‘Prophet Spider’ Now Targeting Old Oracle WebLogic RCE Vulnerabilities
- Hacking group ‘Prophet Spider’ is exploiting last year’s WebLogic RCEs to gain access to corporate networks.
- The actors then sell this access to other adversaries, mostly ransomware operators.
- The initial access market has been on the rise for quite some time now, having exploded in 2021.
‘Prophet Spider’, a sophisticated actor that has been around since at least May 2017, is now exploiting CVE-2020-14882 and CVE-2020-14750, two remote code execution (RCE) flaws on Oracle WebLogic. As detailed in a report by Crowdstrike, the actors are mostly interested in gaining access to the target’s environment and then selling that access to other groups of hackers, like ransomware actors for example. In its recent campaign, ‘Prophet Spider’ demonstrates expertise in targeting both Linux and Windows operating systems, which gives them versatility and potential.
The actor is exploiting the two WebLogic CVEs to access the administrative console and then run code remotely. While the two aforementioned flaws are the most commonly exploited by ‘Prophet Spider’, they’re not the only ones. In some cases, the hackers went for CVE-2016-0545, which allowed them to perform SQL injection to gain access. In general, though, there is no phishing, malvertising, or credentials brute-forcing involved in these recent operations, so the actors are relying solely upon exploiting unpatched vulnerabilities.
After they gain a foothold onto the target’s network, ‘Prophet Spider’ moves laterally using ‘ping’ and ‘nslookup’ commands, while they also use ‘pscan’ to scan the environment for Windows systems by listening on port 445. Once they finish their reconnaissance and establish persistence, the actors delete their tools using ‘rm’, exfiltrate whatever they find interesting through FTP or PSCP, and then contact other adversaries to sell web shell access.
While the scenario of ‘Prophet Spider’ deploying ransomware payloads themselves cannot be ruled out with absolute certainty, CrowdStrike Intelligence believes they are most probably functioning as access brokers. This is supported by the fact that in at least two recorded infection incidents, the ransomware strains used were different (Egregor and MountLocker), so ‘Prophet Spider’ must have sold access to these groups.
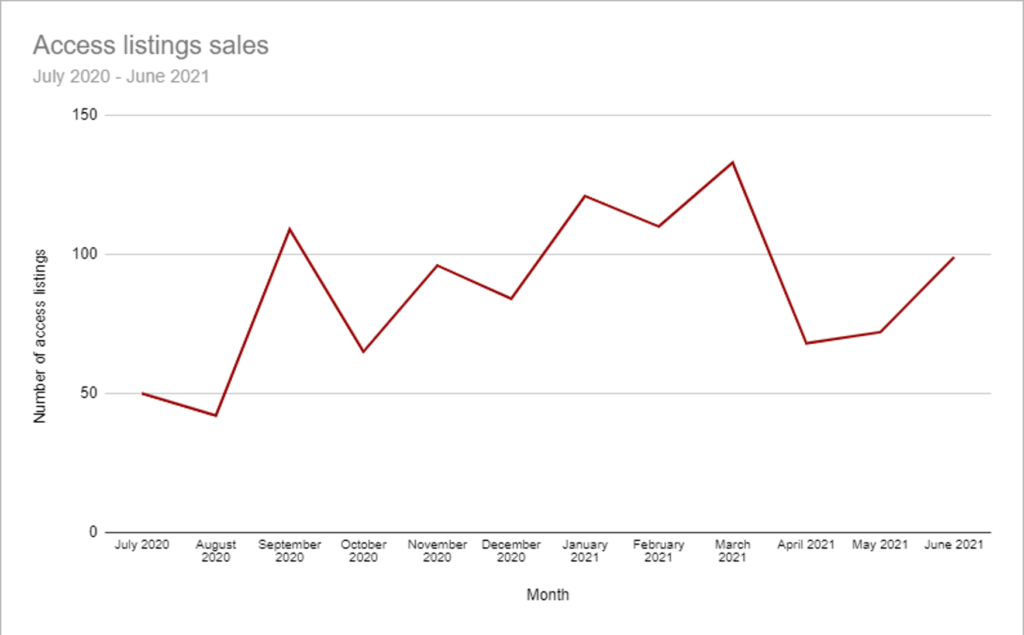
The market of initial access brokers has been on the rise for quite some time now, so opportunistic actors like ‘Prophet Spider’ are finding the field profitable and relatively easy to move into. A recent report from Positive Technologies has recorded an increase of roughly 20% in network access listings in Q1 2021 compared to all entries posted in 2020, so the field is exploding.
A similar report by KELA that came out a few days back paints the same picture, with an ostensible decline in spring being attributed to the sellers negotiating their offerings privately following the high-profile ransomware incidents that raised the law enforcement heat at that time.