Report Claims Hacking Critical US Infrastructure Would Be Fairly Easy
- Researchers have discovered numerous cases of accessible and controllable ICS in the United States.
- These systems can control water treatment systems, oil wells, power plants, and more.
- Anyone could have found and accessed these systems, and it’s by luck that nothing bad has happened.
Critical infrastructure includes water supply services, the public health system, police, military, fuel supply, energy generation, telecommunications, financial services, shopping, railway networks, natural gas supply, nuclear power stations, harbors, and everything else that keeps a country’s economy on its feet. Take one piece out, and you have a serious problem to deal with. That said, one would naturally assume that protecting critical infrastructure would be the utmost priority of all governments in the world. Still, a recent report that looks into the situation in the United States claims that reality couldn’t be farther from this assumption.
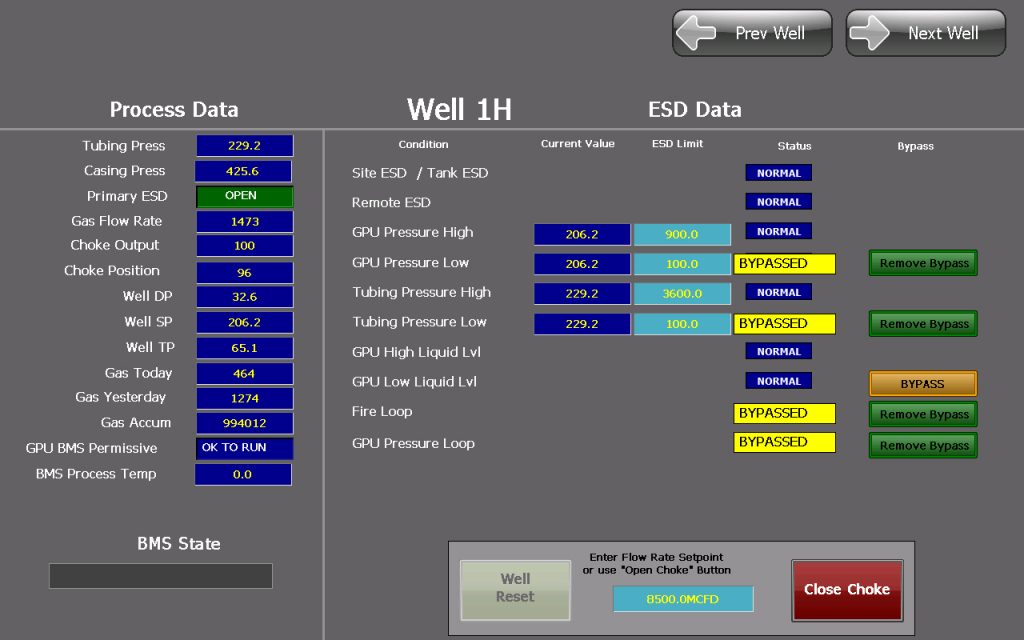
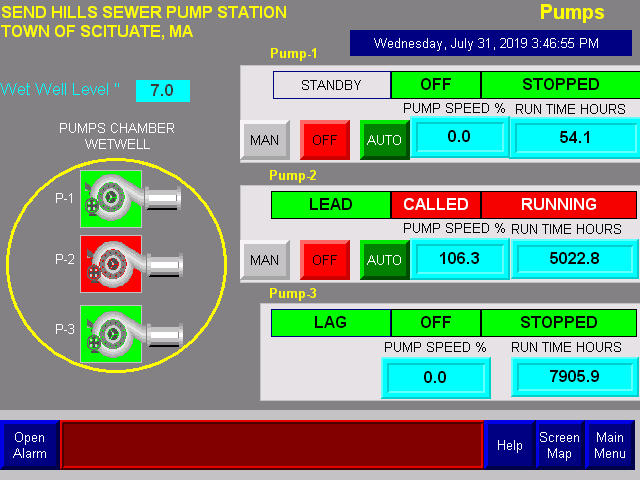
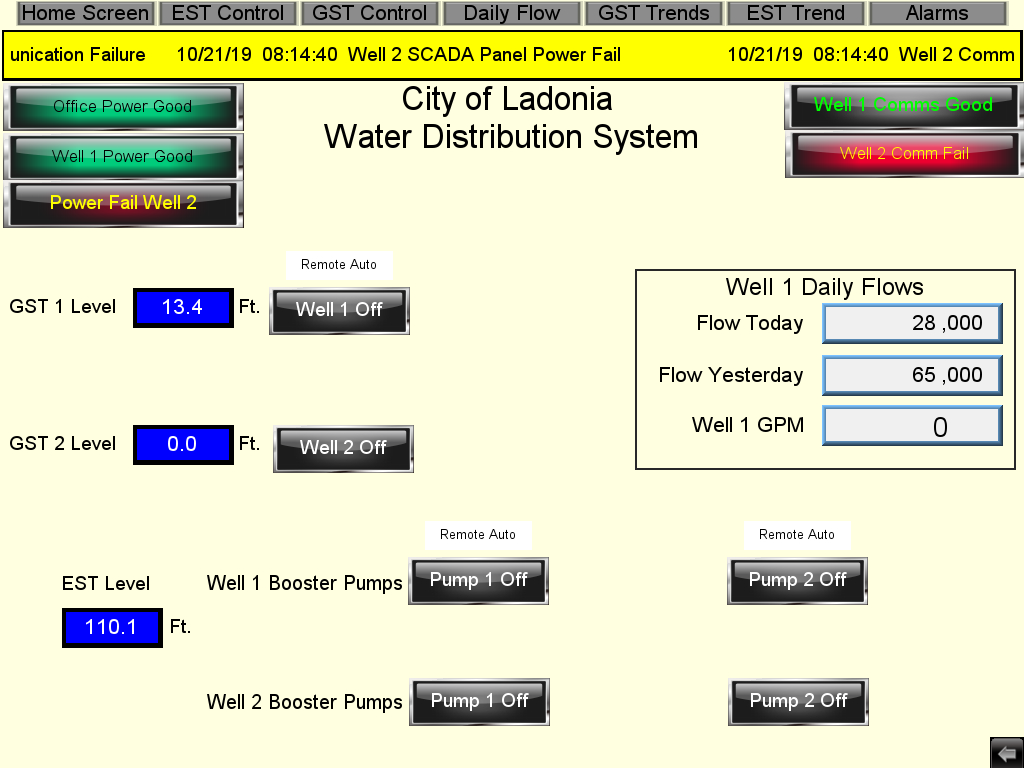
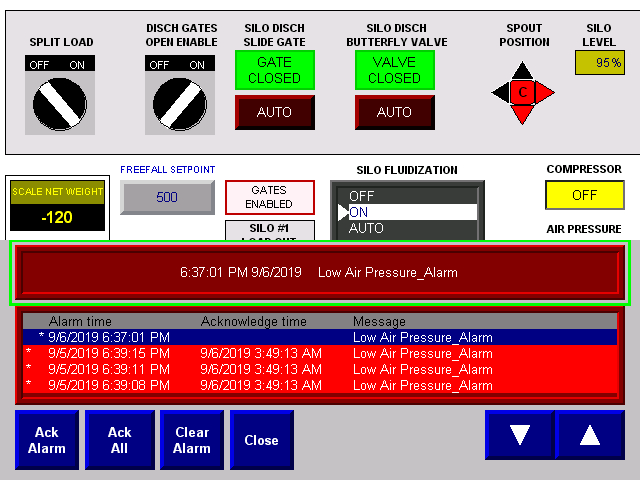
As the report details, a wide range of critical public and private infrastructure is using obsolete ICS (Industrial Control Systems) that have no regard for cybersecurity and are extremely vulnerable to a rich set of potential attacks. The researchers scanned for open ports in the US IP address range and found numerous unprotected and accessible ICS terminals. These are mainly deployed in the energy and water industries, offshore and onshore oil wells, water treatment, and water distribution services. To their surprise, they were able to just take control of the systems and do whatever they wanted.
Source: CyberNews
Source: CyberNews
Source: CyberNews
Source: CyberNews
Whatever problem the researchers identified, they responsibly reported it to the CISA and CERT, as well as the public and private entities responsible for each system. Thus, access to these systems has been secured now. Still, many others may not have been detected and could remain vulnerable. With them, thousands (if not millions) of people could be affected or even have their health endangered. For example, through these ICS units, an actor could potentially shut down the disinfection process in a water treatment or supply plant, silence alarms on oil wells, and let the pressure build-up, or adjust the sewage flow speeds to overflowing levels.
All this sounds scary, and it is the reality in pure form, without any dressings to make it more dramatic. The trust that you have towards the public and privacy critical infrastructure services is based on unsubstantial suppositions. With Chinese, Russian, Iranian, and Korean hackers having the skills to take control of these industrial control systems, one has to wonder why we haven’t seen much happening on that part, and why anything that happened was limited to shutting down electric power. The only possible answer to this question is that state actors don’t feel like harming innocent civilians as this was never their goal. Thus, these people remained safe not thanks to their government, but thanks to the ethical barriers of foreign threat actors.