The “Ragnar Locker” Ransomware Is Now Wrapped In Virtual Machines
- The “Ragnar Locker” is using a new way to hide from anti-virus tools and user detection.
- The group is hiding the ransomware executable inside a virtual machine on a stripped-down Windows XP box.
- The ransomware detects and accesses the local and network drives of the system, exfiltrates, and encrypts them.
There are many ways through which threat actors try to avoid detection, namely by encrypting their executables or C2 communications, using something innocuous to fetch the malicious payload, using stolen code-signing certificates, or even by hiding the malware inside virtual machines. The group behind the “Ragnar Locker” ransomware strain went for the latter choice lately. According to a report by Sophos, the actors are using an Oracle VirtualBox Windows XP virtual machine to conceal the Ragnar Locker executable.
Source: Sophos
Ragnar Locker is the ransomware group that set the trend of stealing data from the compromised networks before they lock down the files locally. They recently targeted the “Energias de Portugal” electric and gas energy provider, stealing approximately 10 terabytes of sensitive data to use for continuous extortion. Ragnar Locker demanded ransom, in this case, was a pretty hefty 1,580 Bitcoin ($14.3 million). That said, we’re talking about a ransomware group that is defining the developments in the field, so the deployment of virtual boxes inside which ransomware executables are hiding may find imitation across the domain. After all, these adversaries are going for the top level, so no technique that opens the way to success is considered unorthodox.
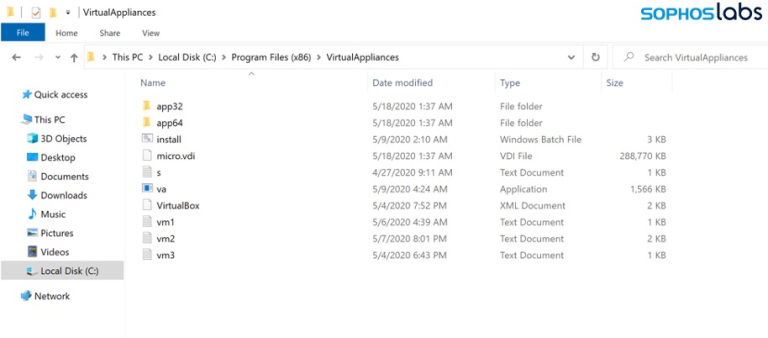
Sophos detected Ragnar Locker infections that use an unsigned MSI package of 122 MB of size and contain an old VirtualBox hypervisor (v3.0.4). The virtual disk image that hides inside the machine is a stripped-down Windows XP SP3, named “MicroXP v0.82” - in there hides a 49 kB Ragnar Locker executable. The virtual image is copied to “C:\Program Files (x86)\VirtualAppliances,” and, through a series of script executions, it disables the Windows AutoPlay notifications to make the loading of the virtual box in a virtual drive silent. The virtual machine is configured to use 256 MB of RAM, and one CPU core, so the user most likely won’t notice that something is running on the background.
Source: Sophos
After enumerating the disks in the system and mapping the network drives on the physical machine, everything is configured to be accessible from within the virtual machine - as this is a requirement for the encryption. Another script is deleting the shadow copies in the target system to make impossible the restoration of the files to a previous (unencrypted) state. Since everything runs from the virtual machine, any anti-virus or anti-malware tools running on the system will not detect and stop anything, so the malicious actions can revel unhindered.