‘Raccoon Stealer’ Now Comes With a Crypto-Transaction Grabber and a Malware Dropper
- ‘Raccoon Stealer’, one of the most popular MaaS platforms now gives clients the ability to drop additional malware.
- Most notably, actors can now steal cryptocurrency transactions and also drop miners onto the victim’s machine.
- In typical deployment cases, the return from using Raccoon is nine times its renting cost.
The authors of ‘Raccoon Stealer’ malware-as-a-service (MaaS) have upgraded their tool with the capability to steal crypto-currency transactions from the infected machine, as well as a new dropper that can fetch additional malware payloads. Raccoon Stealer is sold as a commodity malware to anyone interested for $75 to $200 per month and has risen in popularity since last year. Researchers at Sophos have recently noticed a new version circulating in the wild, which has re-sparked the interest of cybercriminals in the particular malware platform.
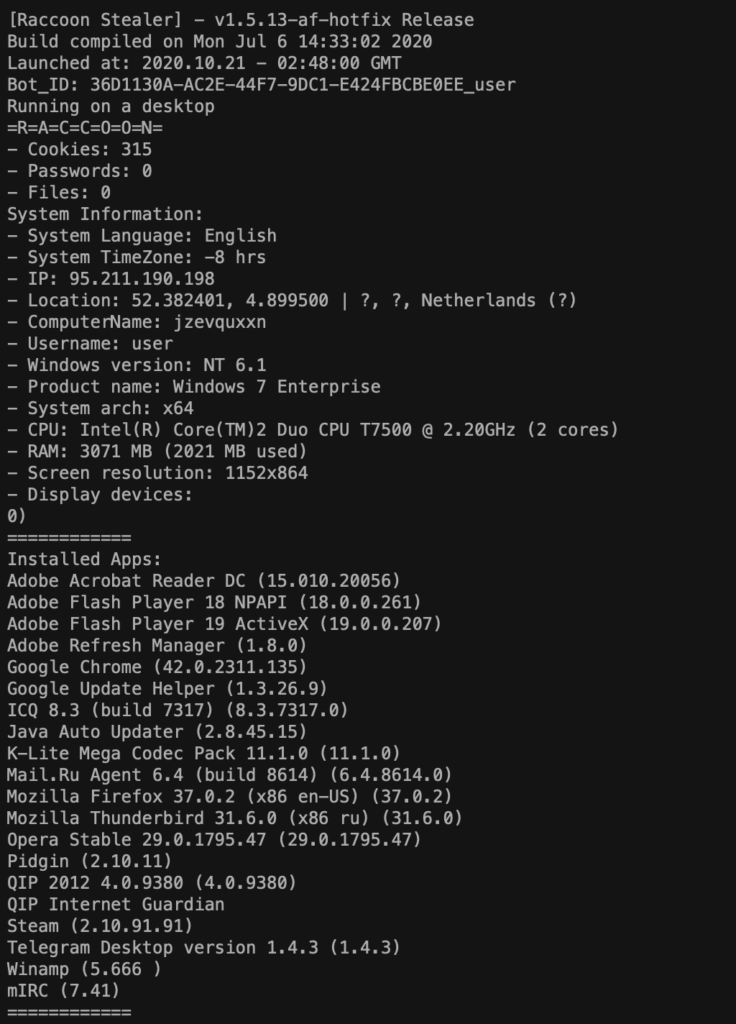
Raccoon can currently collect user passwords, browser cookies, the “autofill” text entered on website forms, and anything that comes through, such as credit card details, or names, or email addresses. And now, cryptocurrency wallets and transactions are also being targeted, thanks to a new clipper component. In the latest minor release (v1.7.4), the author fixed log-collection issues and made the exfiltration less problematic in general.
The developers of Raccoon assign a different signature on each executable of the malware they rent to customers, so if someone leaks it anywhere, they can trace back the culprit client and ban them. These tools are used by huge numbers of low-grade hackers as they are relatively cheap and pretty effective in what they can do. Also, they are generally deployed in low-risk operations, and most cybercriminals prefer these as they come with fewer chances of finding trouble with law enforcement.
