RansomHub Linked to Play, Medusa, and BianLian Ransomware Groups via Shared EDRKillShifter Use
- RansomHub affiliates have been connected to rival groups Medusa, Play, and BianLian.
- Security researchers discovered that these ransomware gangs share the use of intrusion tools such as EDRKillShifter.
- Recent investigations reveal possible collaborations between the threat actors on top of tool sharing.
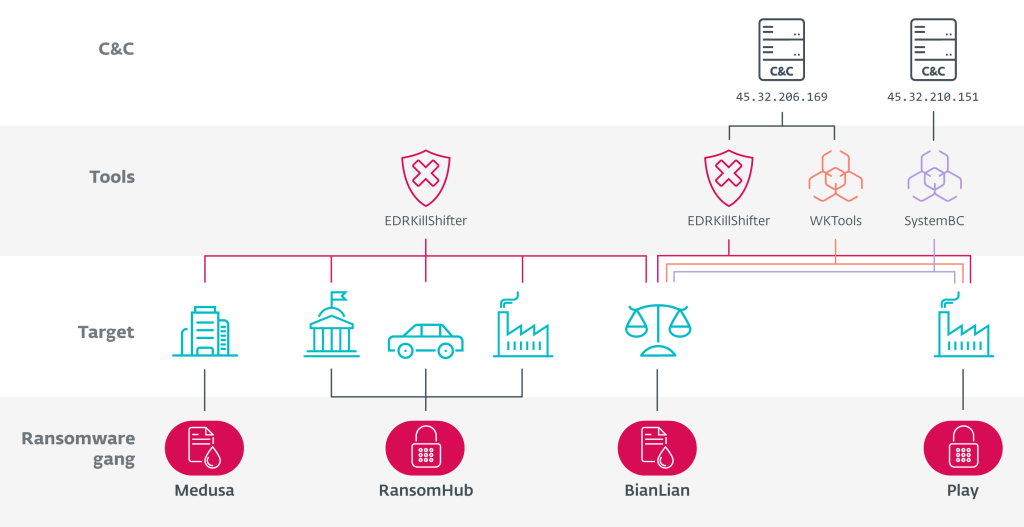
The RansomHub ransomware-as-a-service (RaaS) operation affiliates were linked to established gangs Medusa, BianLian, and Play, which share the use of RansomHub’s custom-developed EDRKillShifter.
One of RansomHub’s standout offerings is this specialized malware developed to disable endpoint detection and response (EDR) systems. This tool provides ransomware operators with a significant advantage by neutralizing security solutions before deploying encryption.
ESET discovered critical overlaps between RansomHub affiliates and rival gangs. A single affiliate, referred to by researchers as "QuadSwitcher," was found deploying RansomHub tools alongside encryptors associated with Play, Medusa Ransomware, and BianLian.
Despite significant differences in these groups' operations, their shared use of RansomHub’s resources highlights surprising collaboration and resource-sharing even among competing ransomware actors.
For instance, QuadSwitcher used identical EDRKillShifter builds in attacks attributed to all four groups. QuadSwitcher also used the commodity malware SystemBC, heavily used by the Play gang.
This discovery suggests not only shared tooling but also collaboration between affiliates operating across multiple ransomware gangs.
EDRKillShifter includes unique safeguards, such as requiring a 64-character password for execution, adding an extra layer of security for affiliates. Unlike most ransomware groups, RansomHub incorporated EDRKillShifter directly into its RaaS program, making it a valuable resource for its affiliates.
EDR killers exploit vulnerabilities in legitimate third-party drivers to disable security mechanisms. Such methods, known as "Bring Your Own Vulnerable Driver" (BYOVD), are increasingly common among ransomware affiliates.
RansomHub, which emerged in early 2024 amidst the collapse of major ransomware groups like LockBit and BlackCat, quickly established itself as a powerhouse. Within months, it surpassed LockBit in victims posted to its dedicated leak sites (DLS).
Many skilled affiliates, including notable operators like Notchy, transitioned to RansomHub, leveraging the vacuum left by decimated groups.
By offering lucrative terms to affiliates, such as a 90% share of collected ransom and a low barrier to entry, RansomHub attracted both experienced and low-skilled operators. However, this inclusivity backfired, as immature operators left trails that proved critical in linking RansomHub's affiliates to rival gangs.