Ransomware Groups Are Now Enticing Disgruntled Employees to Deploy the Payload
- Ransomware gangs are luring company insiders who could aid them get inside without much fuzz.
- The short-term accomplices are offered up to a 40% cut, but of course, nothing is guaranteed.
- The newest RaaS operations are being clear about this possibility for collaboration on their kick-off threads.
For ransomware actors, the easy part is the encryption of the files in a compromised machine. The hard part is to get there, and this step supports an entire market of initial access brokers. But after a recent incident involving an insider's collaboration on the target company, ransomware actors realized they could get their payloads into the target a lot easier and cheaper by simply paying a disgruntled employee to do it for them.
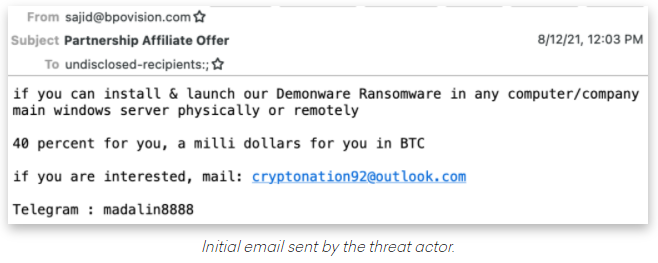
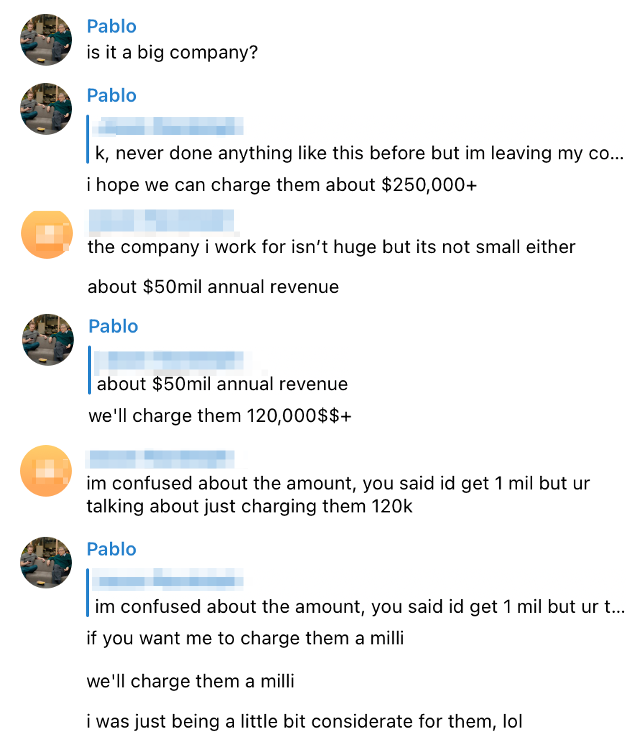
Cyber-intelligence firm Abnormal Security has spotted private messages exchanged between a threat actor and the lured employee, offering them 40% of whatever the victimized company will pay as ransom to the crooks to get the decryptor. In the particular case, the actor discussed the company's size with the researcher who pretended to be an insider in order to set the ransom amount within a realistic scope.
The actor assured the insider that there would be no way for them to be exposed for participating and lose their job, as everything would be encrypted. That includes logs, CCTV footage, and anything stored on the server. The ransomware that was to be deployed in this case was just an off-the-shelf tool called “DemonWare,” which is freely available through GitHub as a demonstration and testing tool.
Although the particular actors phished by Abnormal Security moved with characteristic amateurishness and even exposed their real identity in the process, this is just an example that surfaced online. Other ransomware actors who are a lot more sophisticated and stealthy are bound to be exploiting this peculiar backdoor, as it’s an easy way into corporate networks and one that is very difficult for companies to shut.
In previous years, we have seen cases of employees who were angry with their employer creating accounts on the dark web and offering their help to hackers to launch attacks against their companies. Now, most employees are approached by the actors on LinkedIn.
LockBit 2.0, one of the most active RaaS operations at the moment, includes solicitation for insiders offering very lucrative payouts for insiders that will help their break-in. The also recently-launched BlackMatter RaaS mentions the possibility to purchase access directly from insiders too. This indicates that the ransomware groups are very well aware of this entry point and actively seek to abuse it.