Recent Cryptojacking Campaigns Use a New Malware Strain Called ‘Norman’
- Researchers have captured a new cryptomining malware that has not been seen in the wild before.
- This new malware is called 'Norman' and features a rich set of obfuscation and hiding methods.
- The XMRig cryptominer is focused on Monero, and is particularly effective in its mining activity.
According to a report by the Varonis security research team, the latest ongoing cryptomining campaigns are supported by a new malware variant that they named 'Norman'. This new malicious piece of software uses novel techniques to stay hidden from researchers and AV tools while boasting high mining performance. Most of the variants that were analyzed by the researchers relied on the DuckDNS service for their communication with the C&C server, and all of them are XMRig-based that focus on the mining of the Monero cryptocurrency.
The investigation of Varonis started with their forensics team responding to a question by one of their clients who informed them of suspicious and abnormal network activity. Upon investigation, the team found that the initial infection had taken place over a year ago, and by the time of the discovery, all of their client’s servers and workstations have been infected. This goes to show how well Norman can stay hidden in the network, as the infection had actually been materialized through a rich set of tools, including various variants of the Norman cryptominer, password dumping tools, PHP shells, and other remnants.
image source: varonis.com
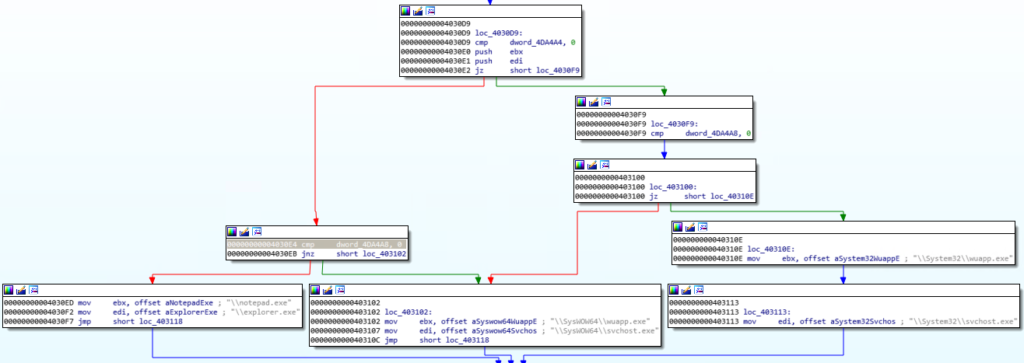
Norman is executed through a file with the name “svchost.exe” which was compiled with the NSIS system. The archive contains various payload DLLs and data files which make its injection possible. To avoid detection, svchost.exe creates a mirror process of itself and terminates, while the second process undertakes the role of launching either Notepad or Explorer, and inject the cryptominer into them.
Depending on whether the target system is a 32-bit or 64-bit OS, Norman follows a different process of getting launched. If the user opens the Task Manager to check what’s going on with the resources, the process that was launched by the malware is terminated. Once the Task Manager is closed, the process is relaunched and the miner is re-injected.
image source: varonis.com
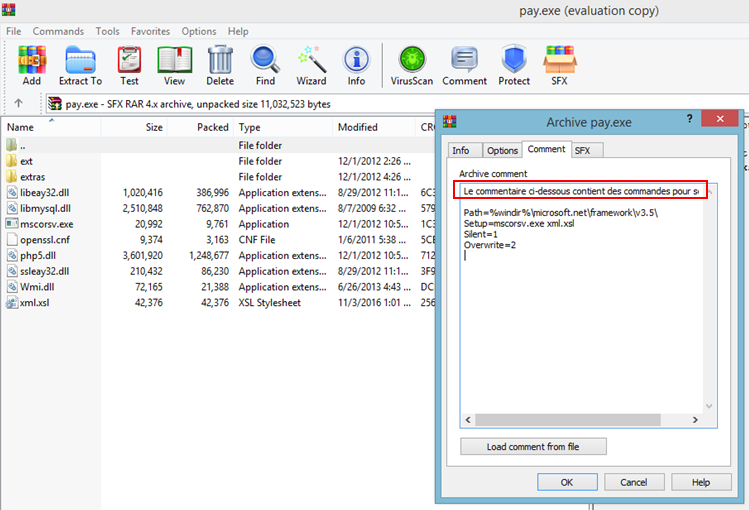
Based on the analysis of the samples, the Varonis team believes that Norman originates from France, as the comments in the SFX file are written in French, and the WinRAR version that was used for the bundling of the archive was also French.
To stay protected against threats like this one, you should keep all your software up-to-date, monitor network traffic and Web proxies and set up specific and targeted restrictions by deploying a firewall. Also, don't forget to monitor the CPU activity on your computers, monitor DNS, and use powerful AV tools.
Have something to say on the above? Feel free to share your thoughts with us in the comments down below, or on our socials, on Facebook and Twitter.