Raccoon’s Info-Stealer “Malware-as-a-Service” Is Getting More Popular
- Threat actors are turning their attention to the Raccoon stealer, making the MaaS gradually more popular.
- There’s already a sizeable community around Raccoon and a noteworthy customer support service.
- Raccoon features basic info-stealing features, but it's easy to use and versatile when it comes to its delivery methods.
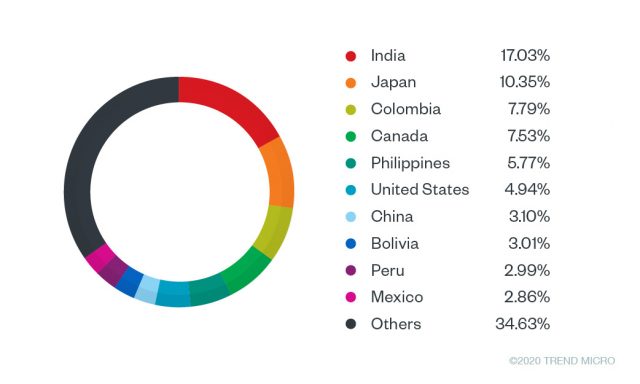
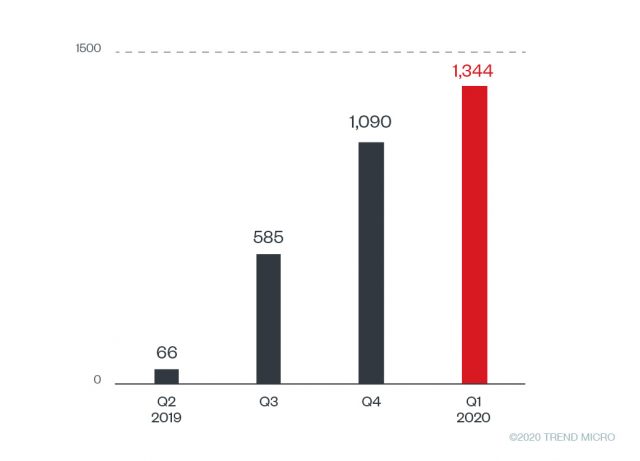
Trend Micro’s researchers are steering the spotlight to Raccoon, a "malware as a service" (MaaS) that has been growing steadily since April 2019, when it first emerged in the wild. The telemetry data is showing an increase in the number of unique Raccoon samples, reaching the record-breaking figure of 1,344 in Q1 2020. As for the number of Raccoon infections, the total recorded events since April 2019 have surpassed 100,000 - with India, Japan, Colombia, Canada, the Philippines, and the United States being the most targeted countries.
Source: Trend Micro Blog
Source: Trend Micro Blog
The raccoon is a pretty capable and dangerous malware that is sold to malicious actors at a relatively low price, ranging between $75 and $200 per month. Actors distribute the malware via exploit kits, phishing messages, or as a payload fetched by other malware strains. Trend Micro reports about the Fallout and Rig exploit kits in particular, which are very often used in conjunction with the Raccoon malware. Raccoon also connects to Google Drive URLs to decrypt its C2 server and to maintain a level of evasion from detection systems.
Right now, 67 unique IP addresses serve as C&C for the various Raccoon operations, while the researchers report that some originate from Lithuania. The servers provide the executable binaries, as well as the libraries required for the info-stealing process. As for what Raccoon can do to the infected system, it can steal login credentials, credit card information, cryptocurrency wallets, browser cookies, and more. The malware isn’t particularly sophisticated, but it is versatile enough to make up for what it lacks in features. The following strings indicate what browsers Raccoon supports and what information can be exfiltrated from them.

Source: Trend Micro Blog
Finally, the particular MaaS is very active in terms of customer support, providing valuable help to the malicious actors who are subscribing to the service. The team behind Raccoon offers easy-to-understand technical guidance and dumbed-down information on how to make a quick buck using the malware. As the community around it is continually growing, we expect to see Raccoon becoming more relevant and popular as we move deeper in 2020. The malware may get more powerful in the next months, fixing bugs, and enriching its features. For a full list of the current indicators of compromise and the server URLs, check out Trend Micro’s detailed report.