Pulse Secure Urges ‘Connect Secure’ VPN Users to Patch Immediately
- Pulse Secure has discovered three more vulnerabilities in its VPN product, and patches are already out.
- The vendor is also offering mitigation in the form of an XML configuration file, but it’s not the perfect solution.
- Sophisticated threat actors will continue to target Pulse Secure products, so patching as soon as possible is critical.
Pulse Secure has released an out-of-cycle advisory to warn users of the need to patch their ‘Pulse Connect Secure’ product immediately, as the latest available update (version 9.1 R11.4) addresses three critical and one high-severity vulnerability. The flaws include problems like remote arbitrary file execution, buffer overflow leading to root-level RCEs, and unrestricted uploads from authenticated admins. The four flaws are tracked as CVE-2021-22893 (CVSS v3.1 score: 10), CVE-2021-22894 (CVSS v3.1 score: 9.9), CVE-2021-22899 (CVSS v3.1 score: 9.9), and CVE-2021-22900 (CVSS v3.1 score: 7.2).
According to the relevant advisory, the following product versions are affected:
- PCS 9.0 R3/9.1 R1 and Higher – vulnerable to CVE-2021-22893
- PCS: 9.1 Rx and 9.0 Rx – vulnerable to CVE-2021-22894
- PCS: 9.1 Rx and 9.0 Rx – vulnerable to CVE-2021-22899
- PCS: 9.1 Rx and 9.0 Rx – vulnerable to CVE-2021-22900
The recommendation is to move quickly to patch these flaws as the Pulse Connect Secure is a product that is constantly being under attack by sophisticated state-supported actors, among others. The Pulse Secure team worked closely with CISA (Cybersecurity and Infrastructure Security Agency) and FireEye to identify the flaws and responded with a roll-out of a fixing patch as soon as possible.
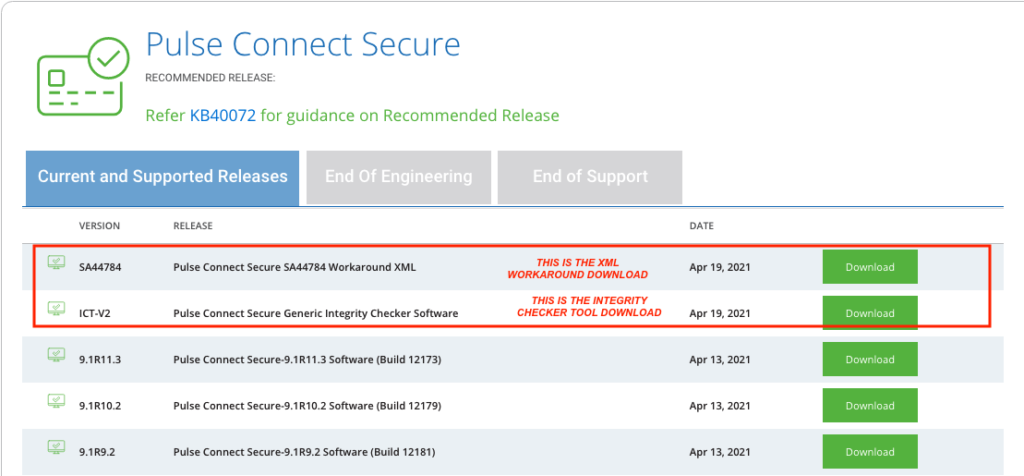
For those who cannot apply the patch for whatever reason, there’s a mitigation for CVE-2021-22893, CVE-2021-22894, CVE-2021-22899, which can be implemented by importing the “Workaround-2104.xml” provided by the software vendor. This file disables the Windows File Share browser and the Pulse Secure Collaboration, so it won’t be of any use if you need these. Even if you implement the mitigation, you are still advised to move to 9.1 R11.4 as soon as this becomes possible.
If you are running any version below 9.1 R9, the workaround XML won’t make any difference. In that case, Pulse Secure recommends upgrading to at least 9.1 R19, ideally to 9.1 R10. Finally, if you are using A/A or A/P Cluster, the cluster will sync the configuration of the XML between nodes, so there’s no need to import the file individually on each node.
In addition to patching or at least applying the suggested mitigation, Pulse Secure also urges users to deploy its ‘Integrity Checker Tool,’ which will provide an easy and automated way to figure out if there’s malicious activity on their systems. If you are using Pulse Secure products, make sure to check the vendor’s update portal regularly, as the game of cat and mouse between security researchers and malicious actors is not expected to end any time soon.