Researchers Discovered Novel Way to Extract Secrets From Intel and AMD Chips
- A team of university researchers has developed attack methods that can leak info from the micro-op cache.
- This is taking place before the speculative execution step, so all Spectre mitigations are essentially bypassed.
- Seeing this fixed or even lightly mitigated is highly unlikely, as the risks of exploitation are mostly theoretical.
A team of researchers from the University of Virginia and the University of California, San Diego, has discovered a way to extract “secrets” from the micro-op cache inside Intel and AMD processors while bypassing all Spectre protections that have been incorporated over the years. The boffins have reverse-engineered many undocumented features of the internal micro-ops used in modern chips and managed to develop three attack methods that would result in stealthy data leaks.
First, there’s a cross-domain attack that takes place across the user-kernel boundary. The second is a cross-SMT thread attack that transmits secret data across two SMT threads via the micro-op cache. And the third is a transient execution attack that leaks secrets that are accessed along a misspeculated path, which is where the Spectre mitigations are bypassed.
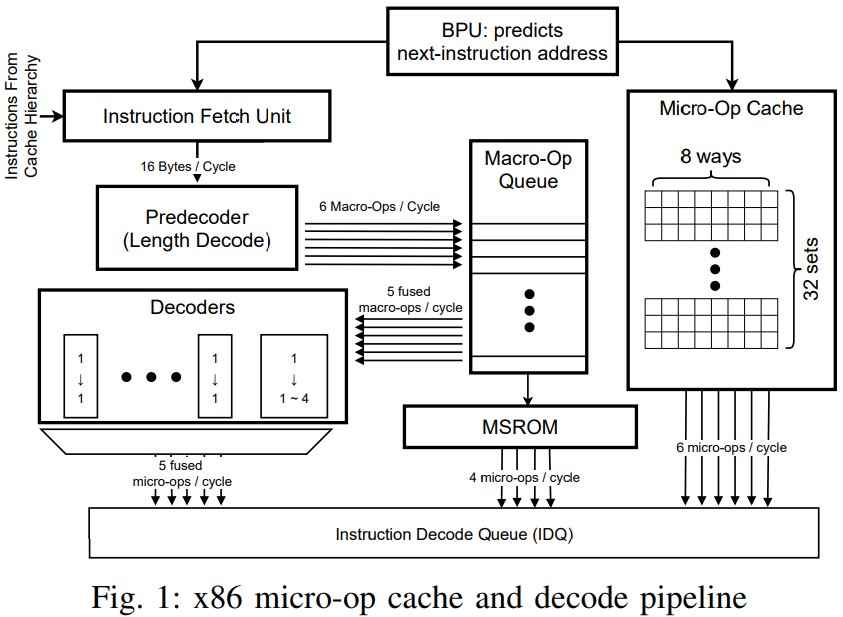
To put this simply, micro-op caches are an internal place in the processor where sensitive information is stored temporarily before execution, awaiting security checks. This was added onto modern chips to improve their performance, as the micro-op cache holds small instruction chunks that can help speed up speculative execution. Specter attacks disrupted that last step and gained access by diverting the instructions to a different path. In this latest discovery, the data disruption happens before the instructions are approved for entering speculative execution, so it is very effective even if inevitably not as useful.
The researchers suggest a couple of potential mitigations, like flushing the micro-op cache at domain crossings, performing counter-based monitoring, or introducing privilege level-based partitioning. As it’s always the case with attacks of this kind, fixing them isn’t simple at all because the flaws are intrinsic to the chip’s operation and design. Sure, disabling speculative execution would address everything, but the drop in performance would be very noticeable, and the risk that will be addressed as a result isn’t that severe.
These attack methods aren’t easy to weaponize or to exploit in a meaningful way, even if they theoretically affect billions of systems out there. From what we understand, this discovery concerns all x86 chips made after 2011, although the researchers focused on Intel Skylake and AMD Zen microarchitectures in their study. Due to the scope and the balance between security gains and performance losses, we wouldn’t expect to see an aggressive response to this discovery by Intel or AMD. Still, the paper offers an interesting perspective for chip engineers to consider in the future nonetheless.