RedCurl Deploys Novel QWCrypt, Moving from Cyber Espionage to Ransomware Attacks
- Cybersecurity researchers observed the RedCurl hacking group deploying a new ransomware strain.
- The previously espionage-focused threat actor engaged in its first ransomware attack.
- However, the initial infection vector remains phishing emails containing IMG files disguised as CVs.
The cybercrime landscape is witnessing a change in strategy by RedCurl, a Russian-speaking hacking group previously known for its corporate espionage operations. For the first time, the group has been linked to a ransomware campaign involving novel ransomware strain QWCrypt.
Targeting organizations across regions such as Canada, Germany, Norway, and the United States since 2018, RedCurl has traditionally focused on espionage, relying on spear-phishing emails and human resource-themed lures to infiltrate systems.
However, recent activities reveal a pivot in their approach, with ransomware now being their arsenal's newest addition, according to a report by Romanian cybersecurity firm Bitdefender.
The attack method employed remains rooted in the group's established phishing tactics – fake CVs presented as mountable ISO disk images are used to deliver the QWCrypt ransomware.
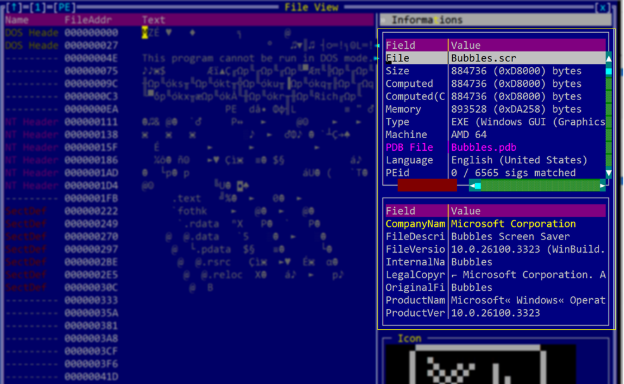
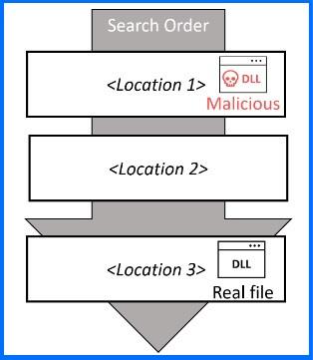
Disguised files exploit DLL side-loading techniques, leveraging legitimate Windows processes to install malicious loaders like "RedLoader,” a tool previously observed in phishing campaigns earlier this year.
Once installed, the loader executes various stages of malware, culminating in the deployment of QWCrypt. Bitdefender uncovered that QWCrypt encrypts data hosted on virtual infrastructures, even rendering virtual machines unbootable.
The objective is to cause widespread disruption with minimal effort by targeting virtualized environments critical to modern business operations.
The ransomware employs advanced techniques such as Bring Your Own Vulnerable Driver (BYOVD) to neutralize endpoint security software before encryption.
Further, the ransom note left on compromised systems borrows heavily in design and content from groups like LockBit, HardBit, and Mimic. Interestingly, no associated leak site has been identified yet, leaving questions about RedCurl’s ultimate motives.
The group’s ability to effortlessly transition between espionage tactics and ransomware attacks highlights its growing sophistication. However, their use of tactics such as rehashed ransom note text also raises questions about whether this campaign aims solely for extortion or has alternative motives.