Radar/Dispossessor Ransomware Gang Servers Seized by International Operation
- An international law enforcement operation seized several servers and domains of the notorious Radar/Dispossessor ransomware group.
- The investigation uncovered 43 companies outside the U.S. that had fallen victim to the cybercriminal gang.
- Among the seized domains are two criminal websites, one with fake news and another with videos.
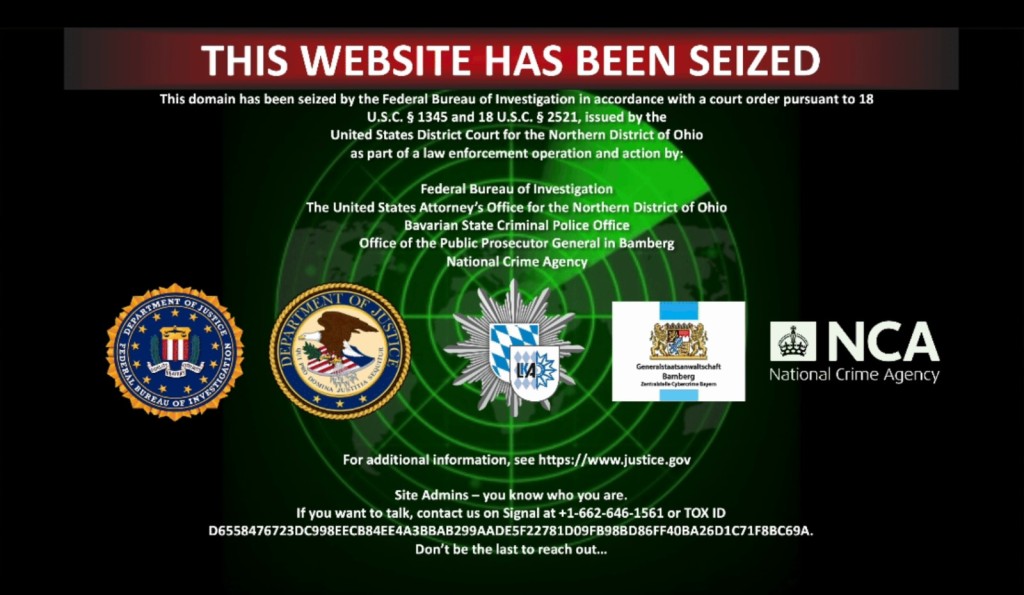
In a joint international operation, the FBI disrupted the Radar/Dispossessor ransomware led by the online moniker "Brain,” as per the FBI’s official press release. During its investigation, the FBI identified several criminal websites linked to the individual and their team and seized 24 servers and 9 domains worldwide.
The operation dismantled 18 German, three U.S., and three U.K. servers and took down one German-based and eight U.S.-based criminal domains, including a fake news site and a criminal video site.
Radar/Dispossessor debuted in August 2023 and quickly became an internationally impactful ransomware group that encrypted and extorted small- to mid-sized businesses and organizations in the production, development, education, healthcare, financial services, and transportation sectors.
The press release said among the victims are 43 companies from countries including the U.K., Canada, Australia, Argentina, Brazil, Peru, Honduras, India, Germany, Belgium, Croatia, Poland, and the UAE, besides the U.S. victim entities.
The ransomware gang exploited vulnerable computer systems, weak passwords, and a lack of two-factor authentication (2FA) to infiltrate the victims’ network and obtain administrator rights to the files, then claimed the data theft on the group’s leak website.
The threat actor did not stop at the double extortion practice but also moved further to triple extortion, calling or emailing other members of the victim company or their customers. The emails also included links to video platforms presenting their stolen files.
The investigation and joint takedown were conducted in conjunction with the U.K.'s National Crime Agency, the U.S. Attorney’s Office for the Northern District of Ohio, the Bamberg Public Prosecutor’s Office, and the Bavarian State Criminal Police Office (BLKA).
In June, international efforts led to the arrest of a 28-year-old hacker connected to Conti and LockBit ransomware in Ukraine. This was part of Operation Endgame, an internationally coordinated operation against botnets that targeted the cyberinfrastructure used for malware, leading to four arrests and more than 100 Internet servers seized.
Law enforcement shut down LockBit's infrastructure in February 2024 in Operation Cronos, seizing several servers with decryption keys.