Researchers Discover Multiple Vulnerabilities in Synology SRM
- Cisco has discovered several critical remote flaws in Synology SRM and developed exploit chains.
- The vendor has fixed the reported vulnerabilities via a patch that is already available.
- The flaws open up multiple channels of exploitation and practically result in ssh-ing the target router.
Researchers of the Cisco Talos team have discovered a number of critical vulnerabilities in the Synology Router Manager (SRM), which is an admin tool enabling Linux users to connect to Synology routers. As the report details, the identified flaws could be exploited by hackers in order to execute remote code on the device, access sensitive network information, and communicate with other devices connected to that same network.
The flaws that were discovered, reported, and fixed via a patch are the following:
- TALOS-2020-1058 / CVE-2020-27648
- TALOS-2020-1059 / CVE-2020-27650
- TALOS-2020-1061 / CVE-2020-27652
- TALOS-2020-1071 / CVE-2020-27656
- TALOS-2020-1060
- TALOS-2020-1065 / CVE-2020-27654
- TALOS-2020-1086 / CVE-2020-27658
- TALOS-2020-1087
- TALOS-2020-1051 / CVE-2019-11823
- TALOS-2020-1066 / CVE-2020-27655
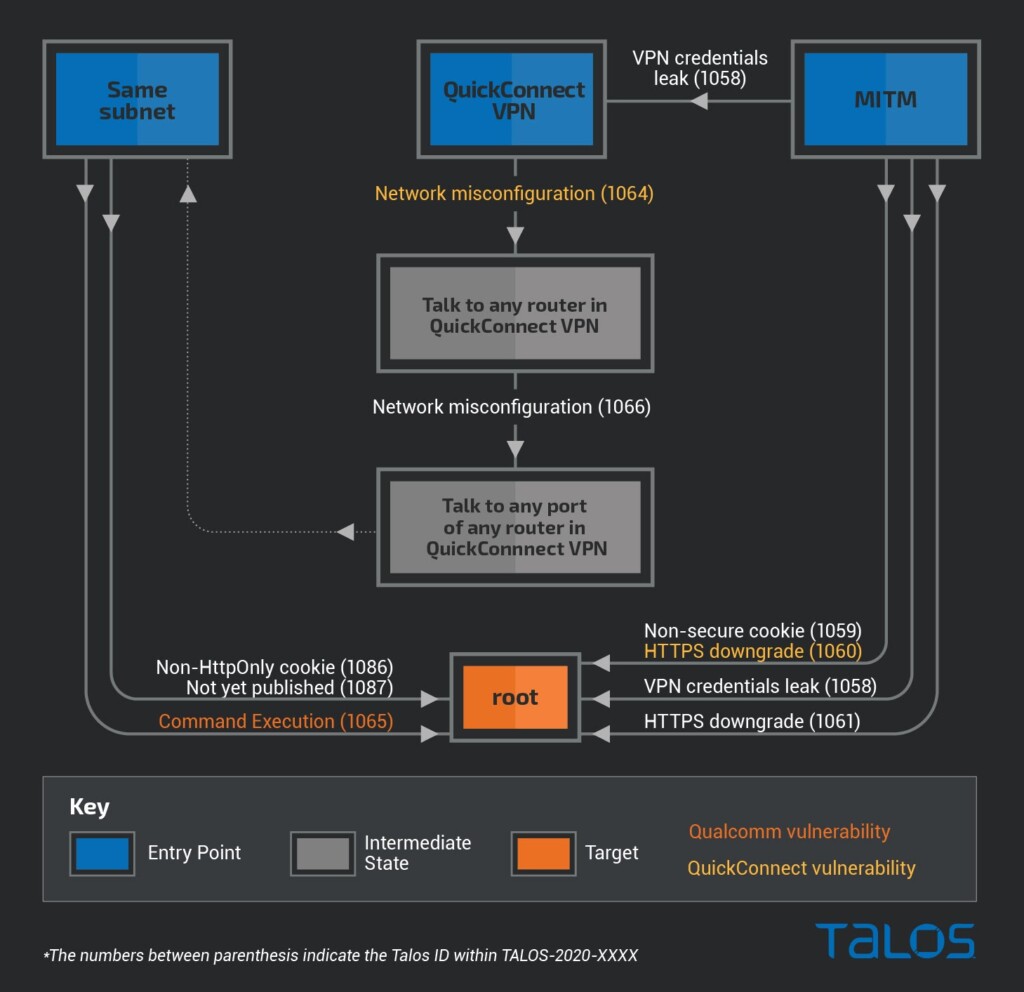
In the following diagram, the researchers illustrate the exploit paths for each of the four flaws, as well as others. The vulnerability that affects the Qualcomm LBD service (TALOS-2020-1065) has also been acknowledged and fixed by the chipmaker via an update.
As it becomes clear from the above diagram, the attacker can use various starting points like the LAN, QuickConnect VPN, or a point between the router’s WAN interface and the target host (man in the middle). In all cases, there is more than one way to get root privileges on the target router without having to authenticate. Then, by enabling SSH, a wide range of exploitation potential opens up.
Related: Facebook Could Disclose Any Bugs It Finds on Third-Party Apps in 21 Days
The version that’s affected by most of the above flaws is Synology SRM 1.2.3 RT2600ac 8017-5. Additionally, the first four critical flaws given in the previous list affect Synology DSM (Disk Station Manager) version 6.2.3 25426 too. Finally, TALOS-2020-1065 also affects Qualcomm LBD version 1.1. Since all of the above flaws have been plugged by fixing patches, users are advised to update their router software as soon as practically possible.
Synology is a Taiwan-based NAS specialist, while the company also recently expanded to the space of Wi-Fi routers. In general, it’s products are deployed in professional environments, which makes the present report even more important. Backup systems, virtual storage, file sharing, etc., have all exploded since the beginning of the year, so using an older and vulnerable version of the DSM or SRM is highly risky right now.