Renewed Phishing Campaign by APT29 Targets European Diplomats with Advanced Malware
- APT29 uses deceptive tactics to deploy a new malware loader and an updated variant of WINELOADER backdoor.
- Emails purportedly sent from European Ministries of Foreign Affairs invite recipients to wine-tasting events.
- Embedded malicious links either redirect to legitimate ministry websites or initiate malware downloads.
A sophisticated phishing campaign orchestrated by APT29, a Russian-linked cyber-espionage group also known as Cozy Bear or Midnight Blizzard, is targeting diplomatic entities across
Europe via advanced malware tools disguised as invitations to seemingly benign events like wine-tasting events.
Cybersecurity researchers at Check Point Research (CPR) have uncovered that the primary targets are European diplomatic entities, including Ministries of Foreign Affairs and foreign embassies in Europe, which have been targeted since January 2025. Limited evidence suggests some activity extends to diplomats in the Middle East.
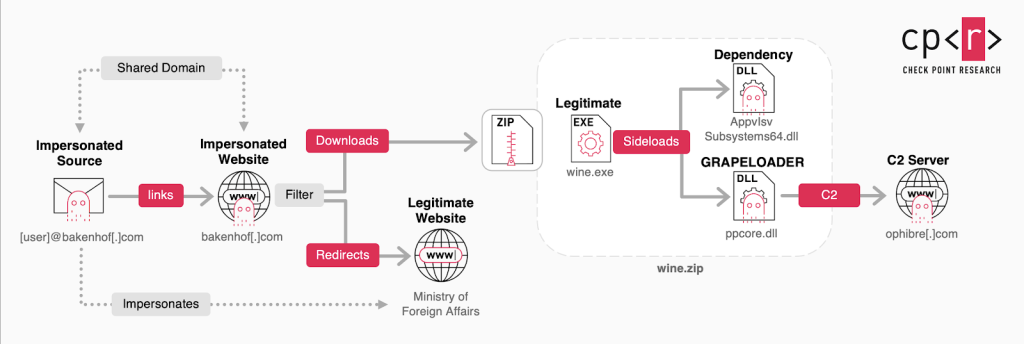
Cybercriminals are leveraging phishing emails to distribute a new, advanced malware loader, dubbed GRAPELOADER, along with an updated variant of the well-known WINELOADER backdoor malware
APT29 employs highly targeted phishing emails sent via domains such as bakenhof[.]com and silry[.]com. These emails often use subject lines like “Wine Event” or “Diplomatic Dinner” to lure recipients into clicking a malicious link. For enhanced success rates, the attackers launched multiple waves of emails to victims who ignored initial attempts.
The malicious link downloads a zip file named wine.zip, which contains components to execute the GRAPELOADER malware. To avoid detection, the link only triggers a downloaded payload under specific conditions, such as predetermined times or geographic locations.
GRAPELOADER is downloaded via these phishing links. This tool stands out for its enhanced stealth and functionality designed for persistence, host fingerprinting, and payload delivery.
It establishes mechanisms to ensure execution after system reboots by modifying registry settings and collects basic system information (e.g., user name, host name, process IDs) and sends it to a Command and Control (C2) server for further instructions. It also facilitates the delivery of further malware, including WINELOADER, as part of a multi-stage attack chain.
Key technical features of GRAPELOADER include advanced anti-analysis tactics such as dynamic API resolving, DLL unhooking, and memory-based shellcode execution. Such methods help the malware evade detection by security tools like antivirus or endpoint detection systems.
The updated WINELOADER malware variant, identified as vmtools.dll, further complicates detection efforts by introducing:
- Advanced evasion techniques such as code mutation and structural obfuscation.
- RC4-based encryption for maintaining secure communication with its C2 server (bravecup[.]com).
- Improved unpacking routines that mimic legitimate processes, often employing DLL side-loading.
The payload collects environment information, encrypts it, and sends it back to the C2 infrastructure for further exploitation.
APT29 is widely connected to previous high-profile cyber espionage campaigns. This campaign reuses themes akin to WINELOADER campaigns observed in 2024. The threat actor is also known for its connection to the SolarWinds supply chain attack.