Razy Trojan Altering the Browsing Experience to Steal Cryptocurrency
- Razy is delivering fake search results, fraudulent ad banners, and swindling offers.
- The extension is monitoring the user browsing activity and hits when the right time comes.
- People are advised to check the list of the installed browser plugins and be suspicious with all banners.
As reported by the Kaspersky Lab, the Razy Trojan is suspect of a new set of browser extensions that are capable of altering the browsing reality and experience for their users, with the sole purpose of stealing cryptocurrency from them. The Razy extensions cover Google Chrome, Mozilla Firefox, and the Yandex Browser, getting installed with the deceptive names of “Chrome Media Router”, “Firefox Protection”, and “Yandex Protection”. In the case of the Chrome, the extension even stays hidden from the installed plug-ins list, so that users don’t realize its presence and activity. In all three cases, the extension is preventing the infected browsers from updating.
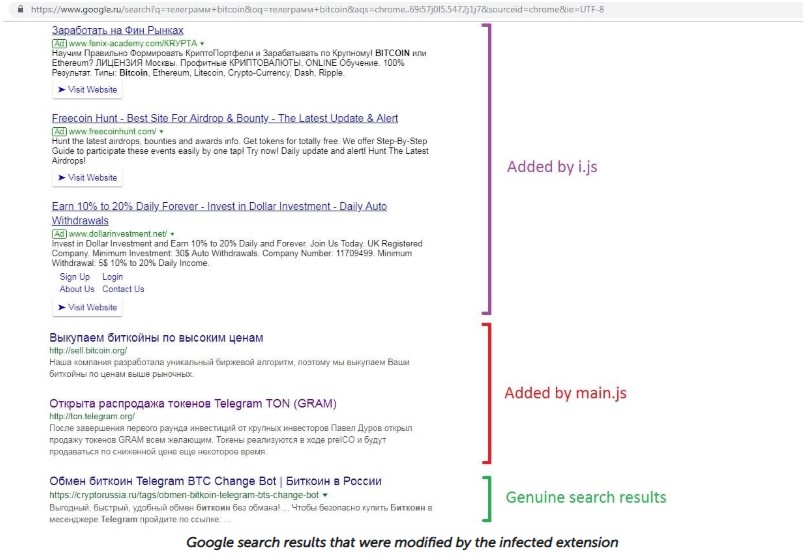
The action is laid out in three areas, all pertaining to the browsing reality that is delivered to the unsuspected users. First, the malicious extensions insert fake Google and Yandex search results that point to phishing websites. These false entries are placed on top of the search results, and may even cover the whole 1st page, leaving little room for doubt in the minds of the victims. To maintain a realistic context, these spoof search results are only delivered when the user is entering cryptocurrency-related terms in the search box, as this is the primary target of Razy anyway. This means that the extension is monitoring the user’s browsing at all times, deciding when to strike with fake results, ads, and banners.
Image source: securelist.com
The HTML page modification and the inserting of phishing elements go on, no matter which pages the user is visiting. The extension adds advertising banners containing lucrative cryptocurrency offers or trying to bate the users by indirect offers from fake online surveys and even Wikipedia donations. In all cases, the banners feature QR codes that correspond to the cybercriminal’s wallet. Other examples of fake banners that the Kaspersky researchers unveiled include an advertisement that is displayed on people who attempt to visit the telegram.org website, offering very low-priced tokens and another banner on the Vkontakte social network that is popular in Russia. The first redirects to “ton-ico.network” while the second points to ooo-ooo.info.
Image source: securelist.com
To avoid getting victimized, only trust extensions that come from reliable sources, scan your computer when a new extension pops up on your browser all of a sudden, and conduct regular antivirus and antimalware scans. Do not get fooled by misleading extension names, and always double-check the URL that you are about to click from a banner.
Have you noticed a “protection” extension in your browser? Let us know in the comments below, and share this story through our socials on Facebook and Twitter, so as to help us raise awareness.