Ransomware Group “Pay2Key” Hit Intel-Owned Habana Labs
- Iranian hackers “Pay2Key” have hit Israeli AI chip developer ‘Habana Labs.’
- The actors have stolen precious stuff such as the domain controller, source code, and internal process info.
- Habana Labs is a promising start-up bought by Intel last year, so the ransom could be a big one.
The Iranian ransomware group known as “Pay2Key” hit Habana Labs, an Israeli start-up that Intel acquired a year ago for $2 billion. The particular actors came into existence fairly recently, and CheckPoint researchers were the first to notice and warn about them.
Two weeks ago, we looked into the “Pay2Key” victim portfolio as the group set up the typical data-stealing extortion payment site, and Israel-based firms were clearly the focus. Now, with the Habana Labs going down, too, the targeting scope of the specific group of hackers is further cemented.
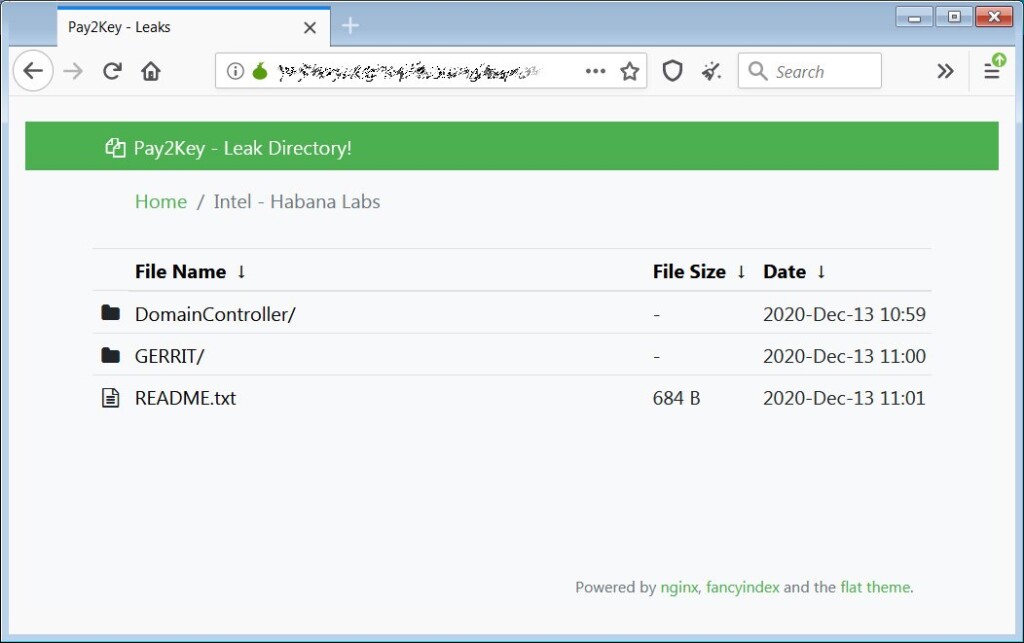
The actors are publishing screenshots from the breach on Twitter and promise to upload more details on the "leak directory" soon. The images show the Habana Labs domain controller, samples of source code, and internal processes, so the infiltration is quite extensive. Possibly, the hackers managed to access parts of Intel’s network as well, but there’s no evidence about that yet.
Habana Labs was founded in 2016 to create AI chips and develop disruptive solutions that will go well beyond what’s available in the market right now. Its AI processors are optimized for deep neural network training and inference deployment in production environments. They are currently operating under Intel, but as an independent company, enjoying the tech giant’s financial support, talent, experience, and customer relations.
This makes Habana Labs an interesting target from ransomware actors like Pay2Key, as they could now extort Intel and ask for a ridiculously large ransom. The hackers have given Habana Labs 72 hours before they initiate the data leaking process, but no amounts were mentioned. BleepingComputer comments that the actors’ main goal may actually not be to make money but to cause business disruption to the Israeli firm.
Although this is likely, it doesn’t match this particular group’s general stance, and neither does it fit the profile created by CheckPoint, which doesn’t link Pay2Key with the Iranian state. Still, though, political motivation doesn’t only come from being state-supported, as nationalism is often found intrinsically in hacking groups.
As for the ransomware itself, the online-bound encryptors that use a hybrid scheme that combines symmetric and asymmetric methods remain uncracked, so there’s no decryption available out there. The more this continues to be the case, the more effrontery the Pay2Key group will demonstrate.