Researchers Discover New Ways to Launch Side-Channel Attacks Against Intel CPUs
- Intel CPUs relying on the ring bus are vulnerable to perilous side-channel attacks.
- The researchers who discovered them have released two examples with PoC code.
- Intel played down the impact and updated its guidelines on mitigating these threats.
A team of researchers at the University of Illinois have discovered and detailed in a report how a novel method for a side-channel attack against a wide range of Intel CPUs would work. The title of their paper, titled “Lord of the Ring(s),” indicates that the side-channel attacks rely on the ring bus of the processor, which is basically an integral part of the CPU’s architecture that helps in connecting internal components.
This is a vastly undocumented piece in Intel CPUs, which the team managed to reverse-engineer to figure out what intercommunication protocols it deploys.
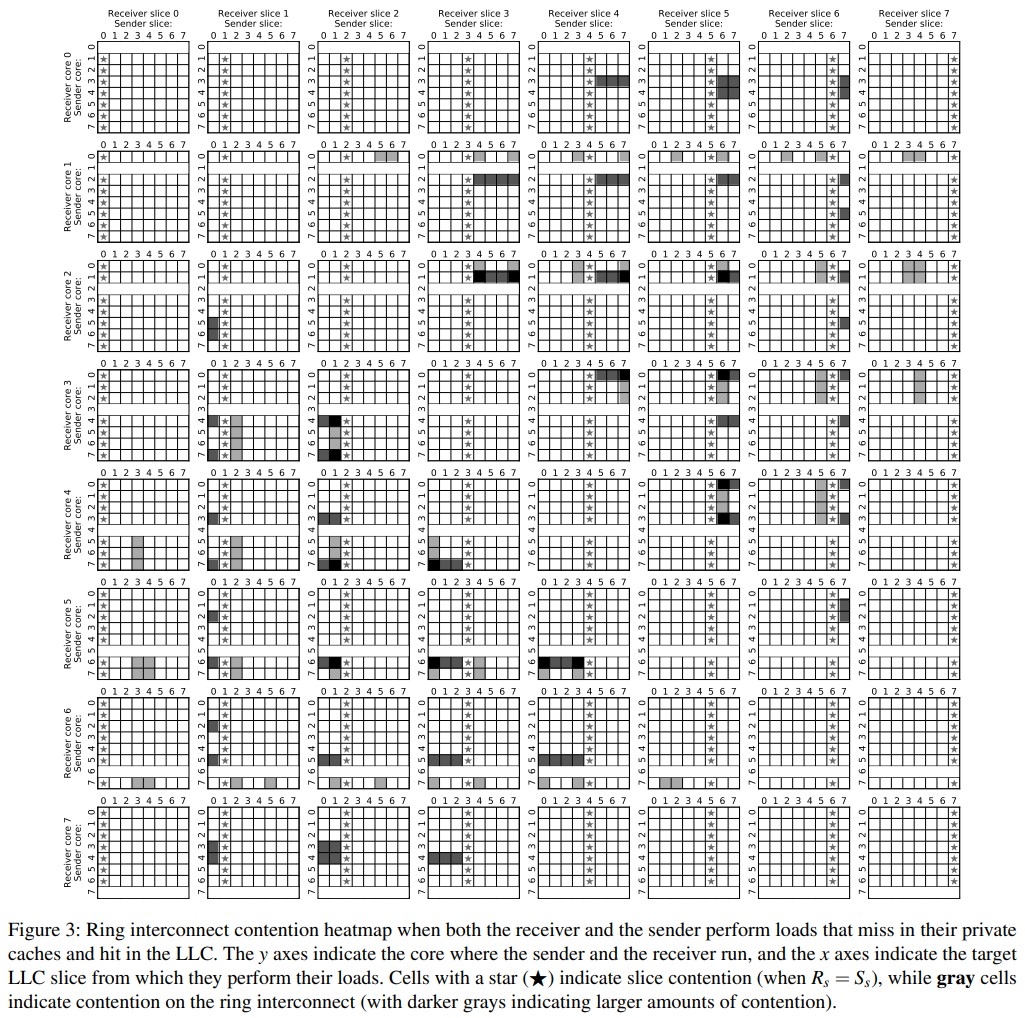
With this knowledge, the researchers built a cross-core covert channel over the ring interconnect with a capacity of over 4 Mbps from a single thread. They also leveraged the fine-grained temporal patterns of ring contention to infer a victim program's secrets.
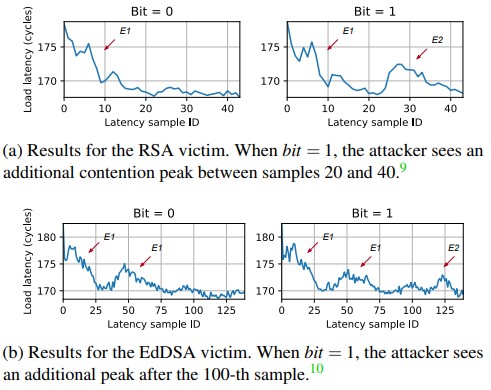
The team has now published two examples of fully-working side-channel attacks that exploit ring contention with their source code. The first attack leaks key bits from vulnerable EdDSA and RSA implementations, and the second infers the precise timing of keystrokes typed by the target user.
As it becomes easily understood, the processors that are vulnerable to these attacks are those which use the ring interconnect system. So, AMD CPUs that use their own proprietary technology called “Infinity Fabric” aren’t vulnerable, and Intel CPUs that use the “Mesh” interconnect method aren’t vulnerable either.
Unfortunately, most Intel CPUs rely on the ring bus system, and only some Xeon and Skylake server processors released in mid-2017 begun using the mesh interconnect. So, considering that almost all Intel users are affected, the next question is how serious this is and whether you should worry about it.
Intel says we shouldn’t worry about it too much - or at least more than other “traditional” side-channel attacks that haven’t brought any real weaponization potential. For Intel, the findings are still significant, but the impact is generally considered minor.
Still, though, Intel published mitigation guidelines mostly relying on constant time code and compiler optimizations and on ensuring that the runtime and code access patterns are independent of secret values. Moreover, there’s a generic “best practices” guide for strengthening resistance against side-channel attacks in general.
These, though, are all for code-writers and software developers. If you as a consumer are worried about this all, there’s nothing you can do about it besides replacing your CPU with a newer model using technologies that haven’t been reverse-engineered yet.