Ransomware Combines with Phishing on High-Level Deception Campaign
- A combination of ransomware and phishing campaign is targeting people’s banking credentials.
- The ransomware doesn’t feature strong decryption, as its focus is on social engineering.
- A solution is offered to victims for free by Michael Gillespie, member of the team who discovered it.
As discovered by the “MalwareHunterTeam”, there’s new ransomware out on the wild that sports a hybrid character, combining the usual ransom notes with a phishing page redirection. Victims who go astray from the suggested practice of not giving in to the payment demands of the attackers are quickly corroborating the reason why this remains a bad idea. Not only will they not get their files back, but they also will risk all of their financial assets by giving their banking login credentials away to the malicious parties.
Something new: A ransom note that direct victims to a PayPal phishing page...
Clicking on the Buy Now button, it directs to the credit card part of the phish already (so the login part is skipped). After filling & clicking Agree comes the personal info part & then finished... pic.twitter.com/NR8HEKsC0b— MalwareHunterTeam (@malwrhunterteam) January 9, 2019
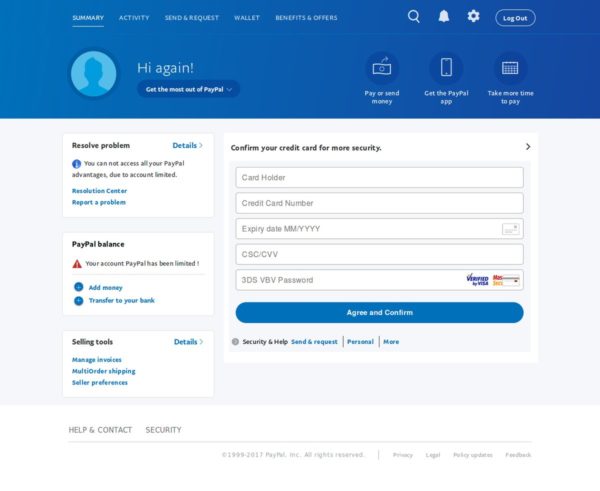
The particular ransomware which dubs as “CryTekk” is locking down the infected systems and encrypts the files contained as usual. Where it differentiates is the payment step, which besides the “standard” cryptocurrency method, also offers a PayPal alternative. The trick is that in reality, it ain’t a legitimate PayPal webpage you are being redirected to, but a phishing page. The phishing page claims that the PayPal account of the victims has been limited for some random reason that happened to occur at the same time they tried to pay the ransom.
This will only trick those who are not familiar with the PayPal interface, as it goes directly to ask for the full credit card details like the holder name, the card number, the CSC/CVV, and all that the attackers will need in order to use it seamlessly. There is no login to PayPal or account creation step at all, which should ring alarms to the victim, but those in panic do not pay much attention to the details.
image source: blog.malwarebytes.com
Once the victim adds all the credit card information, they are urged to “confirm their personal information” (notice the typo right there?), including their DoB, address, phone number, and more. Once this is over, the fake PayPal page displays a bogus message of their account access restoration. This hybrid campaign is no doubt polished from a technical perspective, but where it really shines is the social engineering side of it. $40 is a meager price for getting your files back (less than 10% of the typical), so almost all victims would follow the phishing links and be willing to pay the cost for decryption. Also, the ransom note is warning users that the attackers will extract their data and “use it” if they fail to pay the amount within 14 days, making them feel under threat.
As the encryption used by the particular ransomware isn’t anything special, the experienced decryptor Michael Gillespie cracked it in a couple of hours. If you are a victim, you may contact him directly as he offers help to the victims for free.
Decryptable, victims may contact me for free decryption.
— Michael Gillespie (@demonslay335) January 9, 2019
If you have already given out your banking credentials, however, you should also contact your bank and lock everything down as soon as possible. Next time something like this happens, stay calm and think clearly. That is the solid first step you should be taking.
Any victims of the above? Let us know in the comments below, or just share your thoughts. Also, don’t forget to share this on socials through our own Facebook and Twitter so that others are informed of this hybrid campaign.