfect their obfuscation tools and techniques, and combining many of them is one great way to achieve it.
Are you an audiophile who only uses high-fidelity WAV files? Let us know of your preference in the comments down below, or on our socials, on Facebook and Twitter.