RansomHub Surpasses LockBit as Leading Ransomware as a Service Model
- RansomHub Ransomware became a notorious name in recent months, claiming attacks on huge companies and public entities as well.
- Using a RaaS model, the malware managed to compromise over 200 companies in a relatively short time.
- The cybercriminals now use a new business model that involves double extortion tactics.
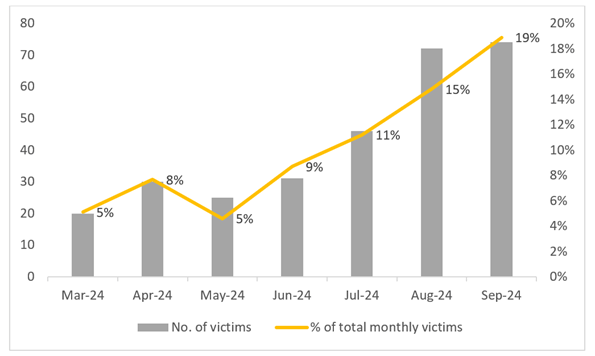
RansomHub has emerged as a dominant force, surpassing the former leader LockBit, following a law enforcement crackdown on the latter. Since its appearance in February, RansomHub has made substantial gains in the ransomware landscape, claiming nearly 19% of all ransomware victims in September 2024, according to a recent security report.
The decline of LockBit, which previously accounted for 40% of ransomware victims in 2022 and 2023, has paved the way for new actors like RansomHub to rise. Its advanced technological capabilities, such as remote encryption, allow affiliates to encrypt local data without local processes, complicating detection and prevention efforts.
RansomHub uses a ransomware-as-a-service (RaaS) model and allows affiliates to launch attacks using its infrastructure. This democratization of cybercrime has enabled the group to infiltrate over 200 organizations by August.
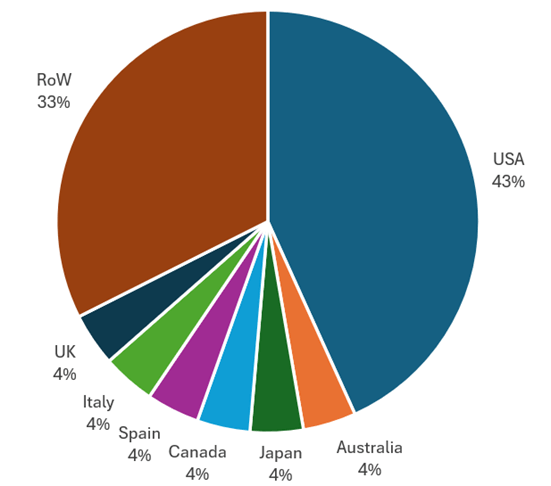
In its extortion efforts, RansomHub employs double extortion tactics, threatening to release encrypted data unless a ransom is paid. Key victims include notable entities like Haliburton and healthcare services but also public entities like libraries, emphasizing the group's wide-reaching impact.
Initially following an encryption-based attack model, Meow ransomware has shifted to focus on data theft and extortion, abandoning encryption for selling stolen data. Victims must choose between paying a ransom to prevent data release or allowing their data to be sold to other cybercriminals.
Reflecting a broader industry trend, Meow's approach avoids encryption risks, focusing on exploiting sensitive information.
Play ransomware ranked second in September 2024 with 43 new victims, primarily targeting U.S.-based companies in manufacturing and consumer goods. Similarly, Qilin ransomware (Agenda) focuses on North American targets, maintaining consistent activity but remaining secondary to RansomHub.
CheckPoint’s September 2024 Ransomware Status Report unveils a rapidly evolving ransomware landscape characterized by increasingly complex and dangerous tactics. With RansomHub's meteoric rise and LockBit's decline, the ransomware ecosystem is undergoing significant shifts, requiring organizations to prioritize data safeguarding over mere breach prevention.
Ransomware has transitioned into an organized, scalable business model via Ransomware-as-a-Service (RaaS). This development allows even low-skilled cybercriminals to launch sophisticated attacks, resulting in a global surge in attack volume. Enterprises now face a formidable threat from a democratized cybercrime marketplace, demanding enhanced vigilance and preparedness.
Groups like Meow have shifted their focus to data theft and extortion, rendering traditional backup strategies insufficient. Stolen data can be sold, causing irreparable reputational and legal harm.
Businesses must, therefore, adopt comprehensive data-loss prevention (DLP) systems, enhanced encryption, and strict access control policies. Leveraging AI-driven threat detection becomes crucial for combating modern ransomware tactics.
LockBit's decline highlights the volatile nature of cybercrime. Although diminished, it has been swiftly replaced by RansomHub, underscoring the need for real-time threat intelligence to anticipate and counter emerging threats effectively.