Ransomware Hits 110,000 Domains with Exposed AWS Access Keys Due to Cloud Misconfigurations
- Hackers targeted 110,000 domains’ Amazon Web Services environments to search for valuable data.
- Unsecured web apps and misconfigured servers revealed over 90,000 exposed unique variables.
- The actors exfiltrated the data after getting Identity and Access Management access keys to the hosting cloud environment.
Update (August 23, 2024): After talking to AWS representatives, we've updated the following article with additional information and provided further clarification based on a statement from AWS.
A yet unnamed cybercriminal gang’s cloud operation targeted 110,000 domains and leveraged over 90,000 exposed unique variables in environment variable (.env) files that contained sensitive data to compromise multiple organizations and then extort the victims, Unit 42 researchers found. AWS declared that services and infrastructure were not affected by these findings.
The report says 7,000 variables were organizations' cloud credentials, and 1,500 were API keys or passwords for social media accounts, some with account names and authentication secret keys. The rest came from on-premises applications.
Among the multiple security missteps were exposing environment variables, such as various app users and passwords stored on unsecured Web applications and misconfigured servers, using long-lived credentials, and the absence of least privilege architecture.
Reconnaissance and initial access operations relied on The Onion Router (TOR) network, and then the threat actor used VPNs for lateral movement and data exfiltration.
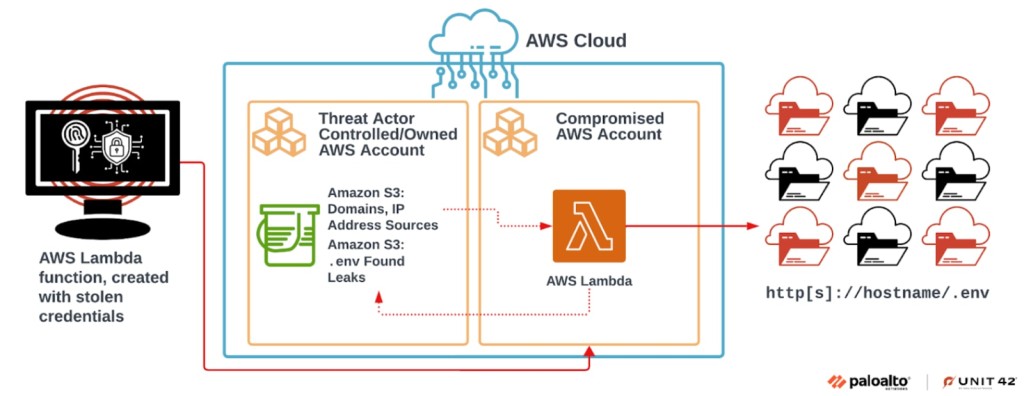
The attackers used various organizations’ Amazon Web Services (AWS) environments. They scanned over 230 million unique targets for sensitive information, identifying exposed AWS Identity and Access Management (IAM) access keys to the hosting cloud environment.
They also searched for Security Token Service (STS), Simple Storage Service (S3), and Simple Email Service (SES) via various discovery API calls, and an API request identified all the existing S3 buckets.
Privilege escalation helped the cybercriminals create new IAM roles with administrative permissions where needed. The threat actors created infrastructure stacks using AWS Lambda and made multiple lambda functions.
Using the S3 Browser tool, which generates various S3 API calls when used, the hackers stole and then deleted S3 bucket objects.
An AWS spokesperson declared the company’s services and infrastructure are not affected by the issues Unit 42 identified, which AWS says were “a result of a threat actor abusing misconfigured web applications—hosted both in the cloud and elsewhere—that allowed public access to environment variable (.env) files.”
The statement continues to say that some of these files “contained various kinds of credentials, including AWS credentials, which were then used by the bad actor to call AWS APIs.” The company mentions that environment variable files should never be publicly exposed or contain AWS credentials, even if kept private.
Customers should follow best practices for IAM to help secure their AWS resources.