Python NodeStealer Adopts New Techniques to Target Facebook Ads Manager
- Novel NodeStealer variants leverage Microsoft-signed binaries to avoid detection in a Facebook Ads Manager campaign.
- Expanded functionality allows the collection of credit card information and employs access token Generation and Graph API exploitation, among others.
- Attackers use credentials and cookies stolen from victims' browsers to access Facebook Ads Manager accounts.
The Python NodeStealer malware targeting Facebook business accounts for over a year has new variants that introduce advanced techniques to extract sensitive information more effectively, specifically focusing on Facebook Ads Manager accounts and credit card details.
These NodeStealer variants extract Facebook Ads Manager account details, such as budgets and business information, likely for use in creating malicious Facebook ads, according to a recent Netskope Threat Labs security report.
Expanded functionality allows the collection of credit card information stored in browser databases, including cardholder name, expiration date, and card number.
Windows Restart Manager unlocks browser database files for data extraction, leveraging Microsoft-signed binaries to avoid detection, and a junk code is added to inflate the script with redundant code to bypass small-file analysis tools.
The malware generates and executes the Python script directly from within a batch file, making detection more complex. Its new persistence mechanisms utilize registry run keys, replacing the previous reliance on startup folder entries.
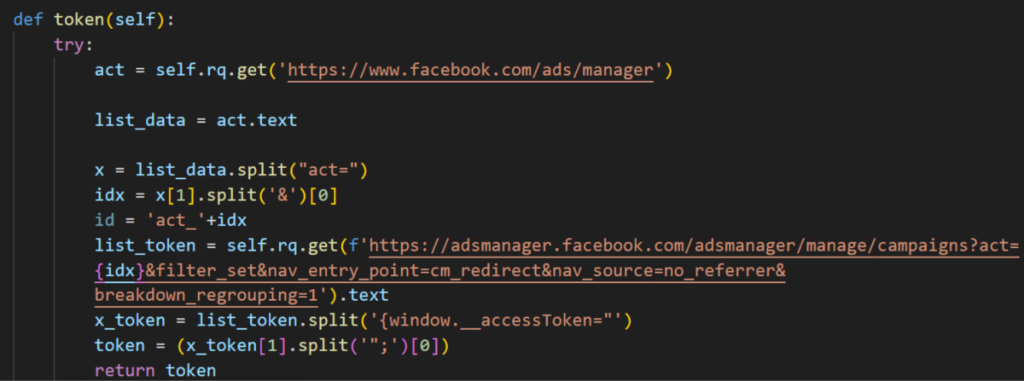
The new variants have been observed targeting Facebook Ads Manager accounts via credentials and cookies stolen from victims' browsers and then using the generated access token to gather detailed business and ad account information via Facebook's Graph API. The extracted data is saved locally in “data.txt” files before exfiltration.
The attackers behind NodeStealer appear to be Vietnamese-speaking and intentionally avoid targeting victims in Vietnam, likely to evade local law enforcement. The malware checks IP-based country codes and exits if the victim’s location is Vietnam.
Credit card theft is achieved by targeting the “Web Data” SQLite database files of browsers, which store payment and autofill information. By unlocking these files using the Restart Manager and querying them with Python's SQLite3 module, NodeStealer retrieves sensitive payment details with precision.
By targeting ad account budgets and credit card details, attackers can exploit stolen access to run malicious ad campaigns and siphon funds directly.
Enterprises should prioritize securing browser-stored credentials and implement robust malware detection capable of identifying LOLBins-based activity, such as the illicit use of Windows Restart Manager.
In other news, an ongoing malvertising campaign distributes the SYS01 InfoStealer via Facebook ads impersonating several popular brands to distribute the malware, including ExpressVPN, Telegram, and Netflix. The hackers collect credentials of Facebook Business accounts to place malicious ads and sell these on the dark web.