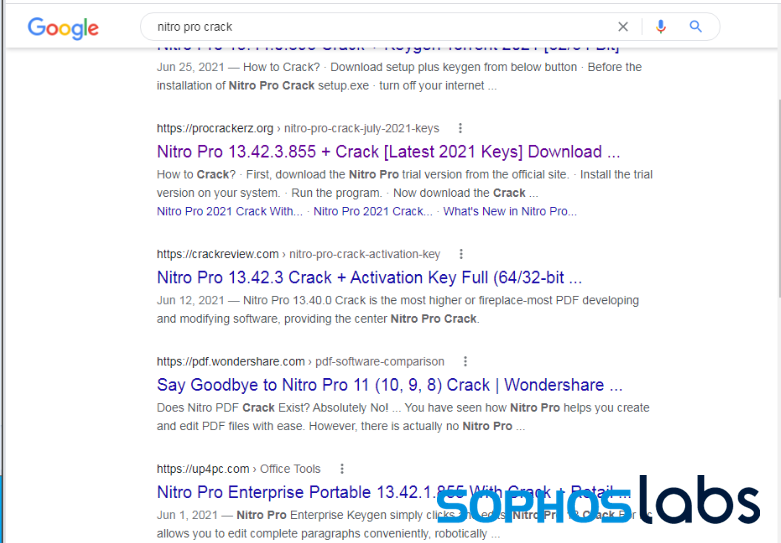
The most common way of distribution is via spam email that comes with a laced document. The second most popular way of spreading Raccoon is through websites that supposedly offer a torrent to download pirated software. The sites used for these campaigns are SEO-optimized so that Google Search includes them on the first page of the results.
Downloading anything from these websites gets you a password-protected folder with a self-extracting installer, usually a 7zip or WinZip file. By using the new malware dropper function, the actors now fetch the following in addition to the Raccoon Stealer:
- crypto-miners
- “clippers” (malware that steals cryptocurrencies by modifying the victim’s system clipboard during transactions and changing the destination wallet)
- malicious browser extensions
- YouTube click-fraud bots
- Djvu/Stop (a ransomware targeted primarily at home users)
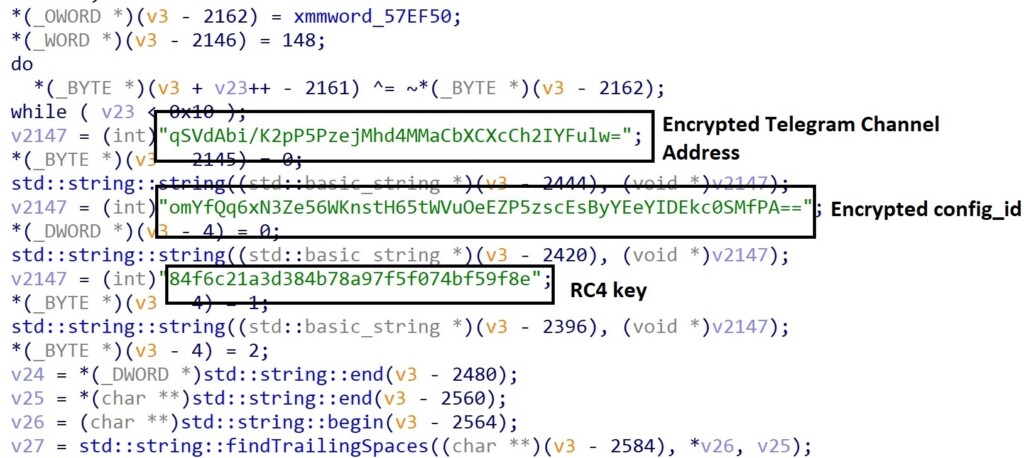
Another new element in the recent Raccoon iteration is the use of Telegram channels for the communication between the stealer and the C2 gateway. The connection is encrypted for obfuscation and detection avoidance.
Sophos analyzed some BTC wallet addresses used in the spotted campaign as the deposit points for the stolen crypto and found a total of $14,200 in them. It is estimated that through the deployment of crypto-miners that run on the victims’ systems, the same actors made another $2,900 over a six-month period. The cost for renting Raccoon for six months is $1,200 max, so the actors made at least $16k, or $2,650 per month.